Understanding SaaS Applications and Implementing Advanced Security Controls to Protect It
In today’s SaaS market, we can see that security is an ideal concern. Compared to the last few years, there’s been a fundamental change in how businesses operate, and customers have already adopted the changes. As a result, building strong credibility is Catch-22. According to a CyberArk survey of corporate decision-makers and IT, 70% of respondents did not prioritize security. In addition, 56% of respondents said there are confidentiality and integrity issues because they do not care about protecting it. We’ve compiled some basic information like the importance of SaaS, threats against SaaS applications, and best practices on SaaS application security. Let’s dive in!
What is SaaS Application?
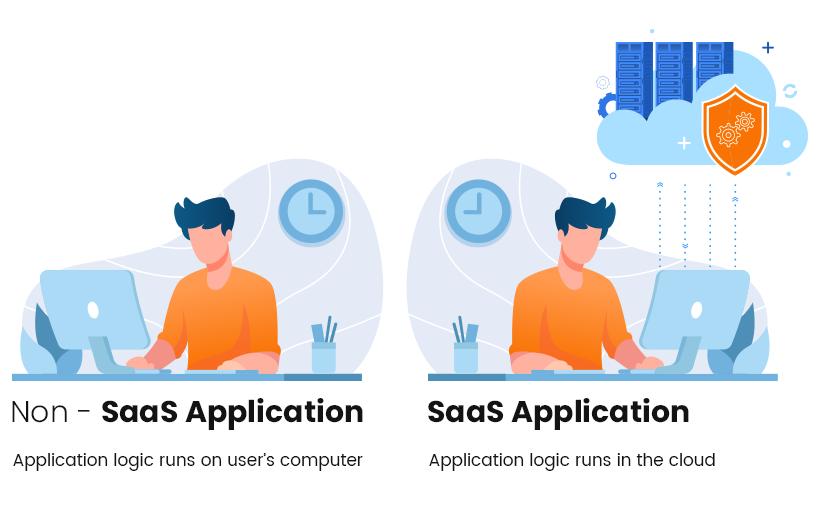
Software-as-a-Service is an on-demand or cloud-based method of providing software to users. SaaS application users subscribe to an application rather than purchasing it once and installing it. Further, users can log into and use a SaaS application from any device over the internet. The provider has access to the application including servers, databases, security, storage facilities, and performance. These services can be availed through a subscription process where payment is made only for the required services.
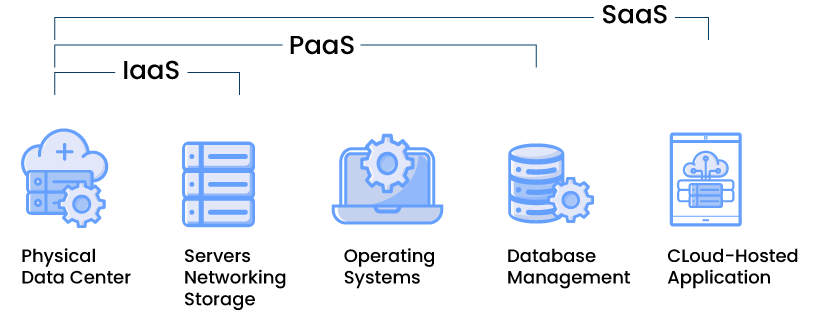
SaaS is made of cloud products such as Infrastructure as a Service (IaaS) and Platform as a Service (PaaS):
IaaS – It is a cloud infrastructure and doesn’t include applications.
PaaS – It is a cloud-based OS and data storage tool.
SaaS – Add apps to these functions.
There are many differences between traditional applications and SaaS applications. They are as follows.
| Traditional Applications | SaaS Applications | |
|---|---|---|
| Customization | Flexible in terms of customization | Limited to customization |
| Installation | Need to install and maintain software | Doesn’t require installation |
| Pricing | Expensive as user need to purchase license for each user | Cost-effective due to timely subscription |
| Data Ownership | Can own data | Can’t own data |
| Free Trial | Free trial not available | Free trial often available |
| Updates | Some updates are automatic | All updates are automatic |
The simplicity and affordability of cloud-based or on-demand software development can lead to overlooking security concerns. Do not fall into the same trap. Whether you are ditching on-demand software for a SaaS offering or growing a cloud-based business, security should be a top priority. With SaaS in high demand these days, the rise of security threats has become a major concern. Moreover, cyber actors are actively looking for less secure applications to attack and bypass security. Therefore, it is important for any organization using SaaS applications to think about security and ensure that they are not compromised.
Features of SaaS Applications
- The SaaS model is like the Application Service Provider (ASP) working with on-demand computing software services. Here, the vendor hosts the software and makes it available to users through the internet.
- In this cloud-based architecture, a single platform is shared by both the users and the software applications.
- SaaS is a multitenant architecture where users and applications have a single, shared infrastructure and codebase. So, it is easy to maintain it. Therefore, it will help vendors to reduce the development time.
- The other important feature of SaaS is its customization capability. The user can easily customize the SaaS depending on their business needs. Hence it reduces the adoption cost for the user.
- It has an advanced feature in accessing data; users can access data from any networked devices and simultaneously monitor privileges and manage data usage.
- The interface of the SaaS application is more straightforward, like websites, so it is easy for the user to understand. You can also customize SaaS with point-and-click ease.
- The SaaS has a flexible payment method in which the user does not need to buy software or hardware. It is entirely cloud-based; the user will only have recurring costs and zero transitioning costs. In addition, the user can un-subscribe to SaaS at any time to cut the recurring cost.
- The user can ask the SaaS provider to update the platform automatically. It will help reduce the pain of internal IT staff by purchasing new software and configuring it.
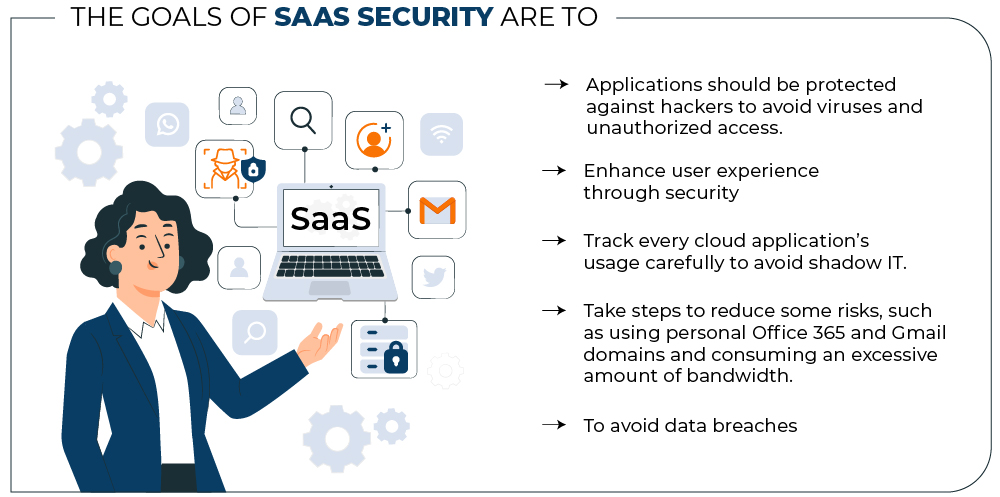
What is SaaS Security?
We now know what it takes to compromise your SaaS applicationdata security. Today, organizations rely heavily on SaaS applications used by multiple users on multiple devices for their daily operations. As a result, there is a high likelihood that your users’ privacy and the security of your corporate data are at risk. We believe that it is the responsibility of the provider to manage the security of cloud applications, which includes various vectors such as platform, network, applications, OS, and infrastructure. Now, before we delve into the SaaS threat landscape, let us take a look at why SaaS security is so important.
Why is SaaS Security Important?
Even though the SaaS provider offers a wide range of security options that can be opted for by the users, the clients play a huge role in managing the security of the organizational data and the user access. Nowadays, cloud applications are prone to various cyber threats such as malware attacks, phishing emails, ransomware, and more. Therefore, despite enhancing the development and usage of customized software, the SaaS applications have also created new security threats that affect user access and sensitive business data.
- SaaS products have a huge market, and there is a lot of sensitive data available that can be easily compromised by threat actors. As a result, hackers are attracted to data such as personally identifiable information and payment card information, which is why the security of SaaS is crucial to avoid any difficulties in the form of data breaches.
- SaaS providers only take care of the platform, apps, operating system, and infrastructure. However, they do not secure customer data. This means that you need to handle the security of your SaaS stack, which you can do by implementing security practices.
- 51% had experienced a ransomware attack targeting their SaaS data, and 52% of those attacks were successful.
Understanding the need of SaaS security
Should restrict the access of critical resources to privileged authorities based on their designation and needs. Data sharing has become simple and less time-consuming with the SaaS applications in use. In addition, the connectivity has increased due to the usage of cloud-based applications, increasing the possibility of a data breach.
As the SaaS applications are provided by the ISV (Independent Software Vendor), who may also be hosting the cloud platforms, securing the applications does not entirely fall under the service provider. As a result, it creates a loophole in the security of the SaaS applications, which can be fixed by sharing the responsibility, where the service provider secures the software. In contrast, the concerned organizations themselves secure user access and data.
The SaaS model facilitates administrative access from anywhere across the globe, which opens a new portal for hackers to attack the organization’s network. As more SaaS applications are used in the business world, the probability of error in the application is high. It is up to the cyber-security teams to find the threats and prevent any issues from the user side.
There is a possibility that the customer data could be stored in a different geographical location from the company. It becomes difficult to secure the data in other geographical solutions when the data security laws are different.
It clarifies that securing the SaaS applications is of paramount importance to safeguard the business functions that rely on them.
The Growing Threat Landscape of SaaS
A recent study has shown that almost 40% of all SaaS data is unmanaged and prone to cyber-attacks. Internal, external, or public users can easily access unsupervised data. Recent changes in the business environment have mandated many companies to adopt SaaS applications to use its adaptive features and easy accessibility. As the SaaS applications are cloud-based, we can access them from any part of the world irrespective of the location. Due to the Covid-19 pandemic, the companies were forced to perform critical operations from remote locations, increasing cyber-attacks and data breaches.
A recent report states that the global SaaS applications revenue will be expected to reach 195 billion U.S. dollars in 2023. Expansion in the implementation landscape of the SaaS model has also enhanced the scope of future threats. The remote usage of SaaS applications allowed access to critical data, increasing the difficulty in managing the data and making it hard to track access to such resources. It is also possible that multiple SaaS applications could integrate to share the data, resulting in a data breach when it goes unmanaged. Therefore, an organization should take measures to secure the SaaS applications as follows.
SaaS Security – Challenges & Risks
SaaS development and implementation are not easy as it seems. The biggest challenges of SaaS are as follows.
-
Visibility
The companies mostly use over 200 SaaS applications. Each one will be different, making it too difficult to track an IT team. But the crucial problem is the lack of knowledge about the application and its capabilities.
Due to this overload, IT could not put their requirement when the department purchases a new SaaS product because it is decentralized. As a result, each department will purchase its SaaS as and when required, which leads to a lack of IT intel stemming from the shadow IT.
For example, the company may buy or place an order for an application that the department already has a similar one. The best way for the organization is to let IT negotiate an enterprise plan with the vendor.
-
Problem in Integration
If the application is not properly integrated, this can lead to numerous problems. Suppose the accounting and sales data are not properly synchronized with the CRM system, and the user is constantly updating changes and uploading files to the various systems. In this case, the system can work incorrectly throughout the company. This results in incorrect invoices being created and sent to the wrong recipients.
-
Performance Issues
If the SaaS users are far from the data centers may face latency and performance issues if an organization does not have a broad cloud strategy. And those who purchased SaaS without proper consultation will end up wasting more money and managing data poorly, which means even more work and IT hours.
-
Time Constraints
The transition from on-premises to the cloud will take some time, which will impact the company’s business operations and revenue. Therefore, the transition to the cloud is usually done in a hurry to get the application and services up and running. Therefore, businesses need to plan carefully to avoid disruption of services.
-
Access Control
Another major challenge an enterprise will face while transitioning into the cloud is access control. Usually, the admin will control all the access, but they might also lose track of it during transition time. If you move from traditional software to a SaaS solution, the access transition will not be that smooth.
-
Budgeting
When it comes to budgeting for a SaaS subscription, the IT and procurement team should be more careful and have proper knowledge and understanding of the application. It will lead to poor budgeting, and the company will unnecessarily spend more money.
Companies will overspend on the SaaS application than they need due to unnecessary tools that are auto-renewed or poor negotiation with the software vendors. If this happens, the company will prevent itself from investing in the necessary application, especially important for business growth. So, IT must help the company make the proper budget, leading to a worthwhile investment and improving the business revenue.
-
Vendor Management
Managing more applications lets enterprises deal with more vendors, contracts, and renewals. However, it makes the team busy in their full-time job, and it can lead them to lose track of the application’s subscription.
So, an organization needs to have a proper system to organize contracts, renewal dates, and mission-critical details. If a company does not have that, it may risk subscribing to unwanted software.
-
Security Risk
Before subscribing to the SaaS while sending a requirement to the IT team, the primary concern will be the risk associated with the application. So, the IT teams must check the SaaS application compliances and the SaaS provider reputations before subscribing to it. Because the IT team allows a single unsecure application or unauthorized access into their network, it will lead to cyber criminals. It could vanish their sensitive data, spoiling the company’s reputation and leading to loss of business. It is why IT teams should work hard before purchasing or subscribing to any application for their organization.
Another critical risk the organization faces when transitioning to cloud-based services is data security. Recent research shows that 66% of people use the same password for most of their accounts. Furthermore, many of them use a simple password like 123456, which means if a provider gets hacked, the chances are bright that the providers’ customers can also be hacked and steal their data.
It is one of the severe threats for the organization to overcome. Therefore, businesses take various security measures, like implementing two-step authentication and encrypting the storage and transmission of data.
-
High Integration Cost
Regular IT resources cannot do SaaS integration. It requires highly skilled professional resources for which the company has to spend some extra money which is a high cost. The company has to hire an external resource for this job. The best way to cut down on cost would be to select a suitable service company that provides seamless integration with all other systems in the company, which should preferably come with an open API.
-
Hyper-Specialization
Most SaaS service providers say that they offer all-in-one solutions for their customers. Still, the SaaS solution improves the application only in one or two things. So, the company has to approach multiple solutions for different purposes. It is a burden for a company, leading to hyper-specialization. So, the company needs to make sure the solutions they are planning to use are playing well.
-
In Proper Attention to SLA
The SLA (Service Level Agreement) is a document that provides the terms agreed upon by both the company and SaaS provider. It will have what to expect from the SaaS provider and the action plan if something goes wrong. If a business is not aware of what they have agreed, it can lead to a relationship issue between the provider and the business in the long term. So, a business needs to check the SLA and understand that clearly by both parties to maintain a good relationship between them. A long-term relationship will always give a profitable business for both parties. It is a Win-Win deal for them.
-
Upgrades Issue
You should always keep data as your main priority when you decide to upgrade the application. Now, this is the age of auto-renewals. Therefore, you have to be careful; otherwise, due to upgrades, you may be in issues. If you have to protect the data, ensure you have user insight to monitor the upgrades.
How to Secure SaaS Applications – Best Practices
It’s tempting to think about the security of SaaS and user access to the Internet. But if we take a closer look, the security of SaaS usage is much more difficult than it seems. The fact is that there is no universal security checklist that ensures the highest level of security. That’s why, with the help of cybersecurity experts, we have compiled the best security practices for securing SaaS applications.
Planning A Security Strategy
The first step in securing the SaaS applications is to create a well-researched plan. Finding out the cloud applications’ vulnerabilities will help design a security strategy. However, without knowing the critical resources to be protected, it is not easy to secure the data in the SaaS platform. Therefore, it is essential to analyse a few factors before initiating the SaaS model business, including the need for SaaS, business-critical data, best service provider, vendor security, and knowledge of cyber-security teams.
Using Cryptographic Technology
Cryptography encrypts the standard text into ciphertext by assigning it with different variables. It is one of the oldest and a more efficient ways to protect data from being stolen by hackers. It means that even when the hacker extracts the data, it will be meaningless until it is decrypted using the right key. More SaaS applications use Transport Layer Security (TLS) for secured communication. This technique can also secure stored data that the vendors should provide.
Authentication Management
Authentication is a security process that ensures the safety of data and application from unauthorized access. Multi-factor authentication is the most efficient method where more than two factors are enabled to access the critical resources. For example, in addition to the traditional factors such as user id and password, the latest factors such as verification code biometric scanning are required to gain access to the data. This method prevents hackers from gaining access through social engineering hacks.
Limited Access
Unlimited access to unmanaged resources can pose a more significant threat to data security. An organization can avoid it by limiting the number of persons who can access the resource and should grant access based on the requirement. The main aim of this concept is to give the proper access to the right person at the right time. In addition, limiting access makes it easy to log the access details and changes to the data.
Control Over the Network
It is indispensable for an organization to have control over its network. First, it helps to identify the cyber-attacks in the earlier stage. It helps to manage the access instances across the network. Additional security features such as Network Access Control List (NaCl) can function as a firewall that controls traffic flow in the subnets. A company can also use other security tools such as Intrusion Detection and prevention systems (IDS/IPS) can also be used to monitor traffic after entering the firewall.
Vendor Analysis
Before choosing the cloud service provider, it is essential to analyse the available vendors thoroughly. Should consider Various factors to select the suitable vendor, including services, infrastructure maintenance, security compliance, and available security features. The service provider with well establish security management framework can effectively secure the SaaS applications and data from hacker threats.
Application Monitoring Tools
Organizations can use these tools to add security to the SaaS applications when the service provider fails to provide. For example, Cloud Access Security Broker (CASB) is software used to identify and fix the security gaps in all the cloud-based business models (SaaS, PaaS, and IaaS). SaaS Security Posture Management is also a security tool used to analyse the application configuration and find a compromise. It can be used for both on-premises as well as cloud-based applications.
Protecting the Data
Data protection plays a vital role in eliminating data breaches in an organization. It includes both physical and virtual security measures. It is mandatory to have proper data management. Can implement proper data security measures by classifying the data according to their importance. Data such as customer information, financial details, company documents should be given more protection when compared to other data.
Storage Management
It is crucial to determine which data is required and which is not. Accumulation of an enormous amount of unwanted data will lead to a data breach. The organizations should be careful in collecting the data from the customers. For example, confidential data such as the customer’s social security number should be collected if necessary. Storing a more sizeable number of data could reduce the efficiency of the data management, which increases the possibility of data theft or leak.
Frequent Updates
The technology is developing fast, which is also applicable to cloud service models. Hackers are also finding new ways to attack the business. Therefore, it is necessary to update the cyber-security software so that it could be able to prevent the latest threats. Outdated SaaS applications could also create new vulnerabilities in the cloud platform. Regular updates to the applications can prevent the hacker from exploiting those vulnerabilities.
Make Use of Key Vaults
Key vaults are like safe vaults used to store valuable things and secrets. These are digital vaults that can store confidential information such as encryption keys, database access codes, digital documents, etc. The critical vault adds to the security layer of the cloud applications, which can either be provided by the vendors or separately used by the organization.
Recovery Plan
None of the digital technology is hackproof. Therefore, it is wise to have a well-defined recovery plan from cyber-attacks. Delay in responding to the cyber-attack will increase the damage done by the hackers. So, it is essential to take immediate action in an attack. A company can do it by educating the security team and other employees of the organization in identifying and mitigating the threat. Assigning responsibilities to the employees can improve the efficiency of the incident response.
SaaS Security Checklist – Best Practices for Developers
To shield your SaaS application, we’ll look at some top-notch SaaS security checklists that developers can implement. You may already know the risks associated with your application and have taken the appropriate steps. Now let us dive into some practices that can help maintain SaaS app security.
Use Authentication
The organization’s password policy should be solid, like an alphanumeric combination and a unique phrase instead of random characters so no one can guess and hack a user account information.
Monitoring Account Activity
Must monitor the account activities regularly, and you should be able to see who accessed which data in the system. So, you can do that when you suspect any suspicious activity on the system; this will help us eliminate the cyber attacker who is waiting to steal the company’s valuable information.
Encrypt All Data
The developers should encrypt sensitive information like API keys, customer records, employee records, billing info, etc. They should miss no data because any unencrypted information will become an access point for the hackers. Once they get access, they will steal all the company’s valuable records, leading to loss of reputation or loss of business for the company. So, a developer must encrypt all the data.
Use Encryption
It is essential to use proper encryption methods like TLS/SSL certificates. All the network traffic should be encrypted using those methods, which will keep hackers away from accessing our data. Using weak encryption methods like WEP or WPA to send files between servers is vulnerable. Cyber attackers can easily hack the data within a minute, and they will steal the company’s valuable information.
Secure the Servers
One of the essential steps an organization should take to avoid a breach of sensitive data is to maintain its server properly with proper security patch updates. So, you need to update the server frequently with the security patches, which helps us to ensure that there is no back-door entry into the server. The other way of maintaining the server is with the firewall. It will help to increase the security of the server. Also, it should do proper security testing in a defined time interval to find the application’s flaws and ensure it works properly.
Limiting Admin Access
The admin access is critical. If it is not used correctly, the hacker can quickly get into the system and steal the company data. Admin should only give company staff administrator privileges on any network. Admin should only give others temporary admin access, where the passwords expire after the specified timeline, and they should be monitored.
Limiting Data Access to The Employees
Only employees who need access to sensitive data should be given access. Those who do not need it should not be given access. In addition, the users must be monitored if it is given, provided they have the expiring password for a defined period.
Check for National or Regional Authorities
Another thing that a developer of SaaS needs to follow is to adhere to the local regulations. They are nations that have authorities that issue guidance on using SaaS, the country, like the UK’s national cyber security center, offers essential security reviews of SaaS products. If you follow the regulation sincerely, it will help you have a good foundation for internal security analysis.
International Standards
The company should comply with the international standard that defines maintaining information securely like ISO 27000, which gives information about how to manage the information securely and includes a set of security controls to roll out.
The Developer should compile with SOC2 auditing procedure. This auditing procedure helps the company identify whether its third-party suppliers manage all the data correctly or not and increase the security of its data. The system must be complex and have plugins, or the system’s data must move between different providers.
Conduct Audit
An organization needs to perform audits on its technology to secure data. In addition, the organization has to update itself with the current technology; otherwise, the hackers will quickly take over your network.
Check the technology used to secure the organization’s data and review the authentication options and other security limits.
Check the user activities and their access level.
Check the easiness of the Security feature and ensure that a single IT admin manages all the users appropriately. By performing the above audits in a defined time interval, the organization can find their flaws and fix them before some hackers use them to hack their network, strengthening company security.
Conclusion
It’s not wrong to say that SaaS technology is and will be the best option, as it promises lower costs and more agile performance. We already know that there is a huge demand for SaaS applications worldwide, and many industries are thinking about adopting SaaS applications. However, most of them don’t know how to secure SaaS applications. Therefore, we have derived these best security measures from the cyber security experts to keep control over the security infrastructure, such as encrypting customer data.