Why Mobile App Security and Privacy Are Non-negotiable in Mobile App Development
The usage of mobile devices has been tremendously increasing in recent years. Every business is looking for an opportunity to develop a mobile application to reach more users across the globe. So, the demand for mobile application development is at its peak. The organizations are looking for highly functioning apps and the best features to develop from taking over the competitors quickly.
In the prevailing demand for apps, most companies ignore implementing app development and maintenance security protocols. This document covers mobile app development, security threats and best practices.
Mobile App Development
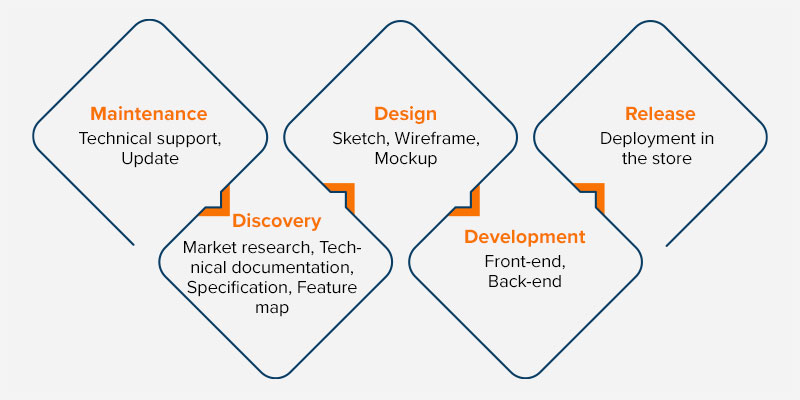
Mobile application development is a process that involves designing and coding mobile apps using basic software languages such as C, C++, JavaScript, etc. It is like the traditional software development process in computers. The mobile applications are developed for two major mobile platforms such as Android (Google) and iOS (Apple). Millions of apps are available in the app store for various purposes such as food delivery, net banking, video streaming, cab booking, etc. Most of the present applications are designed to make use of the features of mobile devices.
The above representation shows the process of mobile application development. The applications are developed using four types of approaches. They are.
-
Native Applications
Designed using the programming language and framework of the platforms such as Android and iOS.
-
Cross-Platform Applications
It is of different programming languages and frameworks but is composed to form a native application that can run on the device’s operating system.
-
Hybrid Applications
These are web applications designed using JavaScript, CSS (cascading style sheets, HTML. They are cost-effective compared to native apps.
-
Progressive Web Applications
It is a web page that acts like an application. It does not require app store delivery and installations.
Need For Mobile Application Security
It is also important to develop an application that is safe and secured. Previously, cyber-security was preferred in computers, laptops, and other networking devices vulnerable to malware attacks by hackers. But in recent years, there has been a paradigm shift in the cyber-attacks from traditional computer software to mobile applications. The main reason is the increased usage of mobile devices in daily life. Therefore, it is essential to secure the applications to avoid any cyber-attack.
Mobile app security is indispensable to protect mobile devices from various adverse effects such as
-
Data Theft
Poor mobile app security could lead to losing sensitive data such as customer information, login credentials, financial details, etc. The hackers will use the vulnerabilities available in the applications to gain access to crucial information. This affects both the customer as well as the company. It is detrimental to a business as it loses the trust among the users.
-
Financial Loss
The data available in mobile banking applications can include financial details such as credit card and debit card numbers, CVV, etc. If a banking app is compromised, it becomes easy for the hackers to get hold of the entire mobile. The hackers can make a transaction on the customer’s mobile without their knowledge. The lack of mobile app security also causes financial losses to the company through fines, compensation, restoration, etc.
-
Intellectual Property Heist
Intellectual property is also a property that incorporates human intelligence such as copyrights, patents, etc. All mobile applications have their base code on which the app is designed. This base code is intellectual property. Generally, the hackers try to abstract the base code of the successful apps to create their clones. Such cloning apps are created to trick the users into downloading the false app under the impression of the original app. These cloned apps can also be used to spread malware on mobile devices.
-
Reputation Damage
Security breaches in the mobile application can damage the company’s reputation. Once the user data is exposed, the customer’s confidence in the app company is ruined. This results in the loss of brand name. Every business works based on user trust. If the trust and reputation are lost, it isn’t easy to rebuild them.
Causes of Security Threats in Mobile Apps
-
Exploiting The Application Platform
A mobile application platform is where all the applications are available for download. The examples are Google play store and Apple store. These platforms have certain guidelines for application security such as android intents, platform permissions, keychains, etc. The improper usage of the platform’s operating system might result in data leakage during android communication.
-
Insecure Data Storage
Here, the security threat is caused by storing data in an unsafe manner. This vulnerability is mainly caused by the compromised operating system, jailbroken devices, improper handling of data cache and framework vulnerabilities. This leads to the hacking of legitimate apps to extract data from them. It occurs in various places such as binary data stores, cookie stores, SQL databases, etc.
-
Unsafe Communication
The data transfer in mobile applications takes place in a typical client-server model. Such data transfer is done over the internet and device carrier network. There is a possibility of hackers exploiting this vulnerability to access sensitive information. This cyber-attack can be carried out through an insecure Wi-Fi network, exploiting the network via routers, proxy servers or malware-infected apps. This leads to stealing of data, Man in The Middle (MITM) attack, etc.
-
Inappropriate Authentication
The improper implementation of the authentication process leads to security threats in the mobile app. Due to poor authentication, the hacker tries to bypass the regular identification process and thus access the information using a false identity. Mobile app authentication is more vulnerable when compared to the traditional web application as it does not require online authentication all the time. This offline loophole can be used by hackers to access the app.
-
Lack of Data Encryption
Cryptographic technology is used to safely transfer data by encryption and decryption methods. The poor data encryption method can compromise the integrity of the information. Hackers can exploit this vulnerability to interpret, steal, or tamper with the original data. It holds a high threat to the security of confidential data during transfer.
-
Weak Coding Practice
It is a solid threat caused due to the volatile coding practice. It is the result of dis-orientation among the members of the coding group where each person follows a different coding procedure. It causes inconsistency in the out of coding program of the app. However, it is difficult to identify the coding errors, which requires both automated and manual coding review. If the hacker identifies such a loophole, it could cause storage leaks; buffer overflows, compromised default libraries, and more.
-
Reverse Engineering
The reverse engineering threat occurs in Android apps where JavaScript codes are written. The coding pattern of the android apps can be exposed by applying reverse engineering tools and techniques. The online binary tools are used for this purpose. The threat is not the exposure of the base code but how it will be to replicate the original app to steal user information. It does not affect the app in a single device, but all the devices that use such an application.
Mobile App Security Best Practices
There are various mobile application security practices that can be implemented in app designing and maintenance. Some of them are as follow.
Open-Source Code Assessment
Most mobile applications use open-source code or third-party libraries which contain reusable source codes. Even though such codes make it easy to develop and deploy mobile applications, they are readily available to anyone, which poses a threat to the android apps that are using them. The method of reverse engineering can be used to crack the code easily.
Moreover, in the app development process, the open-source codes from the third-party libraries are merged with the written code, and they go unnoticed during app testing. So, it is mandatory to run a thorough test on the open codes for any vulnerabilities before adding them to the app code.
Solid Usage of Cryptography
The cryptography was originally used to transfer the data without revealing the message to the third party. This can be done by encryption and decryption of data during transfer. Now, this method is used in network communication for safe communication and storage of data. Using a strong data encryption technique, application data such as source code, user info, login credentials, app storage can be secured from hackers. Once the data is encrypted, even if the hacker steals the data, it becomes difficult to interpret the original content.
Using Code Signing Certificate
It is very important to code sign the mobile application to protect it from cyber-attack and gain the trust of the user. A code signing certificate is a digital certificate containing the CA’s digital signature (Certificate issuing Authority) along with the developer’s identity. It makes sure that the code has not been interpreted or altered after signing the app. There are many ‘cheap code signing certificates’ available, which can sign the mobile application. It is both cost-effective and provides high security to the application.
Enhancing the Data Cache
The cached data contains information retrieved from the app to help in faster reopening, thus improving the app’s performance. This data cache is generally stored unsafely in the user device. It makes it easy for the hacker to interpret the cache data and steal sensitive information. So, it is always safe to create a password to lock the application, making it difficult to access the cache data. It is also a good practice to clear the cache data frequently and log in using a secured network connection.
Safe Data Storage
Each application contains lots of data that cybercriminals can exploit to do malicious activities. It includes both users’ as well as the app developer’s information. Therefore, it is essential to store the app data safely where both the app and the device are up to date. The developer always recommends not to store the app data in a local store. Secured cloud storage can be used for this purpose. It is also important to have a layer of protection in the app to safeguard private information. It is a best practice to separate app data from user data.
Authentication and Authorization Techniques
The authentication and authorization process forms the two strong pillars of mobile app security. Both are equally important to secure the application from cyber-attack. The authentication process ensures that the users provide required information such as login credentials to open and access the data in the app. It is essential to have multi-factor authentication to prevent data theft. It includes user id, password, PIN, OTP, etc.
It is also essential to give limited authorization according to the requirements. Giving high-level authorization such as administrator to the normal user could result in data theft and tampering with the entire app. The authorization should always take place on the server-side to verify the role and permissions of the authenticated users.
Data Wipe and Device Locking
This feature is mostly used in the application, containing confidential data such as personal, financial, health information, etc. It is a security layer where the remote data is wiped after several unsuccessful logins attempts from the user side, and the application is locked. It also mandates the users not to use a sequential number instead of capital letters, special characters, alphabets, numbers, etc.
The enterprises use three types of data wiping solutions: factory reset wipe, full device wipe, and enterprise device wipe.
Counteract Reverse Engineering
The method of reverse engineering used by the hackers to tamper with the function of the application causes a serious threat to mobile app security. By gaining access to the app’s source code, the hacker can circumvent the authentication process, fake the location, and steal the app data. Enforcing the run time security is paramount to counteract reverse engineering. This prevents the hacker from modifying the internal functions of the app by changing the code structures to affect the application behaviour.
Conclusion
To secure the mobile application from cyber-attacks, it is essential to follow security measures. As mentioned in the document, the mobile app developed with a proper security framework can help avoid future threats from cybercriminals, thus gaining the users’ confidence. When it comes to business, it is all about the trust and confidence of the users, which can be gained by deploying a high featured app with a solid security framework.