The Significance of Cyber Resilience in Defending Against Modern Cyber Threats
The world is changing rapidly, and cyber-attackers are adapting to it faster than the rate of development of security solutions. Advances in technology also lead to advances in cybercrimes backed by the evolution of cybercriminals.
You cannot just stick to old-school techniques to prevent a data breach. Traditional security measures such as firewalls and antivirus software are not providing an adequate solution in the evolving cyber world.
To sustain the cyber-attacks, one must think of modern techniques to withstand and recover from the impacts of a cyber-attack, instead of just taking preventive measures. Yes, in this article, we will look at the importance of cyber resilience.
What is Cyber Resilience?
Cyber resilience is a framework that involves a sustainable approach against cyber-attacks. It covers all the three stages of a cyber-attack, including prevention strategies, incident response, and recovery.
Cyber resiliency aims to guide an organization during such adverse conditions and increase its recovery rate. Furthermore, it aims to safeguard the entire organization by considering all possible errors, which may vary from simple human errors to internal and IT controls deficiencies.
For instance, COVID-19 struck the world in 2020, and the after-effects struck hard. An organization with cyber resilience would have recovered faster than a non-cyber resilient organization.
In simple words, Cyber resilience is an organization’s ability to continuously deliver indented services, operations, and outcomes despite the occurrence of cyber events. These events can adversely impact technology, people, system, information, and facilities.
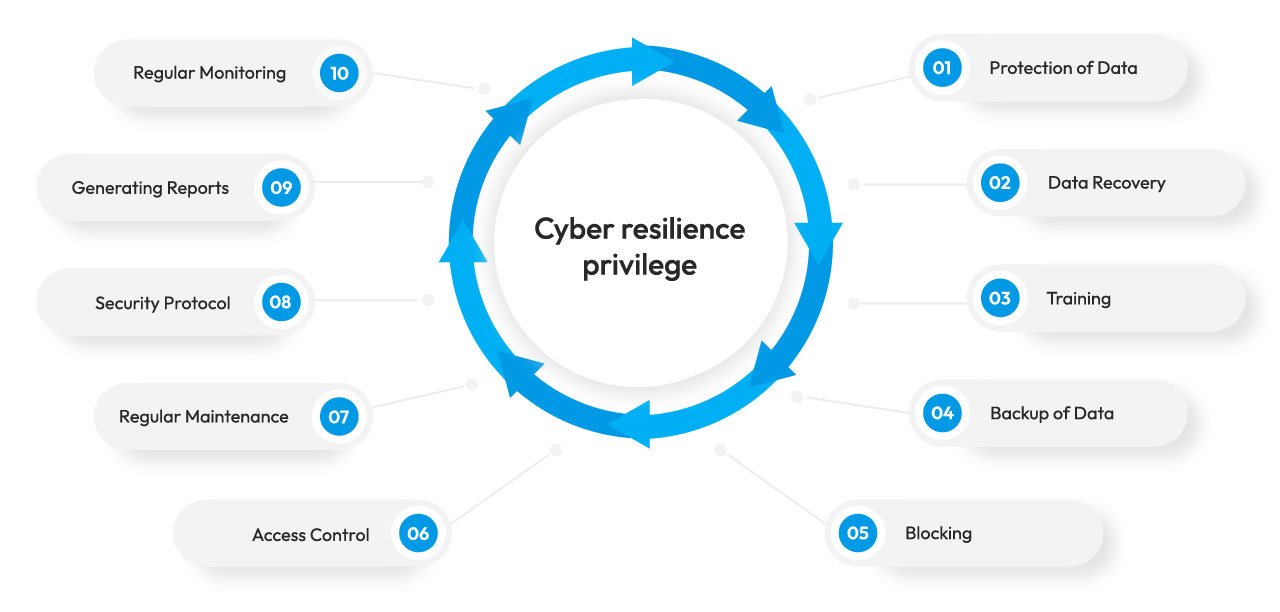
Cyber resilience privilege
Protection of Data
The data is secured from cyber-attacks with the help of security controls and made sure that the work is not affected.
Data Recovery
It helps recover the maximum amount of data in a limited time without much data loss.
Training
The employees working in the organization are given proper training on handling data securely and how to handle the situation when the organization faces a cyber-attack.
In addition, the employees are also trained on an organization’s security protocols in protecting the data and help identify their responsibilities during a data breach.
Backup of Data
Every organization operates with the help of data and statistics. Data is the key to the functioning of every business. So, data backup is of utmost importance during cyber-attacks or natural calamities. The data backup also helps prevent data loss and the costs of data loss.
Blocking
Cyber resilience also acts as a line of defense when cyber-attacks are attempted on an organization. It helps in preventing malicious threats from entering the system.
Access Control
Regular monitoring of the security team’s resources and assets helps protect confidential data from unauthorized access. In addition, controlled access can be achieved by implementing zero-trust security, which involves multiple-step authentication to prevent unauthorized and unauthenticated data access. Thus, cyber resilience helps identify unauthorized users and helps mitigate data loss.
Regular Maintenance
Cyber resilience helps in the regular maintenance of IT infrastructure and security controls. This can be done by conducting regular internal and external audits. Thus, cyber resilience helps an organization achieve a proper defense framework against a cyber-attack.
Security Protocol
Cyber resilience helps in framing a proper security protocol for an organization. In addition, the security protocol helps an organization comply with the rules and regulations of the regulatory body under which it performs. It also helps in reducing the legal costs associated with a data breach.
Generating Reports
The report of a cyber-attack is generated in case of a data breach. It helps the employees and security team analyze a breach deeper and ensure that the same mistakes are not repeated. Moreover, it could help avoid a similar data breach in the future.
Regular Monitoring
Regular monitoring of an organization’s resources identifies unauthorized data access and predicts a cyber-attack.
Components of Cyber Resilience
Cyber resilience involves multiple purposes such as securing data, identifying the cause of the threats, risk management, effective functioning of the organization during and after a cyber-attack. Cyber resilience ensures the proper business continuity of an organization even after a cyber-attack.
In addition, the company should be well prepared to face the after-effects of the cyber-attack. Thus, an organization’s cyber resilience relies on the six key components that help the organization mitigate the risks associated with a cyber-attack and secure and recover the data.
The response of an organization should be immediate, precise, and effective. Hence the following components are included while planning the cyber resilience of an organization:
Identify and Prepare
The first component of resilience is to identify and prepare. The first step in resilience is Asset Inventory. The organization’s assets such as hardware, software, and physical infrastructure should be identified, which helps find the vulnerabilities in the assets.
This step ensures that the security plans are framed according to the present vulnerabilities and involves checking the readiness of the existing internal and IT controls in case of a cyber crisis.
In addition, it is made sure that an organization’s policies related to data protection and security goals are properly woven with the IT infrastructure. It also involves identifying the risks associated with the network security of the organization, information in the system, and the IT infrastructure of the organization.
Protect
While the vulnerability associated with the assets and business functions are identified in the first component, the next component involves effectively implementing vulnerability assessment tools.
The organizations should conduct Internal and external audits to check the efficiency of internal and IT security controls. In addition, all the employees should be trained to have basic knowledge regarding cyber-attacks and knowledge of their roles and responsibilities in case of such an event.
This step of Cyber Resilience protects the information and systems from cyber-attack and unauthorized access.
This step involves managing the employees’ identities and control access, implementing the information security policies, effectively training the employees, and properly maintaining the software, hardware, and infrastructure.
Detect
The third step of Cyber Resilience requires continuous monitoring of information and network systems to detect abnormalities and potential cyber security incidence before they can cause any significant damage.
The system is scanned for suspicious activity such as illegal access, unusual network traffic, malware attachments, phishing emails, etc. Advanced analytics can detect the threats and investigate those hiding inside or outside an enterprise.
Respond
The next component of cyber resilience aims to take the necessary steps after a cyber crisis such as a data breach. The immediate response should be in identifying the root cause of the problem.
Then, the vulnerability that caused the cyber-attack should be figured out. Then, a proper plan should be framed based on the vulnerability, breach, and compromised data.
Next, the affected system/network should be isolated to reduce the effects of the breach.
Finally, the stolen data should be recovered from the available backup in a data breach.
Recover
During a cyber-attack, an organization undergoes financial as well as reputational breakdown. As the name suggests, this step deals with the recovery processes after a data breach.
It is crucial in resilience as faster recovery results in better organizational performance. The affected systems/network which was isolated is to be fixed, tested, and verified before implementing them in the cycle. This component of cyber resilience aims to ensure an immediate recovery of a company from the financial and reputational crisis.
Adapt
In this step, the cause of the breach and how the attack should be handled are discussed elaborately with employees.
It gives the employees a clear picture of the attack and its handling. This can be considered training and motivation to the employees that help face other possible attacks in the future.
How is Cyber Security Different from Cyber Resilience?
Cyber Security prevents hackers and cybercriminals from gaining access to the systems, applications, and data by implementing technologies, processes, and security controls.
Cyber security is important because the number of breaches increases daily, and the following consequences are devastating.
Cyber resilience refers to how an organization recovers from a cyber-attack. It also helps in reducing the risks associated with the data breach.
In addition, cyber-attacks affect a company financially and reputationally. Therefore, cyber resilience aims to recover an organization from the devastating effects of cyber threats.
| Cyber Resilience | Cyber Security |
|---|---|
| Cyber resilience deals with recovering an organization after a cyber-attack. | Cyber security is the security measures taken to prevent a cyber-attack. |
| Cyber resilience aims to mitigate the risks associated with a data breach and recovery of lost data. | Cyber security aims to protect the data, system, and network from cyber-attack. |
| Cyber resilience procedures vary between different organizations and according to the security updates. | The procedures are more or less the same in different businesses. |
| Cyber resilience security measures are implemented following the cyber security protocols. | Cyber security measures are implemented by the risks and vulnerabilities associated with a company’s assets. |
| Implementing cyber resilience measures guarantees the recovery of a company after a cyber-attack. | Implementing cyber security measures does not provide a complete guarantee to prevent cyber-attacks. |
Working of Cyber Resilience
Recoverability
To recover from a data breach, a company must have a well-designed recovery plan to ensure business continuity during the attack. It involves identifying the breach and patching it as immediately as possible, recovering the data compromised, and informing customers, stakeholders, and the regulatory body within the time permitted by the regulatory body under which a company performs.
The security team must take control over the situation by identifying the vulnerability which caused the breach and isolating the affected systems and networks to prevent the spreading of the data breach. In addition, it is crucial to minimize the data loss associated with a data breach.
A proper data backup must be implemented so that it isn’t affected by a cyber-attack. The loss of data could result in serious financial and reputational consequences. The Employees must be trained enough to handle the situation and take the necessary steps to recover the data.
The security team must notify its customers and stakeholders through emails and other mediums. The customer support team should be elaborated on the situation to handle calls associated with the breach. The breach should be disclosed as early as possible to maintain customer trust and client loyalty.
Threat Protection
With the evolving cybercrimes and cybercriminals, an organization cannot rely on old-school techniques to secure its data and network.
As many companies adapt to cloud technology to store their data, a company must find a robust cloud security provider who operates in compliance with the law. It is because the cyber-attacks on cloud-based industries have increased drastically.
Phishing emails, texts, and applications are a great threat to companies. The employees must be given proper training to identify and report phishing emails to avoid falling victims.
In addition, a company must invest in AI-based anti-phishing tools to avoid phishing emails and applications.
Due to the pandemic, employees adopt a work-from-home method to accomplish their tasks. Therefore, it leads to the increased usage of Virtual Private Networks (VPN) comparatively.
Therefore, a company must ensure that its VPN is secured properly to avoid the attackers gaining an advantage over them.
A company must also invest in Endpoint Detection and Response (EDR) and Domain Name System (DNS) mechanisms to prevent risks associated with a data breach. DNS mechanism ensures the filtering of malicious contents, and EDR ensures transparent endpoints to avoid risks associated with end-user computing.
Durability
Cyber-attacks result in financial as well as reputational consequences. The durability of a company is determined by the way it performs following a data breach. Data breaches result in reputational consequences; a company must ensure better performance to gain customer trust.
It can be achieved by investing in proper security controls and infrastructure and regular audits ensuring data protection to gain back customer trust. The affected systems and networks should be restored to enhance the company’s infrastructure. A company should be durable to function effectively following a breach.
Adaptability
Cyber resiliency is much more than just preventing and recovering from attacks. For a company to be cyber resilient, it must be adaptable to the emerging cybercrimes. The adaptability of a company depends on the ability of its security team, employees, and infrastructure in responding to a data breach.
Regular internal and external audits help identify a company’s security control and infrastructure status. After dealing with a cyber-attack, the security team must discuss the vulnerabilities that caused the breach and how the team handled it with the employees.
It will create awareness among the employees in dealing with a similar data breach. The security team must predict a cyber-attack in advance so that the consequences associated with it can be mitigated. This can be achieved by incorporating analytical tools based on Artificial Intelligence and Machine Learning.
Significance of Cyber Resilience
The main purpose of Cyber Resilience is to resolve the cyber issues arising in the business field:
- Cyber Resilience works effectively and efficiently to protect the systems from malpractices and also builds strategies to improve security by analyzing the rate of threats. If the confidential data is safe, the company becomes immune to cyber-attacks.
- Incorporating cyber resilience into an organization has major advantages such as enhanced data protection, improved IT governance skills, minimized human flaws, enhanced customer trust, etc. In addition, this ensures the durability of an organization’s functioning.
- Cyber Resilience leads to a healthy and active work environment by turning down the human effort in protecting data. It can be achieved by proper planning and implementation of cyber resilience.
- Cyber resilience helps in mitigating the financial and reputational losses associated with a breach by having a proper incident response and data recovery.
- Builds trust amongst the clients and customers by providing security to their data, leading to smooth functionality. As a result, the company will experience growth due to the safe and secure functioning, which attracts more customers who will turn into a client, and the client will entrust them with their process.
- Lesser risk can be assured to the organization by analyzing the access given to the data.
- It can be used to ease the management process of an organization since it uses automated technology.
- It performs tests on all the systems used to provide accessibility to the employees or authorized users, either by external or internal means to ensure security.
- The main advantage is that it works under the authorized rules and regulations issued by the government, so the organization that is using Cyber Resilience can be tension-free about its use.
- Minimal human strength and intelligence usage are required since it uses automated technology for its functioning.
Different Methods to Improve Cyber Resilience
Every protective method needs to be coherent and orderly, so enhancing technology is a continuous process. Henceforth, there are specific methods to improve Cyber Resilience, they are.
Transparent Asset Inventory
The primary and most crucial step in improving an organization’s cyber resilience lies in a transparent asset inventory. Asset Inventory is the collection of all the company assets that need to be protected.
This step is crucial as security measures cannot be implemented in protecting unidentified assets. Furthermore, in case of a data breach, a transparent asset inventory is crucial to isolate the critical assets from others.
Based on an asset inventory, one could figure out the vulnerabilities associated with an asset. In addition, it could give a clear picture of how an asset might get affected during a data breach. Nowadays, most organizations have introduced automated asset inventory techniques.
Using Automation Industry Curate technology
Automation technology is the set of all the machines and processes that helps in the automatic running of an organization. Therefore, automation technology like Artificial intelligence and Machine learning plays a vital role in improving Cyber Resilience.
These technologies can detect a threat in advance and act accordingly by implementing the necessary security measures, mitigating the risks associated with a data breach.
Prioritizing the Data Safety
Ensuring that the data is secure is the basic step to prevent cyber-attacks. Analyzing the data and protecting it in compliance with privacy and government policies is also important.
It will enhance the cyber resiliency of an organization. Another effective way to ensure the safety of backup data is by storing it in the cloud over local on-premises servers. It will provide additional defense in case of a data breach.
Secure Authentication
Employees have direct access to the data and systems of an organization. To improve an organization’s cyber resilience, the employees who have access to data and systems should be managed properly. Unauthorized access could easily lead to a data breach.
Creating Awareness
All the employees must be given regular training on the updates of the latest data breaches and how cyber resilience helps mitigate the risks associated with these data breaches.
They should be trained well enough to handle a data breach incident. They should also know their roles and responsibilities during a data breach. It will help improve the cyber resiliency of an organization and the chances of surviving a data breach.
Recruiting Capable Employees
Developing a healthy work environment will improve the quality of work and the output generated. Recruiting talented employees and guiding them properly on cyber resiliency could do miracles to the company in case of a data breach.
Talented and trained employees and advanced security controls could handle a data breach effortlessly.
Systematic Observation
It is necessary to monitor the systems and find out the flaws continuously. In case of any suspicious movements in the operating system, a data breach could be treated in advance.
Making the Patterns of Operations Unforeseeable
The dynamic changes made in the operating systems lead to the change in the operating patterns, and it will be difficult for the hacker to cope with regular systems changes. It will ultimately lead to failure in the attempts of data breaching.
Division of Network
In case of a data breach, namely a ransomware attack, it could spread from the attack site to other sites in contact with it. Thus, dividing the network into different sectors could avoid such problems during a breach.
Reduction of contact between the highly important services and not so important services is necessary. Because if there is any failure in the less important service sector, it will directly affect the highly important services, which are not affordable.
Advantages of Cyber Resilience
The need to protect digital data is becoming more intensive day by day. For the proper undisturbed operation of a business, it is necessary to incorporate Cyber Resilience, which is supple, easy to use, and irrepressible since many cyber crimes have been going on lately.
An extraordinary Cyber Resilience setup is proven to provide several extra benefits during all stages of an operation.
Lesser Number of Cyber-attacks Recorded
By giving precedence to the analysis of threats and preparing the countermeasures, the efficiency of Cyber Resilience can be enhanced, thereby increasing the organization’s digital and overall security.
If the threat analyzing teams determine the false alarms, they can easily focus on the actual incident and reduce it efficiently. Thereby, it provides high-level security towards cyber threats.
Less Punitive Actions and Mulcts
When a business firm uses Cyber Resilience techniques to protect their digital data and other security, the risks associated with data loss in a data breach are reduced. Thus, the firm is subjected to minimum fines, and penalties since the government’s law enforcement completely regulates it.
So, the protected data and its processes are intact with the rules and regulations. As a result, it leads to smoother operations in an organization and saves penalties.
Risk-free Business Operation
The overall purpose of cyber resilience is to reduce the risk associated with data breaching and prevent malware incidents. A fine Cyber Resilience makes it happen by unifying all the operation desks into a single platform.
It reduces the risk and lets the security teams be less tense. But for an organization without Cyber Resilience, data breaching may cause huge data loss and damage its reputation. In addition, this affects the economic growth of the organization, which leads to financial loss.
A Renowned Name in the Business Industry
To gain trust among clients and customers, an organization needs good business continuity and no data theft records. Therefore, for an organization that is Cyber Resilient, the data theft records will be at a minimal rate, which attracts more customers and helps in further economic growth.
In case of a data breach, an organization suffers criticism from the press, social media, the public, and even its customers. Thus, an organization’s reputation and brand value are disturbed locally and in online search results. This eventually reduces the existing number of customers and affects the flow of capable new customers and investors.
Reduced Economic Losses
Cyber-attacks not only affect the reputation and brand value of an organization. In addition, the financial status of an organization is severely punctured in a data breach, such as recovery costs, legal costs, investigation costs, etc.
Cyber resilience helps in handling a data breach effectively. The reduced effects of data breaches result in a minimum breach cost. Thus, cyber resiliency helps minimize the financial instability associated with an organization during a data breach.
Endured Functionality
Cyber Resilience prevents the systems and networks from getting breached and protects the data. Therefore, it reduces the risk of cyber threats and attacks drastically.
In case of a data breach, the primary task of cyber resilience is to ensure an organization’s business continuity by coming up with an immediate reaction plan against the breach.
Cyber resilience ensures the mitigation of risks associated with a data breach, thereby helping in the continuous functionality of the organization and recovering lost data in case of a breach. Thus, an organization remains competitive in the business against its rivals.
Capable Employees
Cyber resilience helps in producing capable employees. As a result of training sessions associated with cyber resilience, an organization’s employees become fluent in handling a cyber-attack.
They will be aware of their roles and responsibilities during a breach. Therefore, it ensures a healthy work environment where employees develop a piece of deeper knowledge on security measures and cyber resilience. It enhances the overall performance of an organization.
Current Center of Attention Needed in Cyber Resilience
Cyber Resilience mainly focuses on the highly co-operated fields with Information Technology and digital transactions.
1. Automation in Cyber Resilience
The use of old-school techniques and tools to handle sophisticated cyber-attacks is not easy for the security team. Moreover, the time to detect and respond against a breach is maximized due to alert overload, shortage of talents, and manual work environment.
Installation of automated and machine learning tools can help the security team quickly detect a threat and respond against it. The use of such tools simplifies the work for the security team and enhances the team’s response time against a breach.
Nowadays, companies are leaning towards Security Orchestration Automation and Response (SOAR) tools and techniques in handling attacks.
SOAR is software that responds against cyber-attacks automatically without human support by identifying the risks associated with a company with the help of data collected from various sources.
This technique provides suggestions based on history, thereby reducing the time to make effective decisions against a breach.
Thus, automated and machine learning tools in cyber resilience help increase the security team’s productivity, the quicker response against a breach, etc. Therefore, it increases the business continuity, the productivity of an organization, reduces human error, and reduces the breach rate.
2. Crucial Event Supervision and Prevention of Attacks
The business workflow involves several processes such as monitoring the system and network, reporting in case of a threat, and testing the entities who access data and controls in the system and network. Integrating all these operations into a single workflow helps create a highly secured cyber-resilient environment.
The entire workflow is automated into a single platform; it offers rapid data recovery. Also, the completely automated environment helps build a zero-trust framework by which flaws of trusted entities could be avoided. It also mitigates the risks associated with a cyber threat as threats are predicted in advance and ensures operation continuity even during a breach. This feature of cyber resilience helps in enhancing customer trust and satisfaction.
3. Advancement in Providing Technical Services
Compared to the previous generation’s service providence method, today’s system uses an evolved method to provide the services. As there is less threat and uninterrupted operations due to Cyber Resilience, every authorized employee can concentrate on their daily operations to provide their services to the customers as promised.
4. Improvising the Digitalism on the Incident Occurrence
The installation of advanced automated systems which can analyze a threat risk and respond effectively is important. This notifies the security teams to know about the digital trespassing and thereby prevents the tampering of necessary data from being violated or misused. Furthermore, so that an active functioning daily can be kept going on, it is possible when the improvisation of the technology in terms of Cyber Security is done.
5. Developing and Providing Access to Focus Center
The crucial elements of a security control process are creating a list of risks and vulnerabilities associated with a business organization, the list of operations in the business, and the plans to react to a cyber-attack. Combining these elements into a single platform enables the employees to understand the internal and IT controls.
Unification and Polarization lead to the accelerated supervision of the events occurring since it increases the efficiency of Cyber Resilience. Thus, risk or vulnerability is monitored in advance, and the hazards associated with a breach are mitigated. In addition, it ensures minimum workload for employees associated with maximum security in avoiding or handling a breach.
Conclusion
As already said, this sophisticated cyber world requires something much more than just cybersecurity called cyber resilience. The evolution of criminals and advancements in cybercrimes could shatter any means of defense.
Thus, it is important to incorporate cyber resilience into the security system to ensure faster recovery and enable business continuity even during an attack. Therefore, companies should not compromise on the cost of cyber resilience incorporation into their line of security.