
The Importance of Cybersecurity Awareness and Its Role in Threat Prevention
With the usage of the internet in all aspects of life, including personal and professional, the need for cyber security awareness has also increased. To handle cyber threats, it is essential to be aware of the possible cyber-attacks and the methods to prevent them. This document covers the essential cybersecurity awareness topics and their importance in the internet world.
Why Is Cybersecurity Awareness Needed?
There is a higher demand for cybersecurity awareness than ever before. Many reasons contribute to the necessity of cybersecurity awareness. Some of them are
- Prevent data breaches and possible cyber-attacks.
- Include the security culture into the business environment.
- Use developing technologies to create a secure defence against cyber threats.
- Increase the confidence of the customer to develop the business. Trusted customers are important for the business to run.
- Improve the cyber responsibility in the business world. The cyber-attack on one business will have a domino effect on the other business depending on it.
- Prioritize the well-being of the employees in the organization. The security awareness programs could help the employees personally and professionally.
Essential Security Awareness Keynotes
Password Practices
Password Practices For ages, passwords have been the first line of defence to secure sensitive information in the system. Even though many advanced technologies like biometric authentication and facial recognition are used to secure the devices, passwords’ prominence cannot be ignored. Despite having high-end cybersecurity software installed on the network systems, poor passwords management by the employees could open confidential information to the third party. Furthermore, if the passwords are easy to guess, unauthorized persons could easily open the system to steal sensitive data.

A single system with a vulnerable password can be used to affect all the other systems in the company’s network. This can be done by infecting the system with malicious software, which is more harmful than a data breach. Such situations can be prevented by following best password practices.
Steps to Have a Good Password Security
- All the online accounts and the organization’s accounts should be secured with strong passwords. The systems can be designed to mandate strong passwords, which should contain a combination of alphabets, numbers, and special characters.
- Avoid using common passwords such as birthdays, phone numbers, or other personal identification details.
- Use password manager software to generate and store complicated passwords, which can help the employees remember the passwords.
Educate the employees on the importance of strong passwords in data security and help them to create complex passwords to protect their systems.
Phishing Emails

It is the most popular cyber-attack through malicious emails under cover of the authentic source. In this attack, the hackers will send emails that contain links to the malwares. When clicking upon such links, the malware gets installed in the system and encrypts all the information available. The motive would be different for each phishing attack, including stealing the data, demanding ransom, infecting the company’s network to damage the reputation, and more. Most phishing email attacks are successful because they are pretended to be sent from reliable sources such as the organization’s business mail, higher personnel such as managers, etc.
Steps to Be Taken to Avoid Phishing Emails
- The primary step is to create awareness among the employees. Without proper knowledge of phishing emails, the staff could easily fall prey to malicious attacks.
- The phishing emails can be identified by a few clues such as altered spellings in the name, demanding immediate action to click the link, suspicious email addresses, etc.
- The employees should be encouraged to use encrypted email communication and email scanner to block requests from suspicious addresses.
Ransomware Threat
In this kind of cyber threat, the malicious software is spread through the systems to encrypt confidential data, and the hackers demand ransoms in return for the stolen data. Most ransomware attacks are incorporated with phishing emails used to scatter the malware across the network systems. These malwares are also hosted online, under the protection of legitimate software available to download. When the software is downloaded from malicious links, it spreads through the system and encrypts the available data. These data may include sensitive data such as personal information, photos, videos, company details, and more. Then the hacker would demand ransoms to decrypt the data in the system; otherwise, this information would be sold for money on the dark web. It is important to know that most ransomware attacks are unintentional. It can be easily avoided by taking preventive measures.
Steps to Be Taken to Avoid Ransomware Attacks
- Keep away from visiting suspicious websites that could have links to malwares in them.
- Do not download software from any unauthorized sources or websites. Either it can be for the mobile or the system.
- Conduct an awareness program for the employees regarding the ransomware attack and methods to prevent it. Restrict the employees from visiting unofficial websites over the company’s network.
- The latest software can be used to create a line of defence from any malware attack and minimize the damage to the organization.
Social Engineering
Using human psychology to get confidential information from people is known as social engineering. There are many methods under this concept used by hackers to get critical information such as system passwords, bank account details, ATM PINs, etc. It is done to get ransom either directly or indirectly by selling the stolen data. The social engineering technique is considered much easier than trying to hack the systems or devices with complex passwords.
This attack can occur in various mediums such as emails, messages, calls, social media, and more. For example, the hacker would call the victim and pretend as a bank manager to ask for the bank account details. So, the hacker could use the bank details and easily steal the money from the account. Even if a single employee’s system is hacked by social engineering, the entire network becomes vulnerable to cyber-attack. Real-world groups like Scattered Spider have used similar tactics to impersonate employees and compromise major enterprises.
Steps to Be Taken to Manage Social Engineering Attack
- The public should be given awareness about the social engineering attacks. They should be warned against providing personal information to unknown persons over any form of communication.
- It is the organization’s responsibility to conduct an awareness program to educate the employees about social engineering.
- Avoid posting too much personal information on social media platforms, which could help the hackers get more data about the victims.
Multi-Factor Authentication
In recent years, many organizations have used multi-factor authentication to protect their online and offline network. Adding to the traditional passwords, other authentication procedures such as one-time passwords (OTP), verification codes, etc., are used to secure the websites and networks. For example, it is widely used in a bank account that asks the users to enter the password and the OTP that will be sent to the registered mobile number or email address. This makes sure that even if the hacker gets the password to a net banking account, he cannot log in to the account without entering the OTP. Multi-factor authentication provides a second layer of defence to confidential information.

Steps to Be Taken to Multi-Factor Authentication More Effective
- The employees should be insisted on using multi-factor authentication to protect their systems and confidential files.
- The authentication data such as OTPs and verification codes should not be shared with third-party.
Remote Work Menaces
In the covid-19 situation, work from home has become a new normal, increasing the possibility of cyber-attacks. It poses a new threat to business operations. In general, the work- data will be shared among the connected systems within the company’s network. The closed network in the office environment can be easily secured than the open network in individual homes. But in the remote work scenario, the data are shared over an open network, creating a huge opportunity for hackers to steal business information.
Steps to Be Taken to Improve the Remote Work Security
- Additional security factors such as VPN (Virtual Private Network) can be used to protect the online privacy of the remote systems by preventing the internet service provider (ISP) from tracking the browser activity.
- As the company’s data security depends upon the employees, it is essential to conduct a cybersecurity awareness program to educate the employees about the best cybersecurity practices that can prevent cyber-attacks in remote work.
- Organizations should follow security practices such as updating software, using strong passwords, being aware of a phishing attack, etc.
Managing Removable Media
Removable devices such as pen-drive and hard disk store the data externally. It may also contain malwares that can infect the entire device and make it vulnerable to cyber-attack when connected to the system. Therefore, it is not advisable to use unknown removable devices in the office systems.

Steps to Manage Removable Media Threat
- Organizations should implement strict rules against removable devices in the network systems as it can pose a serious threat to the company’s network.
- It is advisable to use the removable devices after formatting the contents. In this way, the unknown malwares in the device will be deleted.
Physical Security

Even though the latest network security software is used to secure the company’s network, it proves useless if the physical systems are not secured from unauthorized access. If the organization has weak physical security for an important system, the third party can easily access the system to steal sensitive information. Therefore, physical security adds an extra layer of defence from cybercrime.
Steps to Be Taken to Enhance the Physical Security
- A system containing confidential information should be secured in a locked room with limited employee access.
- The employees should be given an awareness program about physical security. Common mistakes such as leaving the system unlocked, documents and files unattended, leaving the cabin door open, and more should be avoided.
- The company could increase physical security by using access cards for entering and leaving the office.
Requisite of Data Backup
Data backup is a crucial step in managing cyber-attack. It is not possible to prevent all the cyber-attacks from happening. The organization should be prepared to retaliate the cyber-attack if it comes off. The main aim of all the hackers is to extract confidential data from the company’s network and demand ransom in return for the data. So, the organization should be ready to face data loss and be able to retrieve the data for uninterrupted business. This can be achieved by taking regular backups of all crucial information and storing them safely.

Steps to Be Taken to Implement the Data Backup Policy
- The employees should be advised and guided to take responsibility in securing the organization’s data through the regular backup of the data under their control.
- The data backup should be stored in a secure place such as cloud storage with high security.
Using Cryptographic Technology
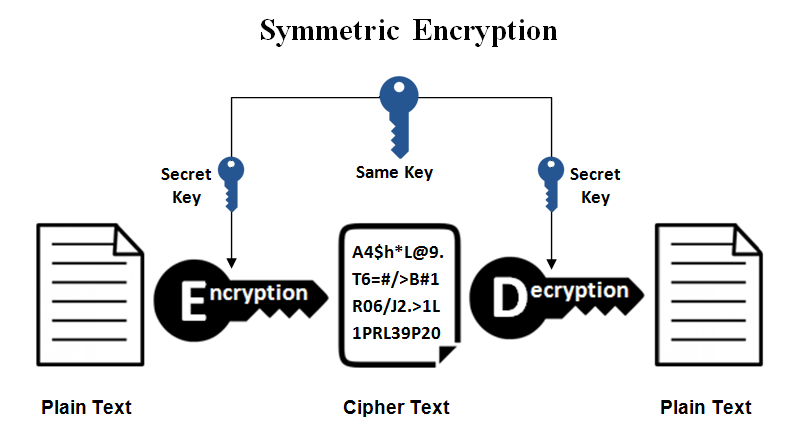
It is essential to protect the data during the online transfer of information. Organizations hold the responsibility to secure their data via cryptographic techniques. Where the data is encrypted to prevent hackers’ sneaking, it is not easy to understand the information without decrypting the data, which can be done only with the private key. This ensures the security of the online data. The General Data Protection Regulation also mandates the company to protect sensitive information such as customer details, personal data, etc.
Steps to Secure the Data Using Encryption Technique
- Always use the SSL Certificate to protect the information available on the organization’s websites.
- The emails can also be secured using end-to-end encryption technology. It prevents hackers from interpreting online communication.
- The confidential company file can be stored in an encrypted format to safeguard it from cyber-criminals.
Public Wi-Fi Threat
Using public Wi-Fi is another easy method to access personal devices. With the growing technology, we use the internet for all our activities. So, many people use the public internet for their devices. However, using the unknown network to access personal devices such as mobiles, laptops, etc., poses a greater threat to data security. The hackers could use an open network to get into the personal devices and encrypt all the personal details without the owner’s knowledge. This could lead to data loss and ransom threats from hackers. Furthermore, the loss of financial data could result in money theft from the respective bank accounts.

Steps to Prevent Public Wi-Fi Threat
- Educate employees against the usage of company devices under public Wi-Fi connections.
- It is safer not to use public networks for personal devices to prevent data loss.
Social Media Scam

Social media usage is increasing day by day, increasing the threats based on them. Hackers use social media platforms to steal personal information from the individual or the organization. It can be in any form, such as malicious links, registration forms, gift cards, and more available on social media platforms. The criminals may use the acquired personal details to get access to the professional information of the individual. This could lead to a data breach in the company network.
Steps to Be Taken to Avoid Social Media Scam
- The employees should be trained on the risks posed by social media and advised not to post too much personal information on social media.
- Think twice before visiting any unknown websites through social media which could also contain malware to attack the system.
Payment Security
All the cyber threats are based on financial gains where payment gateways have become the easy target for hackers. By getting access to confidential information such as bank account numbers, phone number, ATM pin, etc., the hacker can easily steal money from the bank accounts. Therefore, if a business holds an online payment gateway, it is the organization’s responsibility to protect the transaction details from the third party.

Steps to Safeguard the Payment Gateway
- The respective company should implement multi-factor authentication for online payment gateways.
- The transactions should be encrypted to prevent them from third-party interpretation.
- The user data should be stored in a secured place.
Incidence Response
Even after taking all the required cybersecurity measures, some cyber-attacks are unavoidable. Therefore, it is important to have a minimal response time in such a situation. The more time is taken to identify and respond to the cyber-attack, the higher will be damage to the company. Therefore, it is essential to respond quickly to the threat and try to fix it as soon as possible.
Steps to Be Taken to Minimise the Response Time
- The employees should be trained to identify and report the possible threat to the management as soon as possible.
- Cybersecurity software can monitor the network abnormalities and find the cyber-attack at an earlier stage. This helps to take immediate actions against cyber-attacks by isolating the infected systems, retrieving the stolen data, and more.
Conclusion
Giving importance to the security awareness training program is the primary step against the existing cyber-threats. This helps to reduce the losses due to cyber-attacks by the hackers, which include monetary loss, reputation loss, data loss, and more. This can be easily avoided by effectively implementing security measures across the organizations.




