The most awaited the new year 2015 has arrived and ready to flourish your life ahead. SSL2BUY wishes you a prosperous new year and ready to provide enhanced product support for better future security prospects. We brought a modern revolutionary robust SHA-2 algorithm and strongly recommend to switch your certificate from SHA-1 to SHA-2 Hash Algorithm for improved web security.
The SSL certificate is a backbone of web security and helps to validate the identity of your website. SHA-1 and SHA-2 both are algorithms used in SSL to sign the certificate for identity validation. Before few months, all SSL certificates were signed by SHA-1 algorithm, but recently, in response to the NIST advice and the CA/Browser forum, all major browsers, and certificate authorities (CAs) have started to deprecate a SHA-1 algorithm and started to migrate to SHA-2, which is quite stronger and secure than its previous algorithm. Therefore, it is a wise decision to migrate your SSL to a new SHA-256 algorithm.
If you are using an SSL certificate with the older SHA-1 algorithm and want to know about the migration of your current algorithm to a new SHA-2 algorithm, then this piece of information is going to help you a lot.
What Microsoft, Mozilla, and Google Say about sunset of SHA-1:
Microsoft and Mozilla Firefox have already declared about gradually sunset of a SHA-1 algorithm due to weak cipher and insecure against a collision attack. Even, Google has announced to switch to SHA-2 for its chrome browsers in the upcoming versions 39, 40 and 41.
Why You should Migrate to SHA-2?
Before switching to SHA-2, it is wise to know about the SHA-1 algorithm. Why is SHA-2 better than previous algorithms (SHA-1)?
SHA stands for Secure Hash Algorithm that produces 160-bit hash value. Four SHA algorithms (SHA-0, SHA-1, SHA-2, and SHA-3) differentiate from each other. After the failure of SHA-0, in 1995, SHA-1 was introduced which was widely used in many applications and protocols. Unfortunately, cryptanalysts found SHA-1 vulnerable against collision attack, and there emerged a need of new and updated algorithm to protect enough against attack, hence, SHA-2 was introduced.
What is SHA-2?
The NSA (National Security Agency) introduced SHA-2; the family of SHA-2 includes SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, and SHA-512/256, All are shortened versions of SHA-256 and SHA-512. SHA-256 is ciphered with 32-bit words while SHA-512 is computed with 64-bit words. It is a one-way algorithm means once a hash is used for a chosen file will not be used again, so each file that is hashed with SHA-256 is unique and carries equal strength.
Timeline Decided by Chrome Browser for SHA-1:
Google has announced below timeline for SHA-1 used in its Google Chrome browser and after that, your chrome browser will show security warnings on your page.
- If the expiry of an SHA-1 signed certificate comes after January 1, 2017, will be remained secure, but with minor errors and will be shown with yellow padlock.
- If the expiry of an SHA-1 signed certificate comes on or after June 1, 2016, to December 31, 2016, will be treated secured with minor errors.
- If the expiry of an SHA-1 signed certificate comes on or after January 1, 2017, will be treated as neutral, lacking security, and will receive a blank page icon.
- If the expiry date of an SHA-1 signed certificate is, January 1, 2016, to December 31, 2016, will be treated as secure with minor errors.
- If the expiry of an SHA-1 signed certificate comes on or after 1 January 2017, will be treated as “affirmatively insecure”.
Does your Browser support SHA-2?
Browsers have also considered this major effect and have already started to support SHA-256 algorithm. Major browsers, including IE-7+, Google Chrome 26+, Mozilla Firefox 1.5+, Apple Safari 5+, Opera 9.0+, Konqueror 3.5.6+ support SHA-256. Many old browsers do not support SHA-2 so you can get the complete list of browsers here that support SHA-256. If we talk about windows OS, then XP version SP3 supports SHA-2 while Android version prior to 2.3 versions does not support the SHA-2 algorithm.
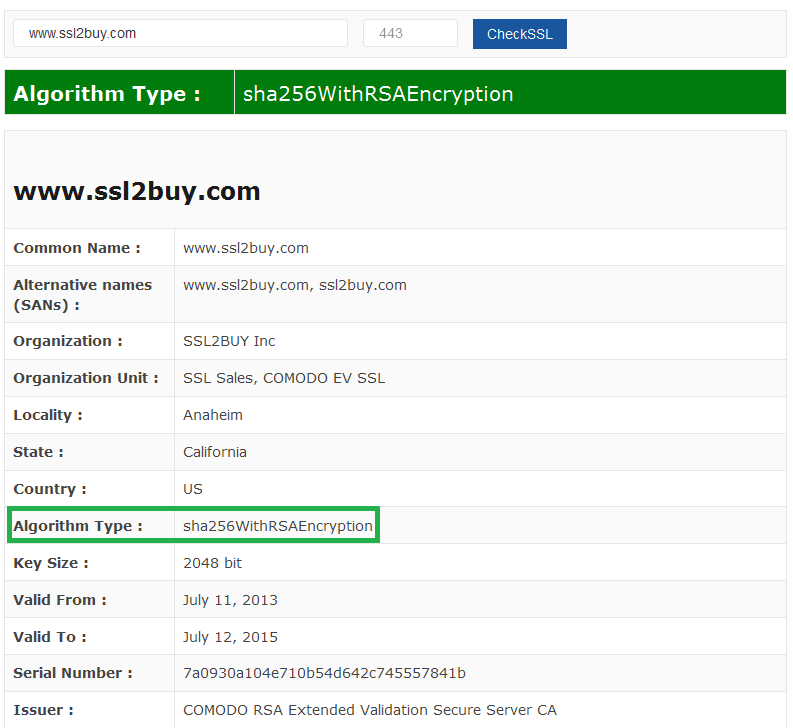
Check your Website for Signing Algorithm:
If you are not sure about the encryption algorithm used in your SSL certificate, there are two ways to know your certificate signing algorithm.
Option 1:
Using our SSL Checker Tool, you can easily find the current secure hash algorithm which is implemented on your website.
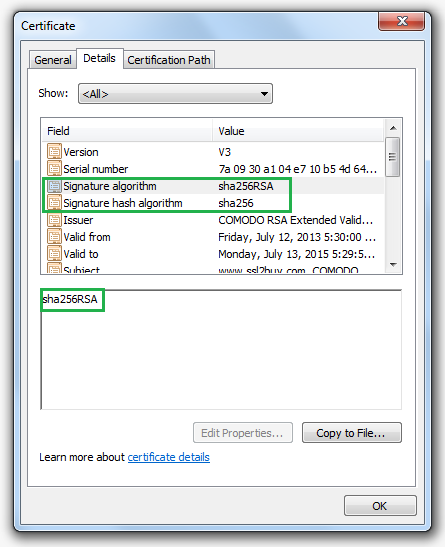
Option 2:
You can view the type of algorithm applied in your browser and for that, you have to follow below steps:
- Click on green padlock in the Chrome browser.
- Now click on “Certificate Information” shown under the “Connection” tab.
- You can find “Signature Algorithm” under “Details” tab that will show the type of algorithm.
What could be worst If not migrate to SHA-2:
SHA-1 is a weak algorithm and as we discussed major certificate authorities advising users to move to the SHA-2 algorithm. Therefore, if you have an SSL certificate, it will be a wise decision to move to SHA-2. If you run your current certificate on the old algorithm, then it will initially show a warning and later the website will be blocked if it continues with SHA-1.
What Steps Numerous CAs have taken for SHA-2?
After the announcement from Google, many certificate authorities (CA) have started to support migration of an SSL certificate. Few certificate authorities have issued a guideline or an announcement on their website regarding usage of SHA-2.
- Symantec Guidelines: If you are using an SSL certificate issued by Symantec, then Symantec has published about the SHA-2 announcement on its official blog. Symantec has also published FAQs guide that will guide customers about their queries.
- RapidSSL Guidelines: If you are using an SSL certificate of RapidSSL then follow this announcement for SHA-2 migration.
- GeoTrust Guidelines: GeoTrust authority has also published a guideline regarding SHA-2 under heading Product and Solution on their website.
- Thawte Guidelines: Thawte CA has already initiated SHA-2 algorithm in its SSL certificates and guided about replacing the current certificate with SHA-2 equipped certificates.
- GlobalSign Guidelines: GlobalSign being one of the most authenticated certificate authorities has also published guidepost about SHA-256 rollout.
How to reissue your SSL as SHA-2?
If you have an SHA-2 SSL certificate, then you do not worry and there is no need to follow this migration process because you already have it.
In another case, if your SSL certificate is bound with the SHA-1 algorithm, then you have to follow SHA-2 Migration process that requires a simple practice with below steps.
- Once you find that your current SSL is equipped with SHA-1, you need to replace your SSL certificate with the SHA-2 algorithm.
- Generate a new CSR (certificate signing request) for SHA-1 certificate on the server.
- Now, you can renew, replace, or purchase an SSL certificate to replace current algorithm (SHA-1) with the new SHA-2 algorithm.
- Once you receive the new SHA-2 certificate, you need to install it on the server along with required intermediate certificate.
- After installation, you have to check your website for a smooth function of newly installed SSL certificate.
Get your certificate Reissued at SSL2BUY:
SSL2BUY is a worldwide SSL certificate provider and always keep a customer-centric approach that is why we also have started SHA-2 migration for better security of our customers. Our all SSL certificates support SHA-2 algorithm so there is no need to scare about the algorithm update. Still, if you have purchased an SSL certificate from SSL2BUY that is bound with the SHA-1 algorithm, contact us to migrate your SSL from SHA 1 to SHA 2 algorithm at FREE of cost.