In an advanced interconnected world, the internet is essential in facilitating a significant portion of communications, making security a paramount concern. Whether you pick up a newspaper or follow a news link, you will see reviews of some other protection breach or hacking try. Despite the inherent risks associated with online communication and data exchange, the speed and convenience of technology make it a worthwhile endeavour.
However, there is a strategy to address these concerns. Consequently, businesses, agencies, and individuals are an increasing number of turning to various cryptography to ensure the secure transmission of data. One such technique is end-to-end encryption (E2EE), designed to enhance safety and mitigate dangers.
E2EE is essential as it can help you secure data against cyber attacks.
According to IBM, the average cost of data hacks in 2023 was USD 4.45 million worldwide. The cost includes violating terms, lost revenue, and reputational damage to businesses and brands.
According to the Government’s 2023 Cyber Security Breaches study, cybercrime affected 26% of medium-sized companies and 37% of large businesses in the last year. This emphasizes the necessity of data security and privacy in today’s landscape. Thus, to gain customer trust, you need to integrate E2EE.
Here you can learn about E2EE in detail to make an informed decision about your business and its brand.
What is End-to-end Encryption?
E2EE (end-to-end encryption) is a secure communication method that encrypts data transferred between two devices or systems. This strategy prevents other parties from hacking or accessing sent data.
Only the sender and receiver can get access to the information in E2EE. The encryption technique occurs on the device level, in which documents and messages are encrypted before being sent and decrypted only upon reaching their intended destination.
When people utilize E2EE to send emails or records, the content of their messages remains inaccessible to anyone other than the intended recipients. This includes government entities, hackers, ISPs, and application providers.
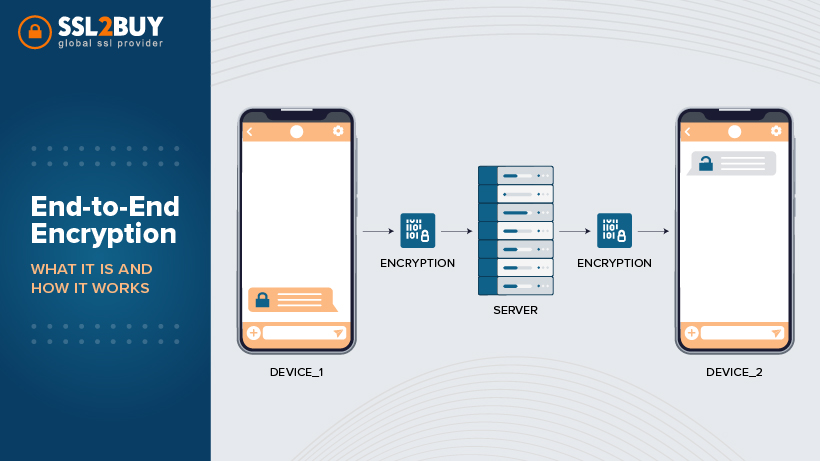
How Does End-to-end Encryption (E2EE) Work?
To know how end-to-end encryption is, you have to understand through this diagram.
For example,
Whenever John wants to send a private message to Max, he encrypts the message using Max’s public key. Only Max, who has the private key, can decrypt the encrypted message and access the original content. In this process, the private keys are never shared, ensuring that even if intercepted, the encrypted data remains unreadable.
E2EE encrypts the data at both stops at the device level, whether a mobile phone, point of sale device, or system. These are the steps that happen during the end-to-end encryption process:
Key Generation
The process starts with creating a unique encryption key. This key is the foundation of end-to-end encryption and the component that secures your messages. Each communication or session has a unique key, providing an extra layer of protection.
Data Encryption
Once the key is in place, your data is encrypted at the sender’s end before it is transmitted over the internet. Encryption converts your message or files into nonsense for anyone who intercepts them. This ensures that the intercepted data is unintelligible without the encryption key, even if your communication is compromised.
Secure Transmission
The encrypted data is then regularly transmitted across the internet. It is important to highlight that the service provider managing the communication cannot access the encryption key. This means the supplier cannot decode your data, protecting your privacy.
Decryption
The encrypted data is delivered to the intended recipient. The recipient’s device now uses its private key to decrypt and access the original content. This decryption process is simple and quick for the recipient, ensuring the security of your communication.
How to Tell When End-to-end Encryption is On?
Identifying the use of E2EE depends on the unique application or service. However, here are the common indications and procedures when E2EE is enabled:
-
Application Interface
Some applications provide visual indicators that indicate the activation of E2EE. These indicators frequently appear as icons or symbols beside a chat or communication channel. This informs users that the content within that interaction is encrypted for increased security and privacy. Users can look for these visual signs to ensure that end-to-end encryption is active within the application.
-
Service Documentation
For precise information on end-to-end encryption in a specific application or service, refer to the provider’s official documentation or help resources. Look for details in the privacy or security parts of the documentation, where the application’s encryption techniques and features are most likely detailed in detail. Official resources verify that E2EE is used and implemented correctly in the application or service.
-
Secure Connection Indicators
When accessing a web-based application, check the URL for “https://.” This suggests a secure connection, although it does not necessarily imply end-to-end encryption. The documentation will include precise information about the security methods to ensure a thorough understanding of the application’s data protection procedures.
Read more – HTTP vs. HTTPS: What’s the Difference? -
Security Labels or Certificates
Some applications use certificates or labels to indicate an encrypted connection. Users can often access this information in advanced settings or by clicking the padlock icon in their web browser’s address bar. Exploring advanced settings or engaging with security indicators gives users a better look at the encryption state.
-
Verification Options
In applications that use end-to-end encryption, users may be able to authenticate the identity of their communication partners by entering verification codes or keys. This additional step guarantees that users connect with the intended recipient rather than a hostile actor seeking to intercept or impersonate. The use of verification procedures improves the overall security of the communication process.
-
Open-Source Platforms
Users of free software can confirm the implementation of end-to-end encryption by reviewing the source code or the project’s documentation. Open-source enterprises often stress transparency, providing information about their security features and processes. Users obtain a thorough understanding of how end-to-end encryption is implemented by inspecting codebase or consulting the project’s documentation.
-
Check Encryption Settings
Examine the application’s settings for sections specific to encryption. Certain applications provide specialized options that allow users to turn on or off encryption for their communications or data. To modify and verify the encryption state, look for privacy, security, or encryption options in the program settings.
-
Service Notifications
Certain services may warn or alert users when E2EE is enabled or when encryption settings change. These notifications keep users informed about the security status of their communications by giving real-time updates on activating or modifying encryption features within the service.
What’s the Difference Between E2EE and Conventional Encryption Techniques?
A key difference between E2EE and conventional encryption techniques is that E2EE encrypts data throughout the entire communication process, while conventional encryption encrypts data at specific points.
Let’s understand E2EE and conventional encryption individually.
The E2EE approach provides better security than conventional encryption since it ensures that data is encrypted from sender to receiver.
In E2EE, each user has their own private and public keys. The best thing about these keys is that they are managed by their end users only, which eliminates the need for a central authority to control key distribution. The process is decentralized, which reduces the risk of failure to even a single point of communication.
In contrast, conventional encryption uses methods such as symmetric or asymmetric encryption to secure data during transmission and storage. In this case, data is typically encrypted at the sender and decrypted at the receiver, with encryption keys managed by a central authority.
Ultimately, end-to-end encryption ensures data remains encrypted on both sides (sender & receiver), whereas conventional encryption encrypts data at specific points. So, there’s no doubt that E2EE is better than conventional encryption.
When to Use End-to-end Encryption (E2EE)?
End-to-end encryption is used when security is paramount. E2EE is a crucial security measure in various digital communication scenarios to protect sensitive information from unauthorized access.
Here are some scenarios when to use end-to-end encryption:
Communication Privacy
E2EE is essential for securing communication channels which include messaging apps, email, and voice and video calls. Only the accessible recipients can get entry to the content. It safeguards sensitive discussions and private information.
File Sharing
When sharing documents containing exclusive facts, employing E2EE guarantees that the content material remains encrypted at some stage in the transmission manner. It prevents interception with the aid of third parties.
Cloud Storage
E2EE is crucial for securing data stored in the cloud. It adds an extra layer of protection. It ensures that the service provider cannot access the user’s files without the decryption key.
Collaborative Work
E2EE protects sensitive business information exchanged among team members in collaborative environments. It helps maintain the confidentiality of intellectual property and proprietary data.
When to Avoid Using End-to-end Encryption?
E2EE is considered a robust security measure. This encryption protects data by encrypting it at the source and only decrypting it at the destination. However, there are several situations when utilizing E2EE may not be appropriate or practical:
Key Management Challenges
Managing encryption keys in E2EE becomes complex for large-scale systems or scenarios with frequent user device changes. This complexity in key management creates obstacles to properly implementing and maintaining E2EE. Thus, avoid using E2EE in such situations.
Recovery and Access Requirements
Sometimes, users may need data recovery or access due to forgotten passwords, lost keys, or other legitimate reasons. But in this situation, E2EE may impede these processes. E2EE is built for rigorous access control, making data recovery nearly impossible without the necessary keys.
Collaboration and Sharing
E2EE complicates collaborative circumstances by preventing the seamless sharing of encrypted data across many users. Collaborative platforms and cloud-based services often require a certain amount of access for authorized users, which may conflict with the tight access control concepts of E2EE.
Performance Concerns
The encryption and decryption of data may cause computational overhead. In situations where real-time processing or high-performance requirements are essential, the additional processing time caused by E2EE can be troublesome. This potential delay may influence the overall performance of systems.
Legal and Compliance Considerations
Certain businesses impose unique legal and compliance requirements for data access and storage. E2EE may conflict with these requirements, requiring enterprises to strike a difficult balance between increasing security through encryption and meeting their legal obligations. Striking the correct balance becomes critical for companies working in such contexts to maintain data protection and regulatory compliance.
Metadata Exposure
E2EE may disclose metadata such as sender, receiver, and timestamp information. More precautions must be taken if metadata protection is required for comprehensive security. Organizations should prompt the need for additional measures if safeguarding metadata is crucial for comprehensive security.
User Experience
E2EE might lead to a less user-friendly experience, especially if users often transfer devices or need data recovery. When compared to systems without E2EE, the procedure may become more complex. Balancing strong security measures and user ease is critical when adopting E2EE.
While End-to-End Encryption is a strong security tool, businesses should carefully analyze their specific demands and use cases to determine its suitability. It strikes a balance between security and practicality.
What Are The Benefits Of Integrating E2EE
Right from communicating privacy to protecting theft attacks, there are multiple benefits of integrating end-to-end encryption to your communication. Here we have listed a few important benefits that cannot be missed.
-
Data Confidentiality
E2EE guarantees that only the designated recipient possesses the decryption key, ensuring exclusive access to the data. This confidentiality protects sensitive information from unauthorized access such as service providers and harmful attackers. E2EE helps to protect the privacy and integrity of communication by limiting access to only the intended persons involved in the communication.
-
Privacy Protection
E2EE protects user privacy by preventing third parties. This is especially important in settings that value privacy, such as personal texting or confidential business exchanges. Only authorized recipients with the required decryption keys may access and decipher the encrypted data. In 2022, Elon Musk discussed integrating end-to-end encryption to X messages like Signal.
Twitter DMs should have end to end encryption like Signal, so no one can spy on or hack your messages
— Elon Musk (@elonmusk) April 28, 2022
-
Mitigation of Intermediary Risks
E2EE reduces the risk of data breaches or leaks caused by vulnerabilities at intermediate points, such as servers or networks. Even if attackers access these sites, they only meet encrypted data. These data cannot be accessible without the appropriate decryption keys. This powerful security mechanism improves protection against unauthorized access.
-
User Trust and Confidence
Incorporating E2EE indicates an attention to user security and privacy. Users are more likely to trust a platform that uses strong encryption. Adopting robust encryption technologies increases user confidence by confirming the service or platform’s commitment to protecting their sensitive information and maintaining a high level of privacy.
-
Compliance with Privacy Regulations
E2EE is helpful for enterprises seeking to comply with privacy legislation and standards. E2EE is especially important in areas where privacy restrictions are severe. It guarantees that sensitive information is handled following legal and regulatory guidelines.
-
Protection Against Middle Man Attacks
E2EE is critical in protecting against middle man attacks. The lack of decryption keys means that intercepted data is secure and unreadable. It offers a strong defense against illegal access or alteration during transit. E2EE thereby improves overall security posture by resisting potential communication-based vulnerabilities.
-
Secure Cloud Storage
When data is kept in the cloud, E2EE helps to ensure that no one has access to the content. This level of security is essential for protecting sensitive information stored in cloud based applications. E2EE improves the confidentiality and security of sensitive data in cloud storage environments.
-
Reduced Insider Threats
E2EE is an effective barrier against insider threats within an enterprise. Employees and administrators with access to the infrastructure or servers cannot examine encrypted data without the necessary keys. This security technique considerably reduces the danger of illegal access or data compromise from within the firm. E2EE adds to a strong security posture by limiting access to only those with the necessary decryption keys.
-
Global Accessibility
E2EE enables secure communication and collaboration across geographically distributed teams. It allows users to transmit critical information without the risk of interception, creating a safe, collaborative environment in remote or international contexts. E2EE becomes a crucial enabler for enterprises with remote teams by assuring communication secrecy.
-
Protection Against Eavesdropping
E2EE effectively protects against eavesdropping. It boosts the confidentiality of communications even when sent via potentially insecure networks. This security feature ensures that any intercepted data is unreadable without the right decryption keys. It provides a robust barrier against illegal access.
Challenges In Implementing End-to-end Encryption
E2EE has become popular due to its usage and the way to encrypt messages. However it isn’t ideal and perfect for all situations. It also has some challenges that need to be looked at.
Here are some challenges to implementing end-to-end encryption.
The Technological Implication
You may be thinking that E2EE is easy and requires no effort, but you are wrong. Implementing E2EE needs a knowledge of cryptography, network security, and software engineering. This may be a complex for businesses, especially for the small businesses with limited resources. This is very time taking and can be a costly aspect.
Legal and Regulatory Limitations
Legal and regulatory limitations are the biggest challenges to E2EE. Strict regulations in various jurisdictions may require businesses to provide access to encrypted data for law enforcement purposes. This, as a result, poses technical hurdles and ethical concerns.
Lack of Standardization
Another E2EE implementation challenge is lack of standardization especially during encryption. Put simply, different systems might not speak the same encryption language. This lack of standardization throws a wrench into the works, making it tough for businesses to smoothly integrate E2EE across their varied tech setups.
How to Overcome End-to-end Encryption (E2EE) Challenges?
Here are a few solutions that you can implement to overcome challenges related to end-to-end encryption.
Balance Between Security and Accessibility
Overcoming the issues of end-to-end encryption necessitates a precise balance between security and accessibility. One option is to encourage collaboration between technology companies and law enforcement agencies to create novel methods for accessing encrypted data while protecting user privacy.
Zero Trust Access Control
In systems without a “trust perimeter (trust no one),” every part has to double-check access for each action. It’s like ensuring you have the right key for every door you open instead of assuming some areas are always safe. Each transaction is looked at closely to ensure it’s secure, using the specific details of that transaction to decide.
Deploy Identity Verification
You can deploy special tools that can overcome the challenges related to E2EE. Employing effective identity verification mechanisms during user onboarding can improve accountability and provide legal access when required.
Educate Users About Privacy and E2EE
Partnerships between the public and commercial sectors can be critical in defining industry-wide standards for ethical encryption practices, guaranteeing a consistent approach across different platforms. Users can be educated and made aware of the need to balance privacy and security, urging them to use encryption responsibly.
Finally, addressing the issues faced by end-to-end encryption while respecting the ideals of privacy and security requires a multidimensional strategy incorporating technological breakthroughs, regulatory frameworks, and user education. Now that we have enough knowledge about E2EE, it’s time to see the applications of end-to-end encryption to secure every communication.
Applications of End-to-End Encryption (E2EE) for Secure Communication
End-to-end encryption is used widely to improve the security of communication across various platforms.
End-to-end encryption is generally used in messaging apps like WhatsApp, however, it can be integrated in different applications for securing different kinds of files. Here are some key use cases where E2EE plays a crucial role:
Instant Messaging/Social Media Messaging
E2EE is widely used in popular messaging apps such as WhatsApp, Signal, iMessage, etc. These platforms use E2EE to protect customer data and privacy successfully. Users can engage in safe and private communication, sending messages and making calls with confidence, knowing that their activities are protected from illegal access or observation, by utilizing E2EE.
E2EE is used by some email services to improve the privacy of users’ emails. E2EE encrypts email content on the sender’s device and maintains encryption until the recipient’s device decrypts it. This procedure effectively inhibits unwanted access. It ensures that only the intended recipient may see the email’s content. This encryption secures the overall security and privacy of electronic communications.
Virtual Private Networks
Virtual Private Networks use E2EE to protect the data in online platforms. VPNs prevent any data by encrypting their internet traffic through the creation of a secure network channel. Those who value their online privacy and wish to protect their data against threats like hacking, monitoring, and data theft will find this to be of particular benefit. Higher security is provided by E2EE in VPNs.
Online Banking
E2EE is used by some online banking services to protect consumers’ financial information privacy. Users can conduct transactions with the understanding that their data is secure and private due to E2EE. This encryption technology ensures that the data is protected all through the transaction procedure, giving users a better degree of protection.
Healthcare Institutions
Healthcare institutions use E2EE to safeguard the clinical information and other sensible data of the patient. This safety function ensures that client data is secure and that only legal individuals can get entry to it. E2EE guarantees the confidentiality and integrity of patient information.
Advice For Users
Be cautious when communicating with unfamiliar contacts on end-to-end encryption services. Remember, while encryption boosts privacy, it also raises concerns about concealed online interactions, particularly involving adults and children. Stay vigilant for enhanced safety.
- Users must exercise vigilance and take responsibility for their actions when communicating on E2EE platforms.
- If users come across any suspicious or inappropriate content, they must promptly report it to platform administrators or law enforcement.
- Particularly critical is the immediate reporting of any signs of child exploitation to safeguard vulnerable individuals.
- Moral conduct and strict adherence to platform guidelines contribute significantly to maintaining a safe online space.
- Encourage users to actively report any behavior that raises concerns, which is vital in creating a more secure internet.
How To Implement E2EE?
E2EE ensures that only the intended recipients may access data, forming a powerful barrier against potential interception or theft by hackers or other unauthorized third parties. The steps for implementing end-to-end encryption are as follows:
Step 1: Choose the Best Encryption Protocol
Numerous encryption protocols are available. Choose the encryption protocol that best meets your needs. For example, SSL/TLS, ECC (Elliptic Curve Cryptography), IPSec and more.
Step 2: On Public and Private Keys
Each device involved in the communication process must produce a unique set of public and private keys. The public key is exchanged with other devices to facilitate secure communication. The private key is kept confidential to preserve the message’s integrity and privacy.
Step 3: Exchange Public Keys
The devices engaged in the communication must provide their public keys to encrypt messages so that only the chosen receiver can decrypt.
Step 4: Use Secure Communication Channels
To ensure communication security, use secure methods such as HTTPS, or a virtual private network.
Step 5: Implement Security Best Practices
E2EE is an important security layer. For optimum protection, combine it with multi-factor authentication, strong passwords, and regular software upgrades.
Conclusion
In today’s time, where security is a major concern, end-to-end encryption emerges as a crucial safeguard. From understanding its basics to addressing challenges and implementing best practices, we have covered everything to help you understand the role of E2EE in secure communications.
FAQs
What Does End-to-End Encryption Do?
E2EE is used to secure communication between two devices from third parties.
How To Fix End-to-End Encryption?
You can fix end-to-end encryption by revoking all active sessions, backing up your data, resting encryption keys, and restoring data from backup.
What Are The Benefits of End-to-End Encryption?
End-to-end encryption has various benefits, including data confidentiality, privacy protection, reduced insider threats, and protection against Eavesdropping.
Who Uses End-to-End Encryption Right Now?
Signal and digital trunked mobile radio standards like TETRA using end-to-end encryption.
What Happens When You Turn On End-to-End Encryption?
When you turn on end-to-end encryption, any text you send will be fully secured, and there’s no chance of being intercepted by third parties or hackers.




