Proactive Monitoring and Response Strategies to Detect and Block Ransomware Threats
As the cyber world grows day by day and makes our lives easier and more efficient, hidden threats and risks also increase. One of them is Ransomware, an expensive and ever-growing cyber threat on organizations’ critical data, files, or any other critical information from the past few years. Here the victim pays the ransom amount for his data locked by the attacker. There are different types of Ransomware to exploit victims or an organization to recover or decrypt their files against a ransom amount of money.
What is Ransomware?
When it comes to understanding Ransomware or defining it, it is malware used to lock the system and encrypt organizations’ critical data. While the key to unlock or decrypt the stolen data is given by attackers only when the victim releases the demanded payment. It is not wrong to call it cyberextortion and is also referred to as extortion ware. Almost all kinds of businesses and systems are at risk, and there are repeated ransomware attacks. Apart from encryptors and screen lockers, the threat of publishing stolen data comes from attackers. This type of attack is known as double extortion.
Well-known types of ransomware are as below
-
Crypto
Crypto Ransomware is the most common that easily spreads through malicious emails, websites, or downloads. It is impossible to access encrypted files and data without a decryption key. New variants are also there to infect systems. Various exploit kits are also used to deliver crypto-ransomware, which immediately downloads and runs malware whenever a vulnerability is found in the system to exploit.
Data encryption starts processing after the download, and it demands ransom by displaying a message. There are variants of crypto-ransomware like Crypto locker, which can encrypt various types of files, while Teslacrypt can only encrypt specific types of files. The payment process is instructed and often paid with Bitcoins or any other digital cryptocurrency.
-
Scareware
The ransomware-type scares or creates anxiety among users with multiple pop-ups showing malware or virus attacks and warning messages. They use this tactic to manipulate users and eventually make them buy potentially malicious software. Scareware always uses fear-based notifications, which is unusual compared to the real anti-virus software. It can also be explained as software which tricks you into visiting malicious websites that may infect your system. Fraudsters also use spam mails to spread scareware. Then, it directs the user to the payment page to resolve the issue.
-
Double Extortion
As the name explains, the victim or the organization faces extortion against stolen data. The attackers steal critical or confidential data and threaten to publicize it. Even after paying the extortion amount, the threat of publishing stolen data remains. The restoration of stolen data does not guarantee protection from data exposure. The Ransomware operators can easily leak the stolen data in underground forums or any other dedicated data leak site. Double extortion is where extortion happens in two stages. The first extortion happens to unlock the data or get the decryption key. At the same time, the second one takes place by selling the stolen data in the data web for a ransom amount.
-
Lockers
Locker Ransomware is the type of virus that infects and locks your system. The attackers use various vectors such as spam emails, malicious links, fake websites, and more to spread the malware that blocks the device’s access. Many pop-ups continue to display on the victim’s screen until the extortion amount is paid to resolve the issue. This Locker Ransomware is a copy of another well-known Ransomware called Crypto Locker.
The victim is locked out of the system or mobile devices and is forced to respond to Ransomware. This Ransomware also creates panic by creating a fake situation to pay a fine.
-
RaaS
Ransomware as a Service (RaaS) is a business model mainly taken over from SaaS (Software as a Service). It is a service provided to subscribers or affiliates to execute ransomware attacks with the already developed tools. These tools come with easy instructions to proficiently undertake highly sophisticated ransomware attacks.
It has reduced the technical barrier and has given lucrative affiliate earning potential. Some services are on a commission basis and without any entry fees. RaaS use the dark web for gaining affiliates.
Their services or kits include attractive offers, reviews, and forums and their charges vary from a few dollars to several thousand dollars. The user or the customer just needs to create a paid account and submit the details of the malware. Many RaaS operators appear and disappear, but some popular examples are Shark, Goliath, Locky, Darkside, and REvil. RaaS works on four business models, affiliate program, monthly subscription, one-time license fee with no profit sharing, and the last one is pure profit-sharing.
Different Stages of Ransomware Attack
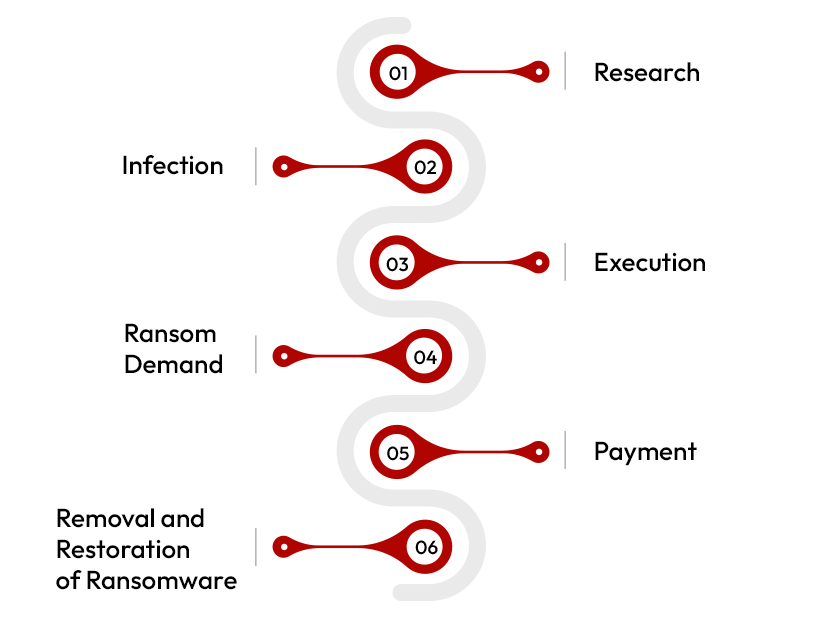
The different stages of ransomware attack are as follows,
Research
This stage is about research on the usage of software vulnerabilities. This attack aims to spread malicious links through research networks, spam emails, or other social engineering techniques. These malicious links trick the user and enable the malicious software installed in his system or device.
Infection
It is the stage where the cyberattack is activated after the malicious software is installed. Initially, it may not be visible but will slowly infect, encrypt, or steal the data. This dormant stage is crucial, and it is very important to identify the threat to minimize the damage. This infection stage sometimes can take months or years until the attacker calculates the time to launch the attack.
When the organization or the victim is unaware of the attack, it is even riskier and leads to bigger risks. The attack’s impact can be temporary or permanent, which causes a complete shutdown and financial loss. The targeted organization’s reputation also falls under negative impact.
Execution
In this stage, the encryption of the data begins through the malware installed in the network or the system. It blocks the organization or victim from accessing the data, whereas the total control of the data comes into the attacker’s hands.
Ransom Demand
At this stage, when the victim’s data or device is under the control of cybercriminals, the process for extortion of money or ransom amount begins. The instructions for the payment through Bitcoin or cryptocurrency are given to the victim. The victim regains control of the system by paying the ransom while the attacker gains the extortion money.
Payment
Payment is a stage when the victim is not left with any other option. Here, the demand for the ransom amount is paid as per the channel decided by the ransom attacker. However, the payment does not guarantee that the attacker will not share the data on the dark web or any other websites. It is also possible that the provided decryption key may not work.
Removal and Restoration of Ransomware
After the payment is processed, there remains a task to remove the malware and prevent similar cyber threats. Since the organization has already faced an attack, the system needs to eliminate any possible malware, which needs to be cleared and restored for regular operations to resume. The organization can also work with cybersecurity partners during this process of recovery and restoration to avoid any further risks in the future as well.
Most Common Ransomware Targets
The most common and some of the main Ransomware targets are as below,
Business
The rise of Ransomware attacks made all kinds of organizations, businesses, or enterprises the targets. Some of them have sensitive data that are very lucrative, which includes legal services, advertising, and accounting. It is often easy to target a certain organization for vulnerabilities or weak cybersecurity systems. However, some of them also manage to control the loss and restore their systems.
Education
The next most vulnerable and top ransomware attack sectors include universities and educational institutions. The ransomware attacks on schools, universities, and colleges steal data and succeed in damaging or disrupting the education or learning process. Over the period, educational institutions have become one of the most popular targets for ransomware attacks due to their loopholes in a cybersecurity system.
Their records contain many students, faculty’s financial data, intellectual property and research, medical records, etc. With so much critical data, the institutions have a very small IT team to manage the data due to budget-related constraints or other issues, but with a widespread network. Since their network sharing is high, it is a more vulnerable and easier target for Ransomware attacks.
Healthcare
Healthcare is a sector that cannot take risks against Ransomware as it involves the life risks of critical patients. Therefore, it makes it an easier target for extortion. Covid-19 proved to be an opportunity for cybercriminals to use the emergency for Ransomware attacks. In the “State of Ransomware” report in 2020, around 560 healthcare facilities were affected due to a Ransomware attack. Found multiple cases during 2021 due to Ransomware attacks in the global healthcare sector.
Banking/Financial
The financial sector is highly lucrative for cybercriminals, and the results are dreadful for the victim organization. The impact of cyber-attacks on the Banking sector has increased by 1318% during 2021, and the threat continues to spike up continuously. Therefore, this sector needs serious attention for cybersecurity measures and quick actions to prevent and protect against Ransomware.
Among the largest commercial insurers in the US, CNA financial paid a $40 million ransom demand in March 2021 to the attackers. It is also found that 91% of the financial institution sector have developed a recovery plan to manage this malware attack.
IT
In the IT sector, it is reported that there is an increase in about 65% of ransomware cases from 2019 to 2020. During this period, Phishing became one of the most popular tools or means to spread and target Ransomware attacks on organizations within a shorter period. By utilizing this pandemic, the ransomware gangs started to target multiple countries such as France, Germany, the US, and Italy.
Government
Security or police protection is a crucial and sensitive role among government agencies. Many have fallen under Ransomware attacks, and there is a hike from 2020 till 2021 of around 34% as per Sophos Researchers. In the United States, most municipalities are targeted in 2019 and 2020. The same led to the need for better cybersecurity measures to be implemented.
Manufacturing
Manufacturing companies are also a lucrative sector to target for Ransomware attacks. Some managed the attack as they were well prepared with backup and restoring data. However, as per the threat researcher’s unit, many manufacturing units could not meet the ransom deadlines, and their data were leaked on sites. In 2020, found almost 45 companies’ stolen data on leak sites. In addition, Industrial Control Systems (ICS) was used to control and monitor industrial operational physical equipment and are preferable ransomware targets.
Most of the critical utilities fall under ICS. For example, power and water. Attacks in these sectors resulted in damages, operational malfunction, and huge financial losses.
Here. Different types of Ransomware were used to target the ICS of different countries. The biggest attacks have happened in the US, Taiwan, Spain, and India.
Commonly Known Ransomware Examples
-
AIDS Trojan
It is the first known Ransomware. This Ransomware was classified as Trojan and spread through an infected floppy disc. This Ransomware disguised itself as an AIDS virus survey. The floppy label was “AIDS Information Introductory Diskette,” which made the recipient curious about the content.
This Ransomware tracked the number of computers booted by replacing the original AUTOEXEC.BAT file with its payload. Once the count reached 90, the Trojan would hide all the directories and encrypt the names of all the files available on the hard disc, making the system unusable. The victim then would be asked to pay $189 to renew the license by contacting PC Cyborg Corporation.
This Ransomware didn’t spread much and earned much ransom as passed it on using the infected floppy disc. However, it instilled the concept of using a program as Ransomware.
-
WannaCry
This Ransomware was categorized as a worm that rapidly spread across computers through the network automatically in May 2017. It infected more than 200,000 computers across 150 countries running outdated Windows Operating Systems.
This Ransomware took advantage of Windows EternalBlue exploit and used Server Message Block Version 1 (SMBv1).The WannaCry Ransomware would initially send a dropper packet executed by SMB. Once executed, this dropper would try to connect to the domain. The attack will stop if the connection is successful; otherwise, it would continue by sending two additional packets called encrypter and decrypter. Once these packets are available on the victim’s computer, the dropper would execute the encrypter file to encrypt and hide the user’s files and display a ransom note to pay ransom between $300 to $600 in Bitcoin to decrypt the same.
Security experts could find a kill switch (domain with random letters and numbers) that deactivated the Ransomware and quick patching of computers restricted the spread of WannaCry. However, this Ransomware had caused severe financial damage, adding billions of dollars.
-
Petya/Not Petya
Petya/Not Petya is a family of related Ransomware (Petya, Mischa, NotPetya) which infects computers running the Microsoft Windows operating system. It first surfaced in 2016 as a trojan disguised as a PDF attachment to an email. If the attachment was downloaded and opened, it infects the master boot record (MBR), and triggers restart. During restart, the Ransomware is used to encrypt the Master File Table of the Windows NT file system and display a ransom note to the user demanding payment in Bitcoin.
Petya and Mischa were typical Ransomware that used to rely on users’ ignorance to infect the computer because it had multiple user actions involved, like opening the email, downloading the malicious attachment, opening the attachment, and agreeing to provide administrative access to the malware.
In June 2017, a new version of Ransomware started spreading, like Petya; however, this was not a Trojan (disguising as an email attachment), but a worm (which can automatically infect a computer through the network) made it more dangerous. This version of Ransomware was called NotPetya.
NotPetya is used to change MBR and encrypt the files available on the hard disc.
It also took advantage of Windows EternalBlue exploit like WannaCry. Security experts identified “perfc.dat” as having the initial infection vector, which Ukrainian tax application MEDocs invoked. This Ransomware leveraged SMBv1 exploit to spread. In addition, it had also used the credential harvesting method to log in to a remote computer in the network. NotPetya was initially tagged as Ransomware. However, later found that it was acting more like a destructive tool. Could never decrypt the encrypted files; some variants could overwrite files physically, which could not be restored even if the victim pays the ransom. Initially, it assumed that NotPetya was intended for Ukrain; however, it had spread over Europe and US and caused financial losses adding up to 10 billion USD.
-
BadRabbit
Many experts relate this Ransomware to Petya/NotPetya family. It had used the same mechanism to manipulate MBR and encrypt files on the victim’s computer and ask for ransom in Bitcoin. This Ransomware is disguised as an Adobe Flash update.
This ransomware attack was carried out using a drive-by method where dropper was distributed using h##p://1dnscontrol[dot]com/flash_install.php. It will redirect the victims to this malicious URL from many popular news sites in Russia and Ukraine. Once redirected, a file named install_flash_player.exe gets downloaded, requiring the user to execute and provide administrative privilege manually. Once launched, it would save C:Windowsinfpub.dat and execute it using rundll32. It will further install dispci.exe into C: Windows and create a task to launch it. Finally, it Would encrypt the user files available on the hard disc with the RSA-2048 key and stop this ransomware spread by removing the malicious Adobe flash installer files from the reported website.
-
Locky
Locky, Trojan ransomware, was spread as Word or Excel attachments to an email asking for invoice payment. Once the user opens the attached Word or Excel file, it shows the content as garbage characters and asks the user to enable the macro. If the user enables the macro, then the word/excel documents download the actual malware, which encrypts all files with RSA-2048 + AES-128 public key and changes the file name with .locky extension. Other versions changed the file names with extensions .zzzzz, .thor, .odin, .aesir, and .zepto. Due to the advanced encryption algorithm, it was impossible to decrypt the file manually.
Microsoft office document or JavaScript as email attachment was used as the dropper. The malicious URL in the macro code downloads the payload. Once Locky infected the computer, a message would be displayed to instruct the victim to download Tor and visit a dark web website to pay up to 1 Bitcoin.
-
Cerber
Cerber had brought the concept of Ransomware as a Service (RaaS). It has commercialized Ransomware and attracted cybercriminals and developers to buy and contribute to Ransomware. In addition, they had shared up to 40% of the commission with the developers.
Cerberus typically uses spam emails to enter the victim’s computer. The email will contain a zipped attachment containing a malicious JavaScript file. This JavaScript file may either download and execute the encrypt program or schedule a task in the background after 2 minutes. In some Cerber versions, it had run PowerShell script as well. The victim doesn’t realize that their files are being encrypted. Once encryption is complete, they find ransom notes in encrypted folders or as a desktop background.
The evolution of Cerber ransomware targeted Microsoft Office 365 users. It has also leveraged the exploit kit. An exploit kit typically provides a platform for cybercriminals to launch an attack.
-
Jigsaw
The Jigsaw was another Trojan ransomware.
This Ransomware is also spread through an email attachment. It encrypts all files and Master Boot Record on the victim’s computer. Once the encryption is complete, it shows the ransom note as a pop-up with a countdown timer where Billy the puppet appears and demands a ransom. If the ransom is not paid in the first hour, the file gets deleted. The number of deletions goes up with every passing hour, and it penalizes the user by deleting 1000 files if the computer is restarted. Another version of Jigsaw also threatened the victims to reveal their personal information online.
-
Crypto Locker
Crypto Locker had been classified as an encryption Trojan. This Ransomware also used email attachments and Gameover ZeuS botnet to propagate.
Once a user opens the malicious attachment, the CryptoLocker deploys on the computer and encrypts all the local files and files available on mounted network drives. This Ransomware used RSA public-key cryptography, and the decryption key was stored on the malware control server. Once encryption is complete, CryptoLocker is used to display ransom notes and asks the victim to pay the ransom in Bitcoin or pre-paid cash voucher.
As per reports, using CryptoLocker, the ransomware author could extort 3 million USD.
Top Ransomware Headlines – 2021
The top ransomware attacks that make headlines in 2021 are as follows,
Acer
Acer is a Taiwan-based computer manufacturer with 7.8 billion USD in 2019. The ‘REvil’ ransomware group attacked Acer in March 2021. They had posted screenshots of financial documents they had stolen from Acer’s network. A Ransomware attack exploited Microsoft Exchange Server. The ransom amount asked was 50 million USD per Bleeping Computer report; it is the highest ransom ever asked in the history of ransomware attacks. Acer did not give many details about the attack and the ransom payment.
JBS Foods
JBS Foods is one of the world’s largest meat producers, and they experienced a ransomware attack on 30th May 2021 by the ‘REvil’ hacker group. This ransomware attack crippled the company’s operations across multiple countries and disrupted food supplies. This disruption also impacted food prices. Before encrypting the same, they had stolen 5 Terabytes of data, including customer information and business-critical confidential information. JBS food shared that they had paid 11 million USD in Bitcoin on 10th June.
Brenntag
Brenntag is a chemical distribution company having headquarter in Germany. The North American division of Brenntag was attacked by Ransomware conducted by the Darkside ransomware group. The Darkside group claimed that they had stolen 150 GB of data before encrypting it. The Ransomware used here was categorized as Ransomware as a Service (RaaS). Brenntag paid $4.4 million against a demand of $7.5 million in Bitcoin, which is also one of the highest amounts paid against ransomware extortion.
Colonial Pipeline
The Colonial pipeline attack was one of the most chaotic attacks that blocked gas supplies and down the system. It directly impacted Americans as this attack created gasoline shortages and panic among consumers. Government officials also agreed that the cybersecurity measures were not up to the mark. This attack covered the highest news coverage in April 2021. Colonial Pipeline finally had to pay 4.4 million dollars in Bitcoin, but the FBI traced the money, and eventually, US law enforcement succeeded in recovering the amount.
National Basketball Association (NBA)
The ransomware attack may happen in any industry, and the latest addition to that was the sports industry, where Ransomware attacked the national Basketball Association in April. The hacker group ‘Babuk’ claimed responsibility and reported that they have access to 500 GB of data of Houston Rocket which was classified as confidential. The hacker group threatened to publicize the information if it did not ransom.
CNA Financial Corp
CNA Financial Corp is one of the largest insurance companies in the US. Ransomware attacked their corporate network in March 2021. The whole network was held captive and infected with more than 1500 devices. As per Bloomberg reports, CNA had paid $40 Million in ransom to get rid of Ransomware. It was one of the largest sums of ransom paid by any organization.
AXA
Another high-profile ransomware attack had happened to insurance giant AXA Asia division. It had impacted the operations of AXA Malaysia, the Philippines, Thailand, and Hong Kong. ‘Abaddon’ ransomware group was believed to be involved in carrying out this ransomware attack. They had stolen 3 Terabytes of personal data, medical records, bank account statements, submitted claim forms, payment records, etc., before encrypting the same. The stolen data was threatened to be published on the dark web if AXA did not ransom. However, AXA did not disclose the ransom amount demanded by the Ava4ddon group.
Kaseya
Kaseya is an IT infrastructure management solution provider for Small and Medium Businesses (SMBs) and Managed Service Providers (MSPs). Kaseya was under ransomware attack in July 2021. REvil claimed this attack. The Ransomware took advantage of Virtual System Administrator and distributed the Ransomware disguised as a system update. Reported estimates suggest that around 800 to 1500 SMBs were impacted by Ransomware. It also came to news reports that 800 stores of Coop supermarket in Sweden had to close for a week. Ravil had demanded 70 million USD as ransom. The impact of this Ransomware was so grave that US President had to intervene. FBI could track and pull down REvil infrastructure and gain access to encryption keys which resolved the situation without paying any ransom. However, this ransomware attack has been considered one of the most widespread and damaging attacks.
Ransomware: Vectors of infection
-
Emails
Most Ransomware spreads through email that looks legitimate and encourages open malicious attachments. Once the user opens the attachment, the Ransomware gets installed and encrypts the files stored on the computer.
-
Removable Drives
Removable drives like Hard disks, USB drives are commonly used to spread Ransomware which is automatically transferred to the system during usage.
-
Malicious URLs or Websites
Many Ransomware is distributed using URLs mentioned in an email or shared using social media. Once the user clicks on the URL, the Ransomware gets deployed on the computer.
-
Malvertising
With the increased use of online shopping and social media platforms, Malvertising (Malicious Advertising) has become a popular way to spread Ransomware. In this method, cybercriminals use the ad-space and link to malicious websites or software. The advertising lures users to click on the ad, which activates the malware to scan the system and deploy malicious code if any vulnerability is found.
-
Drive-by Downloads
The term Drive-by download means any download that has happened without the user’s knowledge. Cybercriminals will host this Ransomware on their website to inject it into the victim’s device.
-
Infection Through Computer Network
Nowadays, most computers are connected to a Network. Therefore, classical Ransomware is categorized as Trojan, disguised as an email attachment, and requires human interaction. However, advanced Ransomware can be a worm that replicates itself and spreads automatically through a computer network without human interaction. Some of the most damaging Ransomware used this mechanism.
-
Plug-ins or Applications
Malwares are spread through pirated applications as well. Restrictions or permissions on installation protect it from any malware app downloads. It is better to read and check all apps before downloading.
Ransomware Detection Techniques
While it becomes difficult to deal with the aftereffects of ransomware attacks, it’s good to detect and protect from them by using major techniques.
The three major techniques to detect Ransomware are as below,
Traffic Based Detection
The traffic is analysed and examined with elements like volume and communication patterns to identify abnormalities in this method. As soon as any abnormality is detected, the account access is locked to protect from a ransomware attack. This technique can detect modified ransomware attacks. However, sometimes false-positive responses also happen, and C-level accounts are blocked, which is a drawback.
Signature-based Detection
The ransomware signature can be defined as a series of bytes commonly known as byte sequence in the ransomware payload. Signature-based detection is one of the most common mechanisms to identify Ransomware. Most Ransomware has a predefined byte sequence that can be detected by Anti-Virus, Intrusion Detection System (IDS), Intrusion Prevention System (IPS), or firewall with the repository of static ransomware signature. This technique is fast and accurate; however, this only works with known Ransomware. It is not effective against any new ransomware threat due to the lack of signature in the repository.
Data Behaviour-based Detection
In this detection, the data behaviour is monitored to check file abnormalities. Behaviour-based solutions monitor any malicious behaviour like encrypting emails. The detection here is accurate, but the security algorithms respond only after some files are encrypted.
Ransomware – Best Practices for Prevention
The Ransomware spreads and infects the system. Certain measures and steps help organizations protect from ransomware attacks. Prevention of malware is highly recommended, especially for the sectors where data theft and the threat of data leaks exist. The following can help in the prevention of cyberattacks and protect your system.
- Always keep your system updated with the latest security patches.
- Train everyone in the organization to follow best practices for cybersecurity.
- Avoid clicking on any link within your email and take time to check them. Nowadays, some emails are not authentic and are copied most of the time. So, look for minor details to identify and avoid ransomware-infected emails.
- Develop a regular practice of offline back-ups of important files and servers.
- Implement email security and IAM (Identity and Access Management) program.
- Take precautions regarding spam or look-alike emails containing links to malicious websites or downloads.
- Many malicious files are attached with downloads encrypted in zip files that are not visible. Take time to identify these malicious downloads and prevent cyberattacks.
- Gain proper knowledge regarding prevention and protection from malicious emails.
- Encourage and enforce the usage of a strong password.
- Enable multi-factor authentication for remote sessions.
- Use an Ad-blocker to incorporate networked devices.
- Provide authorization to the user by following the principle of least strategy.
- Do not use pirated software.
- Implement a firewall to block malicious site access.
- Never connect unknown removable devices to your computer or network.
Conclusion
Ransomware evolves with every new iteration, and attacks are growing every year. There is much Ransomware that spreads without human interaction. However, we can still restrict and prevent the spread and infection by following basic cyber hygiene. It is good to update and educate yourself with preventive measures regularly. There are many software and tools to prevent and protect your system from cyberattacks and strengthen the security of your critical and confidential data.