Root Certificates and Intermediate certificates are chains of trust or the certificate path, which defines the relation between actual SSL certificate and Trusted CA.
Online communications and e-commerce industries are based on trust. For example, your visit to an insecure insurance site may land you on a fake site, which is a duplicate of the original one.
How can you tell whether the site you have visited is a genuine one or a fake one?
Site trust can be established by installing digital security certificates. SSL certificates are digital security certificates used by site owners to secure their in-transit site data. These certificates are issued by Certificate Authorities (CAs) and are installed on the web server. They ensure the security of electronic communications by supporting data privacy, data integrity, and site authenticity.
Though web owners are aware of the importance of SSL certificate installation, they are unaware of the technical terms of these SSL certificates.
Hence, when these newbies of the digital market receive an email from their CA consisting of varied SSL files which need to be installed on the server, they show confused gazes. Their unfamiliarity with these file names like Root certificates, Intermediate certificates, and ignorance about the Chain of Trust and its hierarchy motivated me to write this article.
This article is meant for all these owners who are confused about these terminologies and their functioning. So, without further discussion, let’s get going, and I assure you that in the end, all your doubts about these terminologies will be clarified.
What is a Root Program?
Every single device includes a root store, a storage house for all root certificates downloaded up to date. The device uses the root store, which is supported and suggested by the operating system. At times, it may prefer a completely new root store (third-party) through the web browser.
Example:
- MS users use the Microsoft root store
- Apple (iOS) users utilize the Apple root store lying in their systems.
- Most Android users use Google.
These root programs have fixed rules and regulations, which are defined by the CA/B Forum Baseline Requirements. This helps in raising the trust bar amongst the users.
When the Certificate Authorities issue the certificates, the root certificate is affixed in the root store. It is a valuable certificate since it’s digitally signed with its private key. This digital signature makes this certificate more trustworthy amongst popular browsers.
This certificate has a huge validity period (25 years), and it helps in the issuance of other certificates.
Issuance of certificates from these roots is genuine, and hence they have named them the chain of trust.
What is the Certificate Chain?
Whether you name it The Certificate Chain or the Chain of Trust, it’s immaterial since both portray the same meaning. This chain is a compilation of CA certificates (bought by the web owners) and an SSL certificate.
The recipient of the certificate and the sender are assured about the authenticity and trustworthiness of the certificate.
Properties
- The chain consists of issuer details, i.e., the CA who has issued the certificate.
- The issuer of the current certificate is the same as compared to the subject of the next certificate.
- The certificates are signed using a secret key that corresponds to the certificate in the hierarchy.
- The last certificate (trust anchor) is the CA certificate which is trusted when issued from a reliable source.
Identification of the Certificate Chain
As stated, each certificate of this chain is signed by a secret key. It helps in identifying the next certificate in the chain.
For purchasing an SSL certificate, you need to generate:
A CSR (Certificate Signing Request) + A Private key.
When the CSR reaches your CA, they sign your SSL certificate with the private key used in signing the root certificate.
Browsers verify 2 factors before trusting a certificate.
- They check whether the certificate is signed with the root’s private key or not.
- They also verify all the certificates in the hierarchy, i.e., server, intermediate, and root.
When they get a positive response, they trust the certificate.
So, let’s discuss the certificate hierarchy.
Each certificate chain starts with the root certificate issued by the CA, followed by one or more intermediate certificates, and later ends with the last certificate (SSL certificate).
Root Certificate
The house of this digital certificate is the “trust store”, and hence it resides there. Since its ownership lies with the issuing CA, they keep a sharp watch on these certificates.
Intermediate Certificate
These certificates are mediators between the secured root certificates and the server (endpoint) certificates. It is compulsory to have a single intermediate certificate in the chain, though there can be multiple ones too.
Server Certificate (SSL Certificate)
This certificate is issued against the domain name for which the user-generated the CSR. It secures the root domain and, in many cases, sub-domains too.
The signatures of all these certificates are verified, with the public key lying in the certificate to ensure its genuineness. When the last server certificate is positively verified, it’s proof that the SSL certificate is authentic and trustworthy.
If certificate chains are incomplete, i.e., have a missing certificate, the browsers tend to display an error.
What is an Intermediate Certificate?
Certificate Authorities (CAs) are very cautious when it comes to the issuance of SSL certificates. They avoid direct issuance of server certificates via roots since it’s perilous and may boost fraud.
Roots are precious, and hence multiple root CAs are not advisable. To shield these roots and address this problem, intermediate CAs were introduced. They served as an additional security layer by taking over all the tasks of root CAs.
The keys of the root CA are inaccessible, and hence intermediate certificates act as a mediator between the root CA and the last certificate.
When signed (with private key), intermediate roots are issued by CAs; they become more reliable. The next step done by CAs is using the same private key to sign end-point SSL certificates. Finally, post signature of the same, SSL certificate is issued to the respective site owner.
In the case of the involvement of multiple intermediate certificates, the same process is done multiple times. Here, one intermediate root signs the next intermediate root, and all these can be used by the CA to sign the final SSL certificate.
When root CAs are to be identified, browsers make use of these intermediate certificates. In addition, these certificates are also used for the acceptance of the server certificates.
You might now have a clear picture of why the SSL folder has an intermediate certificate apart from the primary certificate. As far as the validity of these certificates is concerned, they have a better validity period than SSL certificates.
What is a Root Certificate?
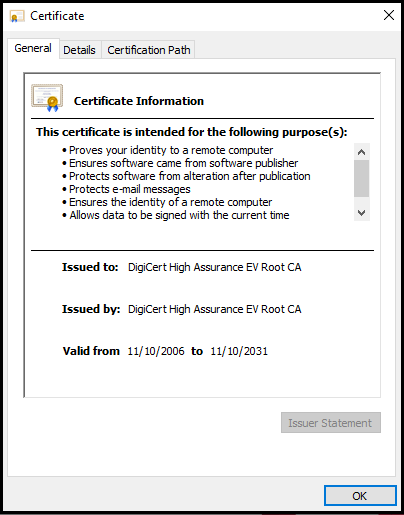
A root certificate is an X.509 digital certificate positioned at the head of the chain of trust. It is said to be the pillar of PKI (Public Key Infrastructure).
Each device comprises a root store which has reliable CA signs. Apart from previously downloaded certificates, this store includes their public keys too.
When browsers need to confirm the CA reliability, they match the same from their root store. However, if the CA name differs from the name mentioned in their root store, the browser will display an error warning to the user, stating that they are trying to access an unsecured site.
The root certificate is the leader, and the other certificates which are issued are the followers. So, if, by chance, the root keys are compromised, it becomes a threat to the Certificate Authority. Therefore, this compromised CA will be deleted from the root store, not to mention that the certificates they sign will all be cancelled.
Such catastrophes can be avoided by storing the root key in a secure place, i.e., the Hardware Security Module. This physical computing device safeguards the digital key, which has crypto processor chips to prevent infringement from cyber-criminals. Root certificates have the maximum validity period as compared to any other certificates.
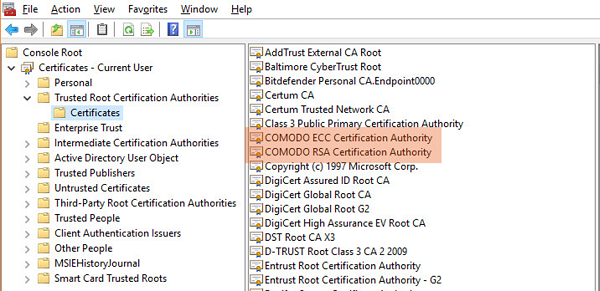
Root certificates are exquisite, and their reliability tends to enhance when they are digitally signed by their private key. Each certificate authority carries different root certificates and attributes. They are all visible in this trust store.
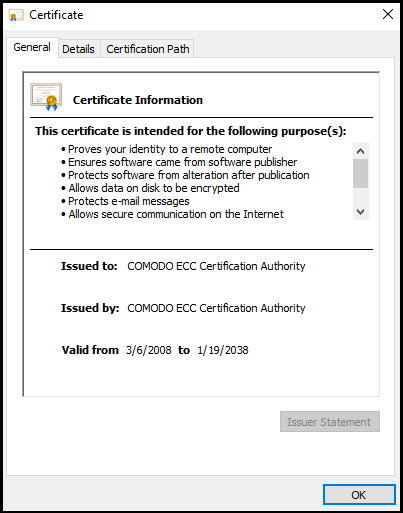
Can you see two Comodo root certificates that are highlighted in the above image?
One root cert is used for RSA signatures, and the other root cert is used for ECDSA.
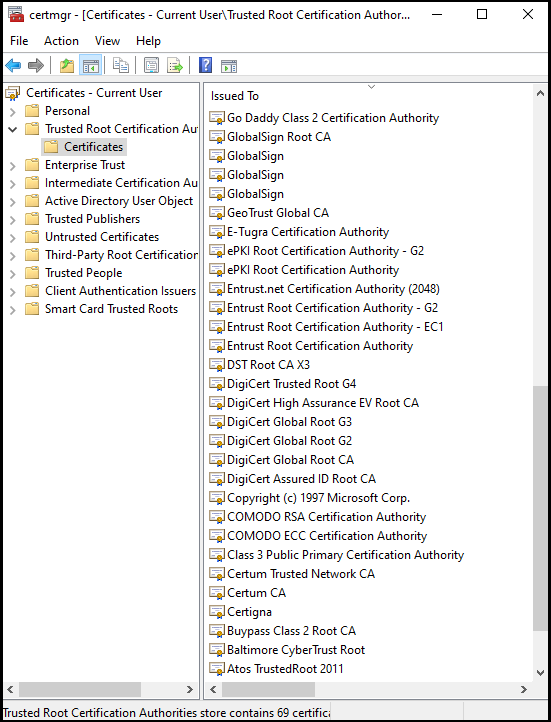
All the root CAs present in the Trusted Root Certificate Authorities folder in the certificate store are occasionally updated by their respective operating system.
Root Certificates vs. Intermediate Certificates – Differences Explained
Definition
The root certificates are CAs that possess reliable roots, which are stored on all the global browsers.
The intermediate certificates are CAs that provide intermediate roots. They don’t use browser storage but are chained to third-party roots.
Value in the Chain of Trust
The root certificate is precious and has a higher value in the trust chain than an intermediate certificate.
The intermediate certificate has a lesser value in the trust chain. It works as an intermediary.
Issuance
The root certificates prevent the CA from direct issuance of SSL certificates. Instead, they take the help of intermediate certificates to sign the endpoint (SSL) certificates for preventing breaches.
The intermediate certificate is the middleman, who protects the root certificate and issues the SSL certificates by signing the intermediates.
Certificate Revoke
In case of revocation of a certificate due to any emergency, root certificates need not be revoked.
In case of emergencies, intermediate certificates will be revoked to prevent damages. All the concerned intermediates will be suspected and removed.
Signature
The root certificate uses the private key to sign the intermediate certificate.
The intermediate certificate uses the same key to sign other intermediate certificates, if any, and the end-point certificate.
Issuance Name
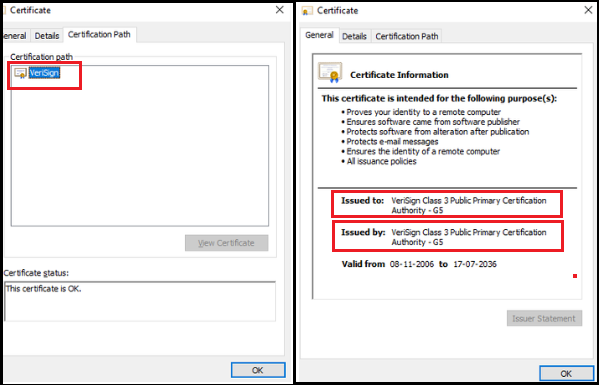
The names against the “Issued to” and the “Issued by” fields are the same in the root certificate.
The same is not true in the case of an intermediate certificate.
Certification Path
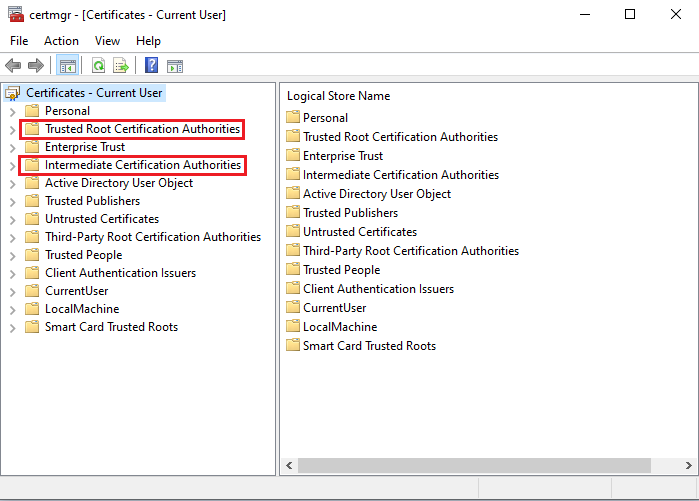
The root certificates display the top-most appearance in the certificate chain in the Trusted Root Certification Authorities folder. This path comprises a single level.
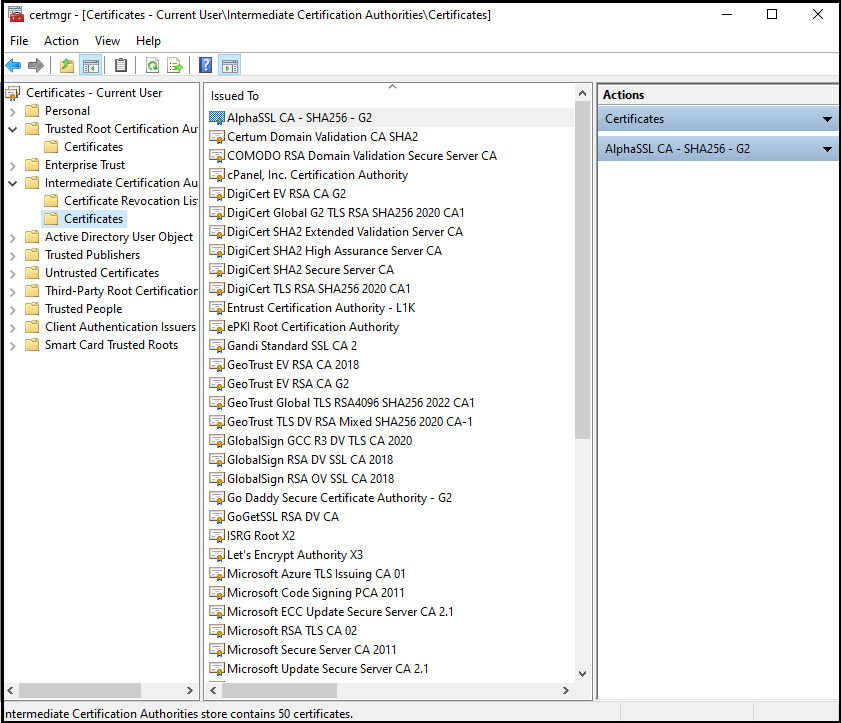
The intermediate certificates are in the Intermediate Certification Authorities Tab in the Console root folder. It may have more intermediates and more levels.
Damage in case of Emergency
If the root certificate has been tampered with, it may cause huge damages since the hacker can access the whole PKI and compromise the trust in the entire chain hierarchy. Hence, it’s advisable to keep this certificate offline for limiting its boundaries.
If the intermediate certificate has been tampered with, it becomes non-usable. The only option is to remove the same as well as the other intermediates to prevent further damages.
Validation Period
The validation period in the root certificate is usually up to 10 to 20 years.
The validation period in the intermediate certificate is restricted up to 1 or 2 years.
Access By
The Root Store accesses the root certificate. The Private Key accesses the intermediate certificate.
Storage Security Protocol
The root certificates are stored in the Hardware Security Module.
The intermediate certificates are stored in the SSL Installation Folder.
Final Words
It’s a challenging task to fathom these technicalities and handle these security certificates. Now that you have read this article, you may be aware that both these certificates are similar in nature and functions but still are very different from each other.
Root Certificate is kept offline, and they never reach end users since they are kept under tight wraps for security reasons. In contrast, the intermediate certificate is kept online for signatures and issuance of other intermediates and end-point certificates.
In a nutshell, both certificates are pivotal in the chain of trust of PKI. The absence of any will break its chain and trust. So, ensure to use both these certificates for securing your systems and digital infrastructure.