Get Private Key for SSL Certificate to Enable Secure Server-side Cryptographic Processes
The private key is created during the generation of the CSR code. People often don’t know when the private key was created and where it is. But it is pretty essential to know its location to activate the SSL certificate. If you cannot find a private key, follow this guide to solve your problems.
What is a Private Key in SSL?
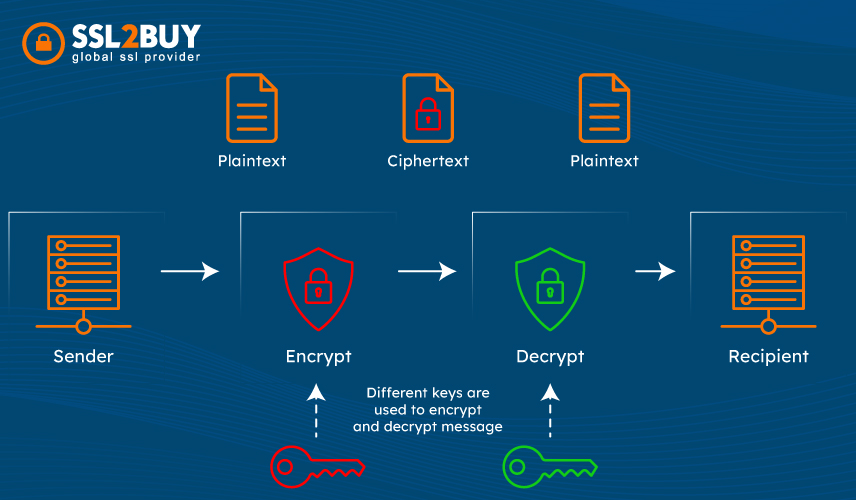
A private key is usually a long string of numbers or letters generated randomly that cannot be guessed easily. It is utilized within an algorithm to encode or decode the data.
It is also known as the secret key, and it must be kept safe within the server or offline. Private keys play a crucial role in cryptography (both symmetric and asymmetric). The secret key must be kept away from the reach of cybercriminals to protect the server and user’s information.
Public Key vs. Private Key
When you request an SSL certificate, two keys are created – a public key and the private key. These two keys are used to exchange the browser and the server’s data safely. When a visitor lands on a server, the user’s browser sends the information to the server. This data is encrypted with the public key to keep it safe from attackers.
The server then utilizes its private key to decode the data and sends the response to the browser. The reply from the server is also encoded. In this way, both keys work together for a secure data transmission between the user and the server.
How do you create a Private Key for SSL Certificate?
The private key is created along with the certificate signing (CSR) code. The CSR code contains all your business information like domain name, email address, physical location, country, organization, and state. It also comprises the public. CSR code is later sent to the certification authority for validation, and the certificate is issued after complete verification.
The private key is produced during the generation of the CSR code, and it must be kept secret. It is always good to keep the secret key secure on the same server on which you want to install the SSL certificate. Once the SSL certificate is granted to you, you can install it for safe data transmission on your website.
Can I Generate a New Private Key for my SSL Certificate if I Lose the Old One?
A private key has a corresponding public – validated by the certification authority (CA). When you generate the CSR code, the private key is also created. The CSR code comprises the public key you share with the CA to get an SSL certificate.
As these two keys are connected to each other, you cannot create a new private key for the same SSL. As you already have a validated public key, creating a new private key would not make any sense. That’s why it is advised to keep the private key secure.
If you have lost or misplaced the private key, you must reissue the SSL certificate, and for this, you will need to generate a new CSR code and the private key. Ensure that you have generated a strong and complex private key, unlike the public key. If someone (possibly a hacker) gets their hands on your private key, then the whole data on your site can be compromised.
What does the Private Key Look Like?
A private key is a long string of random letters and numbers. This encoded piece usually starts with —–BEGIN RSA PRIVATE KEY—– and ends on —–END RSA PRIVATE KEY—–. In many cases, you would not get any idea about the private that when was it generated and where it is. It is created along with the CSR code in the background and secretly stored in the server.
When you receive the SSL certificate, the key should be fetched automatically to install the certificate successfully. But sometimes, you have to install the SSL certificate on another server while you have generated the key on a different server. In such cases, you really need to know the exact location of the private key.
How to retrieve a misplaced private key?
If you have received an SSL certificate but don’t know the location of your private key, then here is some information that will help you. If you have lost or misplaced the private key, then the first thing you must do is to check the certificate’s information. In the certificate box, click on the General tab, and you will find the details of the key at the end of the box.
In the case of an activated private key, you will have a message like, “You have a private key that corresponds to this certificate.”
There will be no information displayed there in case of a misplaced or inactivated private key. There can be more than one reason for this like:
- The SSL certificate is not activated on the same server on which the CSR code was generated
- IIS (Internet Information Services) has deleted the pending request
- The certificate was not installed correctly, i.e., they might have used the Certificate Import Wizard rather than IIS
No matter the reason, the technique to find the misplaced private key differs depending on the operating system. There isn’t a method that works for all operating systems. Instead, you should follow the instructions designed for your operating system. Keep reading this guide to find private keys based on your operating system type.
Looking for a private key, especially when creating the CSR in -browser.
You can generate the private in the browser for all SSL certificates except the multi-domain SSL certificates. In the case of a multi-domain SSL certificate, you have to generate the CSR on the server, so skip this part if you have generated the CSR on the server.
If you have created the CSR code in-browser, you can find a private key in your computer’s downloads folder. When you create the CSR code in your browser, the secret is automatically downloaded as a zip file to the Download’s folder of the system.
If you cannot find the private key there, then check your browser’s settings. You may have set a different location for the downloaded files. Go to that folder, and your private key will be saved there.
The private key comes as a zip file to quickly locate it. It will have the name of your domain and the word “key” with it. For instance, if your domain name is “example.com,” then the file name will be “example_com_key.zip.”
If you still cannot locate your private key, search the file name (example_com_key.zip) on your computer. If still nothing happens, then you will require reactivating your SSL certificate. Because when you generate the CSR code in-browser, the private key is stored in your system, and it must be found there. If not, you will need to reissue the certificate because you cannot restore it by other means.
How to recover a private key on various server platforms?
As already mentioned, there isn’t a method of retrieving the private key that works on all the server platforms. You will need to implement the technique based on your operating system. Here we will cover all the following server platforms:
- Linux operating systems (Apache, Nginx, Lighttpd, Heroku
- Tomcat (using keytool)
- cPanel
- Plesk
- Synology NAS DSM
- Webmin
- VestaCP
- WHM
- DirectAdmin
- Webuzo
- Windows operating systems (IIS, Exchange, Small Business Server)
- Mac OS X
Linux operating systems like Apache, Nginx, Lighttpd, Heroku platforms
The private key is created with OpenSSL on Linux operating systems and is located as a text file along with .key and .pem extensions. But it is to be noted that extensions are not compulsory for text files in Linux-based operating systems, so your private key can be placed anywhere with any name and extension. That makes it quite hard to find the private key in Linux operating systems.
If you know the complete or half name of the key file, then you can start the search by entering the following command in the console:
sudo find / -name ‘example.key’
With this simple command, you can find the private key if it is available on your server. The “/” sign in the code shows that the search will start from the root directory. This way, you will be able to access all the files, and the chances of retrieving the private key are increased.
The ‘example.key’ command shows the assumed name of the secret key. You can write the file name you remember with the “.key” extension here. Use *.key command if you wish to find the files with a particular command. This command will return all the files with the .key extension.
Most of the time, the name of the private key starts with your domain name. For example, if your domain name is example.com, then the name of your secret key should be “example_com.key” or “example_com.pem.” To search private key in Linux OS, use your domain name or any other name in the console that you keep in mind.
If you still cannot find the private key after using all these methods, here is the ultimate way to retrieve it.
Use the following command in the console.
grep -r --exclude-dir=log --exclude-dir=ssh --exclude=*history -I -l -e '-----BEGIN PRIVATE*' -e '-----BEGIN RSA*' -e '-----BEGIN EC*' [search_start_folder] 2> /dev/null
This command will search for the files that start with this expression “—–BEGIN header” and will return the complete path to the file if it is available on your server.
Windows operating systems as IIS, Exchange, Small Business Server platforms
On Windows operating systems, you don’t have the freedom to view or retrieve the private key in the text format. When you import your SSL certificate using MMC (Microsoft Management Console) or ISS, the private key is automatically fetched, and the certificate is installed. This only happens when you have imported the certificate on the same server that generated the CSR code and the secret key.
But if you need to install the certificate on a different server, you will need the private key. You need to do the following steps to retrieve your private key on the Windows operating system.
- Press “Window + R” simultaneously and click OK
- Click on the “File” tab in the new window
- Choose “Add/Remove Snap-in,” click on the “Certificates.”
- Click on Add
- Select the “Computer Account” and press on “Next” button
- Click on “ Local Computer” and press the “Finish” button, and press OK
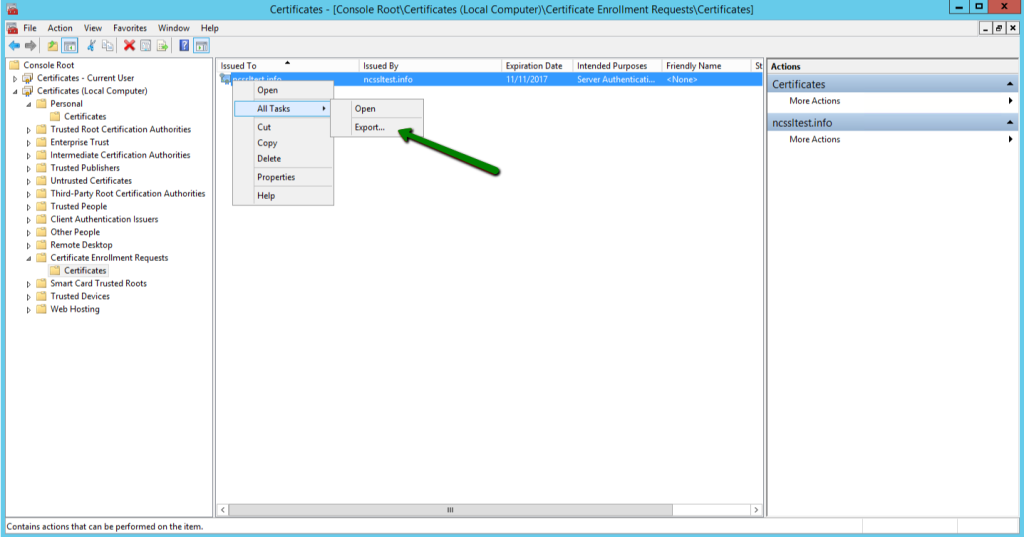
After this, move to the Certificate Enrollment Requests and click on Certificates. This is for the people who have not finished the certificate request yet. If you have already completed the certificate request, click on Personal and then Certificates. Under All Tasks, right-click on the certificates and click on “Export.” This will open the Export Wizard with instructions to follow.
After doing all these steps, you will see a “.pfx” file. This file comprises all the data about the SSL certificate and the private key as well. You can convert the private key into a text file by using an online tool.
Mac OS X
The Mac OS X operating servers have a default “Keychain” tool that prohibits retrieving the created secret key via the graphic user interface. However, you can use the following commands to access the /etc/certificates/ directory, where you can find the private key file.
cd /etc/certificates/ ls sudo nano test.key.pem
The name of the private key file should look like“*.key.pem.”
Tomcat (using keytool)
If you are using the Tomcat operating server, the private key should be in a key store file with a .jks or .keystore extension. The keystore file will be password protected, and this technique is only applicable if the SSL connector on your server is configured in JSSE style and not in APR style. So, better confirm the configuration first before going ahead.
To get the secret key in pem format, you must first convert the key store file into a PKCS#12 (.pfx/.p12) file. You can do this by entering this command.
keytool -importkeystore -srckeystore keystore.jks -destkeystore keystore.p12 -deststoretype PKCS12 -srcalias -srcstorepass -srckeypass -deststorepass –destkeypass
After generating the .pfx/.p12 file, you can convert it into a PEM format using an online tool. You can also utilize the below-mentioned OpenSSL command to convert it into a PEM format:
openssl pkcs12 -in keystore.p12 -nocerts -nodes -out private.key
The “private.key” at the end of the above command tells the name of the file on which the text of the secret will be saved.
cPanel
On the cPanel operating server, you can retrieve the private key using two different methods.
a) SSL/TLS Manager
Open the cPanel home page and click on “SSL/TLS Manager.” Select the “Private Keys” tab, and the new window will open. In this window, you will see all the details of private keys on your account. You can select a key and click on the “View & Edit” button to see it in encrypted and decrypted forms.
b) File Manager
On the cPanel homepage, click on the File Manager. A new window will pop up. Find the “SSL” folder on the left side and click on it. Select the “keys” folder inside it. All the private keys on your account will come out on the right side of the window. You can either download or view a secret key in text mode.
WHM
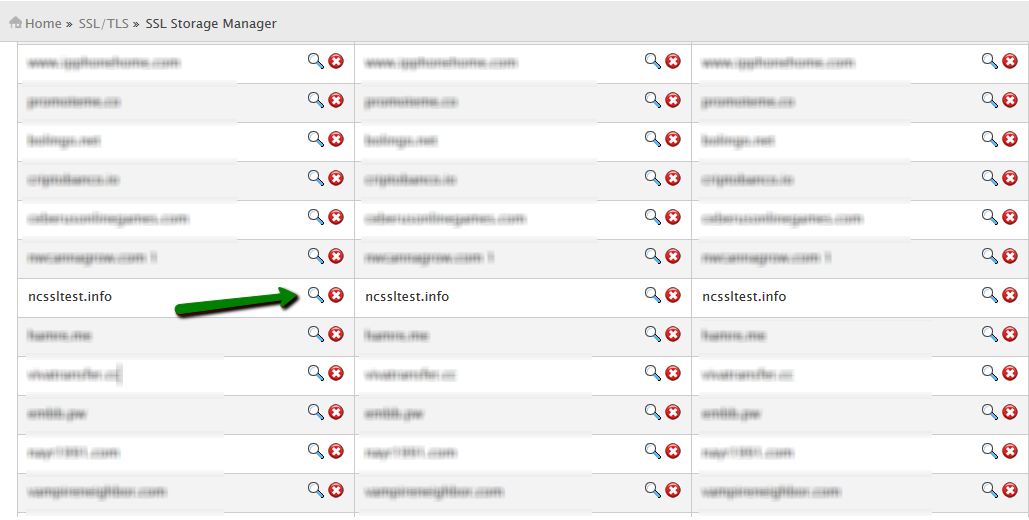
In WHM operating servers, the secret key is saved along with the CSR code and certificates. You can find all these in SSL Storage Manager. You can reach there by clicking on the SSL/TLS tab on the home screen and then selecting the SSL Storage Manager.
You will find three different columns (one each for the key, CSR code, and certificate). Click on the Magnifier button to open the key in the text format.
Plesk
If your operating server is Plesk, you will first require clicking on Domains on the home screen. Then click domain.com and finally on SSL/TLS certificates. You can find a key at the left bottom corner, and it states that “Private Key Part Supplied.” It means the needed private key, which means the required key is available on the server.
You can get this key by two means. First, click on the name and go down until you get the private key. Second, press the green arrow on the right bottom corner of the screen. This will download a .pem file that you can open in Notepad. This .pem file will also contain the CSR and the certificate along with the secret key.
Synology NAS DSM
Retrieving the private key in the Synology DSM operating server is relatively easy. The private key on this server is created/downloaded at the last step of CSR creation. The private key is downloaded in a .zip file and saved with the file name server.key inside it. You can easily open this file on Notepad or any other text editor on your system.
Webmin
This panel was created as a GUI (Graphic User Interface) above the command-line interface. You will also see a Filemin (file manager) there, which you can utilize to find a private key. The other way to retrieve the private key on Webmin is to open the Command Shell and run any of the following commands:
sudo find / -name ‘normal.key’ grep -r --exclude-dir=log --exclude-dir=ssh --exclude=*history -I -l -e '-----BEGIN PRIVATE*' -e '-----BEGIN RSA*' -e '-----BEGIN EC*' [search_start_folder] 2> /dev/null
VestaCP
When you generate the CSR code on this panel, the private key must be saved in text format. You have to do this because it is not stored anywhere on the user interface.
However, there is still a chance to retrieve your private key on this panel. The secret key is stored temporarily in a folder when you generate the CSR on this panel. The exact path to this file can be similar to this “/tmp/tmp.npAnkmWFcu/normal.com.key.”
The main problem here is that whenever you reboot the server, the files in the “/tmp” directory are deleted, so there is a possibility that you will lose the private key.
You can use the following command to find the secret for your domain (for example, example.com)
find /tmp -type f -iname 'example.com.key'
If you are unable to find the private key, you can use the “grep” command here as well.
grep -r --exclude-dir=log --exclude-dir=ssh --exclude=*history -I -l -e '-----BEGIN PRIVATE*' -e '-----BEGIN RSA*' -e '-----BEGIN EC*' [search_start_folder] 2> /dev/null
DirectAdmin
If you are using the up-to-date version of DirectAdmin, then you can find the private key in your system. The private key will be retrieved in the “Paste a pre-generated certificate and key” part in the SSL certificates area. It is good to check the private key before pasting the certificate text in that section. If the private key is not available, it tells that the CSR was created on a different server, or it can also be a system fault. If it is a system glitch, then the private key can be found in the following directory:
/usr/local/directadmin/data/users//domains/.key
Webuzo
Find the “SSL Management” section on the home screen of Webuzo and click on it. You will see a “Private Keys” button there. Click on it to see all the private keys created on this panel. To see the secret key in text format, click on the pencil icon on the right side of the screen.
Conclusion
The private key is crucial in cryptography, and it must be kept safe. If you have accidentally lost or misplaced it, you can take help from this article. If you are still unable to find a private key, it’s best to generate a new CSR code and the private key and reissue your SSL certificate. Make sure that you keep the private key safe this time.