If you’re a software developer, or a cyber security professional, you probably already fully understand the importance of protecting sensitive data and cryptographic operations. Cyberthreats and data breaches are on the rise, emphasizing the need for robust security solutions.
One such solution is Hardware Security Modules (HSMs). These specialized devices play a critical role in safeguarding digital assets and cryptographic keys. Among them, the Luna Network HSM stands out as an exceptional hardware-based security solution.
What is Luna Network HSM?
Luna Network HSM, offered by Thales, is a cloud-based Hardware Security Module (HSM) that takes digital asset protection to new heights. HSMs are specialized hardware devices equipped with cryptographic processors, specifically designed to manage digital keys and perform secure cryptographic operations.
Their primary purpose is to create a secure environment where encryption keys can be generated, managed, and used, ensuring they remain isolated from other system components for heightened security. Essentially, HSMs safeguard an organization’s most sensitive digital assets.
The following are the advantages of Luna Network HSM
Enhanced Data Privacy
HSMs play a crucial role in preserving data privacy by ensuring that sensitive information remains confidential and inaccessible to unauthorized entities. With dedicated cryptographic processors, HSMs perform cryptographic operations within their secure environment, preventing any leakage or exposure of sensitive data.
They protect encryption keys and cryptographic operations to thwart potential attacks aimed at stealing valuable data, providing businesses and their customers with peace of mind.
Secure Cryptographic Operations
HSMs act as a fortress for cryptographic operations, ensuring that these processes occur in a secure and tamper-resistant environment. From generating and storing encryption keys to performing cryptographic computations, HSMs mitigate the risk of unauthorized access and tampering.
This secure handling of cryptographic operations instills trust in digital transactions, making HSMs a vital component in securing online communication, financial transactions, and data transfers.
CSR and Key Attestation Creation for the Luna Network HSM
Key attestation ensures the legitimacy of cryptographic keys and guards against tampering with them. In this critical area, Luna Network HSM excels at generating robust key attestations that serve as irrefutable proof of a key’s integrity and security.
At the heart of Luna HSMs’ key attestation capabilities lies the Public Key Confirmation package (PKC). For the verification of specific key pairs stored securely within them, Luna HSMs only needs to generate PKC files.
These PKC files are structured in the DER-encoded PKCS7 format, and they contain essential information about the key attestation. Ensuring compatibility with the key attestation service is crucial, and that’s why PKC files are encoded in base64 format.
The use of base64 encoding allows for seamless integration and communication with other systems that rely on key attestations for trust verification. For RSA key pairs, there are two common formats for PKCs that are often mentioned: TC-Trust Center and Chrysalis-ITS.
The TC-Trust Center format consists of three certificates within the PKC, but it does not include a root certificate at the end of the certificate chain. On the other hand, the Chrysalis-ITS format boasts five certificates in the PKC structure.
Also, there is a root certificate at the end of the certificate chain. In practice, the steps for generating a CSR and key attestation using Luna Network Attached HSM 7.x involves following the prescribed guidelines for creating PKC files in an RSA key pair context.
These guidelines ensure that the PKC is generated accurately and with all the necessary information to verify the integrity and authenticity of the key.
Process using Chrysalis-ITS Format
Securing digital assets requires a meticulous approach, and Luna Network HSM’s Chrysalis-ITS format is a key component in this endeavor.
Organizations can ensure the authenticity and integrity of their cryptographic keys by generating a Certificate Signing Request (CSR) and a Public Key Confirmation (PKC) using Chrysalis-ITS. Here’s a step-by-step guide for this process:
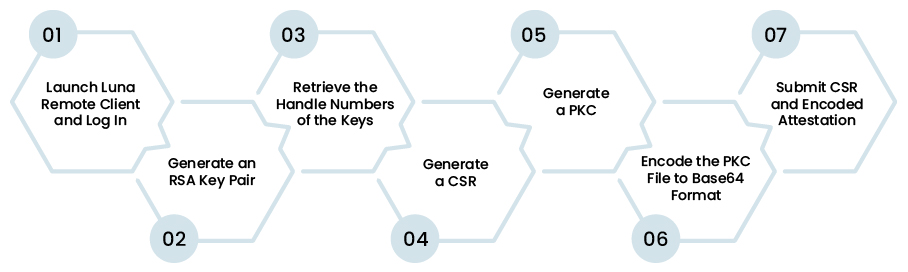
Step 1, Launch Luna Remote Client and Log In
To begin the process, access the Luna HSM by launching the Luna remote client. After logging in, you gain entry to the secure environment where cryptographic operations will take place.
Step 2, Generate an RSA Key Pair
Using the LunaCM2 utility, create an RSA key pair on a designated Luna Partition. Depending on your operating system, execute the appropriate command.
For Windows, navigate to the LunaClient directory and use the following command:
c:\ cd c:\Program Files\SafeNet\LunaClient
c:\Program Files\SafeNet\LunaClient\> lunacm
For Linux users, go to the bin directory and run the command as follows:
>cd /usr/safenet/lunaclient/bin
./lunacm
Now, generate the RSA key pair by using the “cmu gen” command. Make sure to replace “LABEL” with a suitable identifier for your key pair.
cmu gen -modulusBits=3072 -publicExp=65537 -sign=T -verify=T -label=LABEL -extractable=false
It is essential to note that the parameters “-extractable=false” and “-sign=T” are mandatory for successful CSR generation. These settings ensure that Luna HSM will not use this key for signing the CSR. Additionally, for code signing certificates, the RSA key size must be at least 3072 bits.
Step 3, Retrieve the Handle Numbers of the Keys
Next, retrieve the handle numbers of the public and private keys by executing the following commands:
cmu list -class public -label=LABEL
cmu list -class private -label=LABEL
These handle numbers are crucial for the subsequent steps in the process.
Step 4, Generate a CSR
With the handle numbers at hand, it’s time to generate a CSR using the “cmu requestcert” command.
Customize the command by replacing “MNO” and “BCD” with the respective public and private key handles. Set other relevant parameters, such as the country (C), locality (L), organization (O), common name (CN), and output file name for the CSR. For example,
cmu requestcert -publichandle=MNO -privatehandle=BCD -C=CA -L=Ottawa -O=Sectigo -CN="PKC Test Cert" -outputFile=rsacsr.pem
Step 5, Generate a PKC
The next step involves generating a PKC to verify the authenticity of the key pair. Use the “cmu getpkc” command. And, replace “MNO” with the public key handle. For “attestation.p7b“, replace it with the desired file name.
cmu getpkc -handle=MNO -outputfile=attestation.p7b -pkctype=2 -verify
Step 6, Encode the PKC File to Base64 Format
To ensure compatibility and smooth communication with other systems, the attestation PKC file needs to be encoded in base64 format. Below command should be used, subject to your operating system:
- For Windows:
certutil -encode attestation.p7b attestation.b64
findstr /v CERTIFICATE attestation.b64 > attestation.b64
- For Linux:
base64 attestation.p7b > attestation.b64
Step 7, Submit CSR and Encoded Attestation
With the CSR and base64-encoded attestation ready, submit them to the Sectigo (the CA e.g.) key attestation service or reseller-website enrollment form. This submission verifies the authenticity of the HSM, enabling the issuance of code signing certificates.
In Closing
Luna Network HSM offers a solid solution for generating CSRs and Key Attestations, significantly enhancing security in corporate environments. Cutting-edge security solutions like Luna Network HSM allow businesses to fortify their digital assets, maintain data integrity, and stay one step ahead of cyber adversaries with less stress. To build a secure future for your organization, embrace the power of HSMs.