A brute force attack is a type of cyber-attack, where attackers try to work out all the permutations and combinations by testing every key and finding the correct combination of passwords and paraphrases.
The name itself suggests that brute force attacks are done with extreme force to penetrate systems for gaining personal information.
This is an old but effective method, which is loved by hackers, not because it’s quick, but because such attacks are mostly successful. Let me brief you that depending on the length of passwords as well as their complexity, the time required for cracking the password may vary from a few minutes to a few years.
Types of Brute Force Attacks
Attackers are becoming more sophisticated and use varied types of brute force attacks to penetrate the websites. Let’s check them out.
Rainbow Table Attacks
A rainbow hash table is used to find out the output of cryptographic hashes for penetrating the passwords which are secured in the database. Each password has a unique hash and these table attacks don’t ambush the passwords; they attack the hash functions which encrypt these passwords.
Dictionary Attacks
In this attack, the attacker selects a target and guesses all the probable password combinations against the username of the target. The hacker predicts the passwords by using a unique word dictionary, special characters, strings, or numerals.
Simple Brute Force Attacks
This attack is made by using automation, wherein the hackers use software tools and scripts to guess passwords. Easy passwords, pins, etc. are all revealed by these tools.
Example of a Simple Brute Force Attack
| Username | Password | Attempt Status |
|---|---|---|
| Manager | B123456 | Failed |
| Manager | BB12345 | Failed |
| Manager | BBB1234 | Failed |
| Manager | BBBB123 | Success |
When a brute force attack is made on a ciphertext, the hacker tries all the probable keys for breaking the ciphertext. Even random selection of half of the keys will make the original (plain) text appear and increase the chances of a successful attack.
Hybrid Brute Force Attacks
External ideas + Brute force attacks = Hybrid brute force attacks
Hybrid brute force attacks are a combination of external (dictionary) ideas to guess the best possible variations in the passwords.
Reverse Brute Force Attacks
When a password is leaked, hackers instantly take advantage of the situation and start searching the username.
They use this single known password against unlimited usernames, with the motto to find a matching username for penetrating networks.
Credential Stuffing
Here the hacker is aware of the username-password combination and uses the same for exploiting multiple websites. Using this leaked login credentials combo, they try to gain unauthorized access into these accounts via automated login requests which are directed through web applications.
Motives Behind Brute Force Attacks
Hats off to these hackers and their patience for waiting for months and years to carry out a successful brute force attack by cracking passwords or encryption hashes.
But why do they wait for so long? What are their motives and what motivates them to wait?
Of course, massive rewards are the sole reason for the same. Let’s check them out in detail.
Exploit Ads
When a brute force attack is instigated on a website by the hacker, one of their aims is to earn finances from advertising commissions.
Implanting spam ads on a website to gain money on every click, rerouting traffic to a fake website having multiple ads, infecting the site with malware to gain data for selling it in the black market, etc. are some of their motives.
Steal Sensitive Data
Hackers hack personal accounts and invade data privacy by accessing banking details and other financial information. They later imitate the user’s identity to steal finances and credentials for selling the same or launching more attacks.
Inject Malware
These attackers inject malware or spyware and infect the websites. They later redirect customers to malicious sites or create a mirror website infected with malware to trick customers into punching their sensitive details.
Hijack Systems
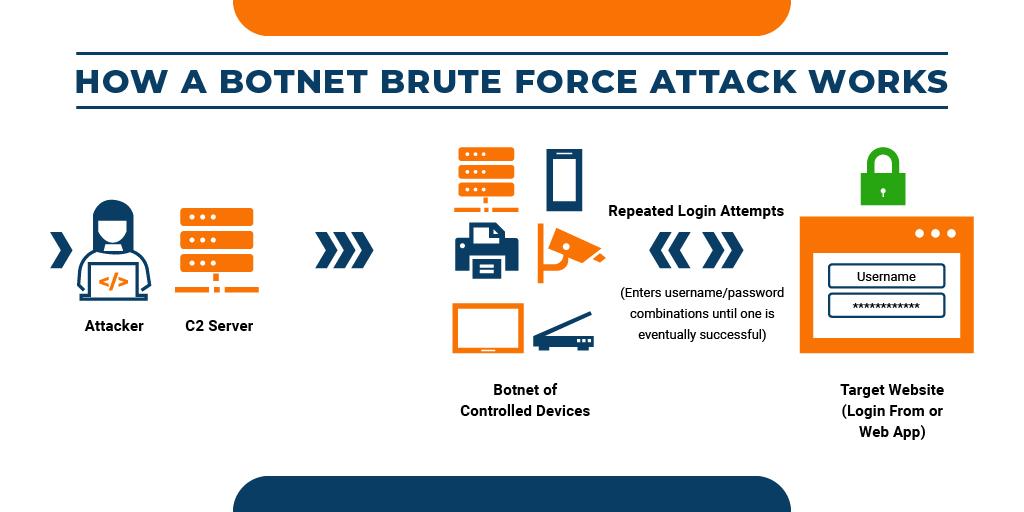
At times, these hackers launch massive attacks by using multiple gadgets called botnets. This is similar to a DDoS (distributed denial-of-service) attack, mainly aimed at the defense systems of the website.
Damages Company Reputation
Bad actors sometimes apart from financial gains try to ruin a company’s reputation by implanting obscene images or text on the website. This not only defames the site’s reputation but also compels the site owners to remove their website from the internet.
A Brute Force Attack Example
When a password comprises a single character and is inclusive of numerals and letters, it requires approximately 62 combinations to be cracked. Normal passwords are of 8 characters or more, and there are millions of possibilities that need to be explored for cracking the same.
In the previous years, a hacker would take at least 7 million years for cracking an 8-character password if we assume that one attempt takes a second.
But in the current scenario, using brute force bots, these hackers can crack the same in a few seconds, just like a supercomputer, which uses only 1 second for inputting 1 trillion combinations.
Examples:
- Imunify Security states that a massive brute force attack took place on July 24, 2020 wherein 15 million unique requests were blocked.
- Flashpoint reported atleast 1,000 websites running on Magento platforms were targeted via brute force attacks for gaining credit card details and installing malware.
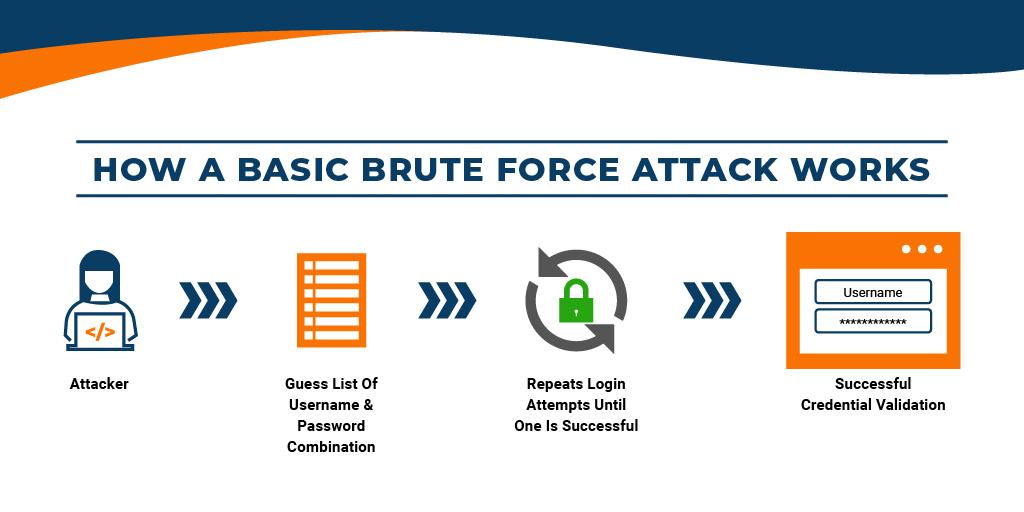
How Brute Force Attack Works:
In this type of attack, the attackers use bots to predict password combinations. They have a common list of combinations and login details that are designated to their bots for attacking the websites.
The attacker manually guesses the credential details or other user logins which may be obtained through the dark web or any other security lapse.
Guesses may be time-consuming and since attackers are impatient, they take the help of software or other brute force tools to get multiple combinations for invading the website. With the aid of these tools, these attackers can attempt multiple password combinations and session ids for accessing the website and other applications.
Top Brute Force Tools
- Aircrack – ng: A password dictionary is used by this tool to breach networks and can function on all platforms like Windows, Linux, iOS, and Android.
- John the Ripper: This open-source password recovery tool can be used on multiple (15) platforms and braces ciphers, hashes, and passwords.
- Hashcat: This versatile and efficient password hacking tool is used for illegal purposes and works on Linux and Windows platforms. This tool assists the hacker to conduct the attack by predicting and hashing the password.
- Ncrack: This is a speedy network authentication cracker tool that is used on multiple platforms.
What are the Strengths and Weaknesses of Brute Force Attacks?
Brute force attacks are simple to implement and successful as compared to other hacking attempts. Each password, encryption key, and hashes can be penetrated by using brute-force attacks.
Brute Force Attacks Strengths
- It’s simple. Why should attackers find back doors, when they can open the front doors to access networks? Intruding legitimate accounts is quite easy via brute force as compared to other hacking attempts.
- Brute force attack tools simplify the cracking process of usernames and passwords, thus making it easy and inexpensive.
- Public (51%) uses simple, easy to guess (123456-used by 23 million account holders) and the same password for multiple accounts.
- Automation and scripts are an added advantage for accessing networks in an unauthorized way.
- Bots and zombies also make the password cracking process quick (few seconds) and easy.
Brute Force Attacks Weaknesses
Website owners also find ways to resolve the strengths in brute force attacks and nullify the same.
- Since brute force attack relies on easy to guess and weak passwords, the same can be rectified by the website owner to prevent network breaches and intruders
- When constant monitoring of unsuccessful login attempts is done from similar IP addresses, the same can be blocked to prevent further damages.
- When 2FA or MFA is used, this attack becomes unsuccessful because, even if the password is cracked, the multiple layer security barriers make it difficult for the hackers to surpass and penetrate networks.
- These attacks can sometimes be very time-consuming (takes years for a successful attack) and may require extensive tools and research.
- The defense mechanisms and the below-mentioned tips can help weaken these attacks and prevent them.
Quick Tips to Prevent Brute Force Attacks
Brute force attacks or password attacks can be prevented by following some simple practices.
Complex Passwords
Increase password length and complexity and use different passwords for different accounts. Encrypt these passwords and use a cryptographic trick (salting the hash) for making the attack process very difficult to succeed.
Change the Login URLs Regularly
Keep on changing the login URLs for web apps and services to prevent automated brute force attempts.
Limit Access
Limiting access to accounts reduces the vulnerability of brute force attacks. By locking the accounts on unsuccessful login attempts, and later unlocking an account by the administrator can prevent this attack.
Example: After 3 unsuccessful login attempts, the account will be locked and the same can be unlocked by the admin guy only.
Progressive Delays
When accounts are locked for a specified time after each unsuccessful attempt, keep a small timer after each login attempt, i.e., the next attempt can be done after a specified time only. The delay in the re-attacking process forces the attacker to focus elsewhere.
Use MFA
The use of multi-factor authentications can prevent these attacks and stop password leaks. Since another security needs to be surpassed, like a fingerprint or a facial scan or a security question to access the accounts, hackers tend to skip such accesses.
Use CAPTCHA
The use of CAPTCHA during the login process can prevent intruders from forcing their way into the networks. CAPTCHA includes typing images, catching images, or identifying objects.
When the CAPTCHA option is enabled, its verification will be required in each login effort.
Remove Unused Accounts
Why keep an open gateway for attackers? They sometimes use expired and unmaintained accounts for invading networks. Remove all the unused accounts and logins given to employees (who have left the firm) to prevent such brute force mishaps.
Wrapping Up
To ensure the safety of your network and systems, it’s advisable to take the necessary preventions and monitor your networks and traffic for suspicious activities.
Sophisticated and skilled hackers always find ways to penetrate networks. Their final motto is to cause a denial of service and extract information, but these attackers may change their tracks and target elsewhere when they find wrenches in their routes.
To defeat them in their process, it’s essential to implement the prevention techniques and save yourself from becoming a victim of brute force attacks.
The use of strong passwords, and encrypting these passwords with 256-bit encryption algorithms makes it difficult for the hackers to crack the passwords.
Monitoring server logs, making the root user unreachable through SSH, avoiding the use of default port, and using unique URLs may prevent these brute force attacks and secure your networks from these attackers.
Related Articles: