In a time in which doing business digitally has become subject to all manner of sophisticated attack and exploitation, zero-day attacks represent a particularly urgent sort of threat to companies. The need for vigilance and caution only increases as the world of malware and viruses becomes increasingly developed and complex. With every step forward that developers seem to make in terms of protecting their software, it seems that hackers and malware developers manage to stay one-step ahead.
Zero-day attacks are in news and more increased nowadays than it was ten years ago, or twenty years ago in the nineties. Malware has evolved to be much more dynamic and zero-day attacks are an example of this unfortunate, but fixable, situation.
What is Zero Day Attack?
Zero-day attacks are malware attacks, which exploit a previously unknown flaw or vulnerability in software coding. A zero-day attack takes advantage of the window of opportunity to strike before the developer has patched the vulnerability. The size of this window of opportunity depends on the response of the attacked company and on the response of the software developer in quickly patching the problem. The term “zero-day attack”, it arises from the idea that software developers have zero days to defend and protect their software, once hackers and malware writers have discovered the vulnerability.
What Symantec Says about Zero Day Attack?
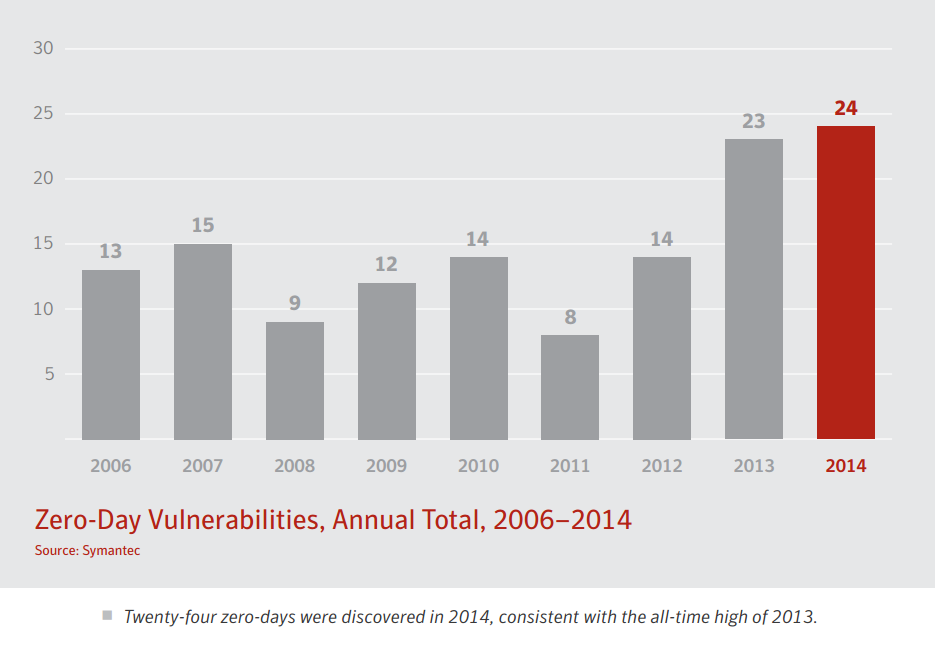
According to Symantec research, Zero-day attacks increased greatly in the period from 2013 – 2015. From 2006 to 2012, the number of zero-day attacks per year changed between minimum 8 and maximum 15. In 2014, the number of zero-day attacks spiked all the way 24.
In September of 2013, Internet Explorer had a zero-day vulnerability exploited – with an attack that allowed hackers to remotely control the computers of Internet Explorer users. In the fall of 2014, Microsoft Windows itself also became a victim of zero-day attacks where hackers had accessed the rights and privileges of Windows users. Adobe flash player was hit with such attacks in early 2015. The attacks, hidden for two months, linked users to malware websites with fake advertisements. The zero-day threat is certainly a growing one.
The main reason the threat is growing is the increased skills and understanding of modern day hackers. These days, malware tends to be designed to self-propagate in a matter of days or hours, and with the goal of affecting a much larger number of systems. Truly modern attacks, such as the Warhol and Flash threats, are designed to propagate and infect many systems in a matter of minutes. Hackers now have a better understanding of the vulnerabilities themselves, and how to exploit them. Put simply, the world of hacking and malware is simply better developed than it was ten or twenty years ago. Companies of any size must be aware and ready to spot and defend from such zero-day attacks. More so than any other attack, time is of the essence in the case of a zero-day attack.
Signs of Zero Day Attack:
Even though it is inherently difficult to spot zero-day exploits before they are known to public, and likely exploited, there are signs and symptoms to keep an eye on, including:
- Unaccounted for traffic and scanning activity from a certain server or client.
- Unexpected traffic in general.
- Unchanged behavior from a compromised server, even after applying a patch or fix
Zero Day Preventions Tips:
By the nature of zero-day exploits, no company will be able to be one hundred percent secure from them. However, with knowledge, planning, and vigilance a measure of prevention can be achieved. Such preventative measures include:
- Keep firewalls up to date, and matched to current business needs.
- Block suspicious file attachments.
- Keep all systems updated against identified vulnerabilities.
- Vulnerability scanner requires assessing the effectiveness of previous security measures.
- Choose a quality anti-virus program that can emulate future, currently unknown threats, in a cloud-based atmosphere, before allowing them to reach your computer.
- Keep all anti-virus programs up to date, take note if the update is described as “critical” – Automatic updates will almost always be a desirable option.
- Make sure to only use updated browsers – since web browsers are particularly vulnerable. Most will update automatically when opened and closed, so if your browsers are left open for long periods, be sure to accept prompts to manually update.
- In general, never install needless software. Review existing software, and don’t keep anything unnecessary.
- Utilize inline-prevention systems (IPS) for real-time prevention – it should include network protection, application reliability, application protocol Request for Comment (RFC) validation, content validation, as well as forensics capability.
- Implement a well-planned incident response, with distinct roles, priorities of action and procedure. By their very nature, no company can be one hundred percent to avoid all zero-day attacks, so a well thought out incident response plan is key.
- Implement a plan to slow or stop the spread of such an attack once it hits. Limit connections to only those necessary for doing business.
- Monitoring applications and their behavior in real time using machine-learning techniques are welcomed.
Zero-day attacks can be a possibility in today’s sophisticated and profitable world of malware development. Proper security measures as given above are about minimizing this possibility of the damage once the zero-day vulnerability has already been exploited. Besides, companies need to take an active role in developing responses plans, keeping software updated, and educating employees to make basic safe decisions online.