SSH vs SSL: here we are exploring similarities and differences between SSH vs TLS/SSL protocols.
SSH and SSL/TLS are both protocols that employ Asymmetric cryptography. These security protocols are intended to keep your personal information private during data transmission and secure communication over the Internet and public networks.
SSH (Secure Shell) and SSL/TLS (Secure Sockets Layer / Transport Layer Security) share similar security aspects – encryption, authentication and integrity processes. However, they have distinct purposes.) share similar security aspects – encryption, authentication, and integrity processes. However, they have distinct purposes.
For instance, when you access a website with SSL/TLS, the data you send, like login credentials or payment information, is encrypted for privacy. Similarly, SSH is used when a server is being accessed and managed remotely. It ensures that commands and sensitive data sent between your device and the server stay private.
If you’re exploring SSH vs. SSL/TLS, here we will break down the similarities and differences between SSH vs SSL/TLS to clarify how each protocol works.
What is SSH? How does it work?
Secure Shell (SSH) is a cryptographic network protocol that enables secure data communication over an unsecured network. In contrast to e.g. Telnet or FTP transmission protocols, which transmit data in their native (plaintext) state, SSH encrypts the data, so sensitive information such as login credentials, commands, or files are reliably transmitted. It is widely used in system administration allowing administrators to connect to servers and devices over a secure connection, execute commands, transfer files, and manage resources.
How Secure Shell (SSH) Works
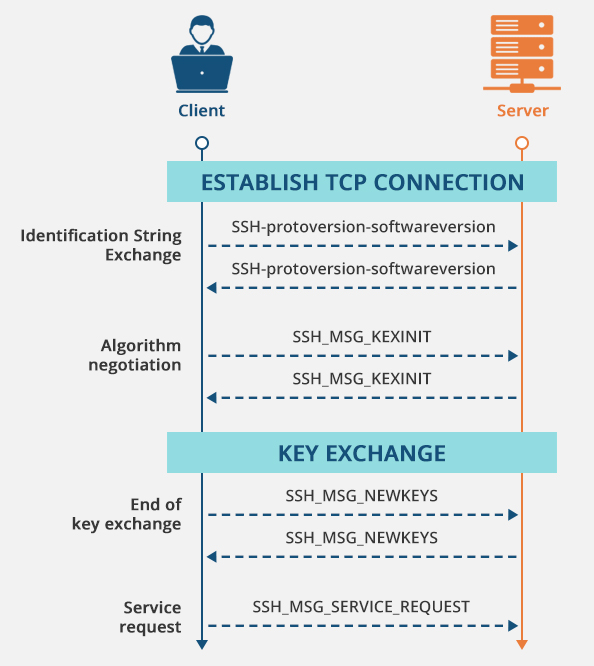
When a client (a laptop or terminal) makes a connection to a remote server using SSH, that client goes through a few authentication and encryption steps in order to ensure that communication is secure.
-
Establishing a Connection
- Whenever the SSH client establishes the connection, it communicates with the SSH server on a specified port (Port no: 22)
- Both the client and server exchange information on supported encryption and compression algorithms to make sure they’re compatible.
-
Server Authentication
- The server sends a public key to the client, which in turn is used by the client to verify the server’s identity. The client will usually cache this key if a successful connection is established to keep future connections secure.
- The client raises a warning if the server’s key changes unexpectedly, allowing it to detect “man-in-the-middle” attacks.
-
Client Authentication
- SSH allows clients to authenticate themselves using multiple ways such as password or key-based authentication methods.
- Key-Based Authentication: This is the most secure and preferable way. A pair of cryptographic keys is created (a public key stored on the server, and a private key stored securely on the client). During connection, the client uses its private key to sign a digital signature, and the server verifies the same against the public key object stored on the server and gets access without a password.
- Password-Based Authentication: The method is simpler but less secure, as it uses passwords that the users have to type in but are still encrypted during transmission.
-
Establishing an Encrypted Tunnel
- After the authentication is completed, the SSH uses symmetric encryption to establish a secure encrypted channel.
- The session key is agreed upon by both parties and used to encrypt data for a session.
- The encryption of this tunnel not only provides confidentiality (not being eavesdropped upon) but also integrity (guaranteeing tamper free).
-
Communication and Data Integrity
- Message authentication codes (like HMAC) are used by SSH to ensure that the data that has been transmitted hasn’t been altered.
- Commands, responses, and files passed back and forth over SSH are all protected with this encrypted session.
Example: Let’s say an administrator wants to log into a remote server to manage files. They open an SSH client like ssh in their terminal and enter the command:
ssh user@remote-server-ip
If the SSH client is configured to use key-based authentication, the SSH client will take the stored private key automatically and will use it to authenticate. After the SSH tunnel is established and you successfully log on, all commands and file transfers will run over the secure SSH tunnel.
Here is an illustration of an SSH handshake:
What are the use cases of Secure Shell (SSH)?
SSH has become a critical tool in modern IT infrastructure due to its versatility and security. Here are some in-depth use cases:
-
Remote Server Management
- When it comes to managing servers, especially remotely or in the cloud, SSH is what system administrators will use to access and work with remote servers. This means that they can actually perform necessary maintenance tasks like updating programs, monitoring logs, and configuring applications remotely.
- SSH also lets you execute scripts on remote servers securely without displaying commands or data in network logs.
-
Secure File Transfer
- SSH permits the secure transfer of files from and to local and remote machines using SCP (Secure Copy Protocol) and SFTP (SSH File Transfer Protocol).
- However, both use SSH’s encrypted tunnel whereby files cannot be tampered with or intercepted during transfer.
-
Port Forwarding and Tunneling
- SSH supports port forwarding, allowing users to tunnel traffic securely through SSH.
-
There are three types of SSH port forwarding:
- Local port forwarding: Redirects traffic from the client’s machine to a specified server through SSH.
- Remote port forwarding: Allows a remote server to forward traffic to a client.
- Dynamic port forwarding: Functions as a proxy, routing traffic to multiple destinations securely.
-
Automated Scripts and CI/CD Integration
- SSH enables secure automation by running tasks across multiple servers without requiring any manual intervention, all through scripts and CI/CD tools.
- In automated environments especially, key-based authentication is very useful, as it bypasses password-based login.
What is SSL/TLS? How does it work?
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are a protocol for securing communication over the internet by encrypting data from clients (web browsers) to their servers. SSL was developed originally to protect data like login credentials and payment information, but its successor TLS is used today widely, and SSL is considered outdated. An SSL/TLS connection uses the Public Key Infrastructure (PKI) and digital certificates to provide security and integrity to website transactions.
SSL certificates have various benefits
Encryption – It secures data during transit, making it unreadable to malicious actors trying to intercept it.
Authentication – It verifies that data is being exchanged with the right server, helping to clock man-in-the-middle attacks.
Data Integrity – SSL ensures that the data stays intact during transfer, preventing any loss or unauthorized changes.
SSL and TLS use digital signatures generated by Certificate Authorities to enable a trusting relationship between users and providers. Once the connection is established, it becomes possible to securely transmit sensitive information, such as might be passed between a bank and its customers. The standard TCP port used for Hypertext Transfer Protocol over SSL/TLS (HTTPS) is port 443.
How SSL/TLS Works
If a browser connects to a SSL/TLS enabled site, the server that is being visited sends its public key certificate to the client to be verified. Before using the certificate, the client checks to make sure that the server is legitimate by trying to verify it with a Certificate Authority (CA).
SSL/TLS operates on a client-server base model. Before a client and server establish a secure connection, they undergo an SSL/TLS handshake process. To understand this better, let’s take a browser connecting to a server process as an example and see how the handshake process works, specifically when using the RSA algorithm.
-
Client Hello
- When the connection starts the client (such as a browser) sends the “Client Hello” message to the server, providing the supported algorithm for communication, TLS versions, and any other options.
-
Server Hello and Certificate Exchange
- The server sends a “Server Hello” message and chooses compatible encryption methods to be used. It also sends a digital certificate containing its public key by a (trusted) Certificate Authority (CA).
- This certificate then gets verified by the client with the CA, that this is actually the correct server (e.g. an actual bank’s website).
-
Session Key Agreement
- Asymmetric encryption is used by both client and server to exchange a session key securely, methods such as the RSA algorithm is used for this purpose.
- Later, this session key is used for symmetric encryption, allowing faster, more secure transmission of the data.
-
Data Exchange and Encryption
- After the session key is established, all of the data that travels between the client and server is encrypted to maintain confidentiality, integrity, and authenticity.
- SSL/TLS also employs hashing algorithms (like SHA-256) to confirm data integrity, preventing tampering.
When you connect to a secure website (e.g., your bank), your browser and the website server complete this handshake process. After the handshake, any data you enter—such as your account information—is encrypted, making it safe from eavesdroppers.
What are the use cases of SSL/TLS?
SSL/TLS plays a crucial role in ensuring the security and integrity of data exchanged over the internet. Below are some key uses of SSL/TLS that contribute to maintaining secure communications and protecting sensitive information:
-
Securing Web Traffic with HTTPS
- SSL/TLS is used to encrypt web traffic using HTTPS (Hyper Text Transfer Protocol Secure). It guarantees that data transmitted from the user’s browser to the web server, and vice versa, is private, integral, and authentic.
- It also promotes trustworthiness as SSL/TLS-certificated websites assure users the site is secure and is marked in the browser with a padlock symbol.
-
Email Encryption
- Email protocols like SMTP, IMAP, and POP use SSL/TLS for encryption of communication.
- Doing so helps safeguard sensitive information that is sent via email, like confidential files or private messages.
-
VPN and Remote Access Security
- SSL/TLS based encryption is used by many VPNs (Virtual Private Networks) to provide encrypted tunnels between remote users and internal networks.
- The setup is extremely useful for remote work, giving employees safe access to corporate resources from public unsecured networks.
-
API and Application Security
- SSL/TLS is used by applications to secure API calls and data exchanges — including those that communicate with external services.
- It prevents man-in-the-middle attacks by which attackers otherwise intercept or manipulate data that is exchanged between systems.
SSH vs SSL/TLS – Differences Between Both Security Protocols
SSH and SSL/TLS generally have different purposes. SSH is often used by network administrators for tasks that a normal internet user would never have to deal with. SSL/TLS, on the other hand, is used by the average internet user all the time. Any time someone uses a website with a URL that starts with HTTPS, he is on a site with SSL/TLS.
| SSH (Secure Shell) |
SSL/TLS (Secure Sockets Layer/Transport Layer Security) |
|---|---|
| Operates over TCP port 22. | Operates over TCP port 443. |
| Used for securely executing commands on a remote server. | Used for secure communication between a client and a server. |
| SSH uses a username/password (mutual) authentication system to establish a secure connection. | SSL normally uses X.509 digital certificates for server and client authentication. |
| SSH is working based on network tunnels. | SSL is working based on digital certificates. |
| SSH is a remote protocol. | SSL is a security protocol. |
| It is used to reduce security threats for remote server login. | It allows secure transition of data between a server and the browser thus, keeps information intact. |
| SSH follows authentication process by server’s verification done by client, session key generation, and client’s authentication. | SSL follows authentication process by exchange of digital certificate. |
| Data integrity is measured with algorithms like SHA, SHA-2, SHA-256. | Data integrity is measured with the message digest and added to encrypted data before the data is sent. |
| More complex to configure and requires setup for secure shell access. | Relatively easier to implement for secure web browsing and e-commerce. |
| Supports port forwarding (SSH tunneling) for routing network traffic securely from one port to another. | Does not support native port forwarding. |
| Machine identities (keys) are self-managed, typically handled within organizations or security teams. | Digital certificates are managed by a CA, providing a more centralized system for identity verification. |
| Common in internal, secure networks for IT and network administration tasks. | Common for external-facing applications and websites to secure user data. |
Similarities Between SSH and SSL/TLS
It’s understandable that someone might get SSH and SSL confused since both are three-letter abbreviations that start with the same letter. But there are other similarities beyond their names. Firstly, both protocols are used to secure connections. They rely on encryption to protect data that passes between two network devices which prevents unauthorized access.
Authentication
The purpose of both types of protocols is to create reliable and secure connections. They achieve this by implementing authentication mechanisms to ensure that only authorized users or devices can access the network or server.
PKI
Both protocols are built around Public Key Infrastructure (PKI), using digital certificates and encryption keys to establish secure communications. They also share flexibility that allows them to extend beyond their primary purposes — SSH can support secure file transfers, and SSL/TLS can secure email communication and other non-web-based applications.
Security
SSH and SSL protocols are designed to provide a high level of security. Both of the protocols use authentication mechanisms and encryption, which protects with tampering and security threats.
Flexibility
Both of the protocols are flexible, and they can be used for multiple things. Like, SSH can be used for secure file transfer and remote administration. On the other hand, SSL can be used for secure email communication or non-web-based applications.
Without these two mechanisms, we would not have the security necessary to conduct business on the internet that we have today.
Conclusion
While SSH and SSL/TLS may seem similar due to their roles in creating secure connections, they serve very different purposes. SSH is primarily a tool for technicians. It allows secure login to remote machines to issue commands, manipulate files, and manage databases. On the other hand, SSL/TLS is a mechanism to encrypt the data exchanged between a website’s visitors and server. It ensures that sensitive information – such as credit card details and passwords – remains protected from man-in-the-middle attacks.
Of course, these two are not mutually exclusive. SSH may use SSL/TLS as part of its secure solution. There are a variety of possible implementations for these versatile protocols. They are necessary these days with all the online threats that we face. It’s another reminder that we all need to be careful and vigilant when using online resources.
Related Post: