The advent of technology has seen most of us placing our confidence in online transactions and storing sensitive information on the cloud. And anything that you place on the world wide web runs the risk of getting hacked. Cybercriminals are always on the prowl and track down unsuspecting business and force their way through unauthorized access. While there are safeguards in place but are they enough? We still here about numerous incidents of data breach every year. Any such event comes with huge costs, including loss of trust, lost sales, lawsuits, severe penalties, and fines from regulators. The advent of quantum computing will provide a more authentic layer of security and prevent hackers from gaining access to your sensitive data.
How can Quantum Computing be used for Cryptography?
Quantum computing was expected to work like supercomputers and solve some of the complex challenges related to cybersecurity. Of late, there has been an impetus in quantum computing with Google and IBM leading the way with IBM introducing the IBM Q System One – a circuit-based quantum computer.
The procedures are always updating with the engineers and scientists working to improve the methods of computing and use across multiple industries. Quantum computing can allow computations to be run very fast and uses the properties of quantum objects. The traditional computational methods have utilized binary gates based on the digits 0 and 1.
Cybersecurity practices rely mostly on public-key cryptography and encryption. The techniques use mathematical algorithms that cannot be easily broken. According to Digicert, around 71% of the respondents to research, mentioned that they were aware that quantum computing would be a risk in the future. When huge quantum computers are built, they can impact algorithms used in cryptography. Using an algorithm called unstructured quantum search, the quantum computers can break into the public key systems within a short time.
Quantum cryptography algorithms can be used across various applications – both scientific and business. There are few areas of cryptography that can handle quantum mechanical techniques. These are key distribution and random number generation.
Random Number Generation
Most of the incidents happening around us are not random and can be predicted if there is suitable data. However, are you aware that the quantum process is random in the real sense? Whatever be your computing power, you will be unable to predict what their values could be. There is various sensitive information that must be protected by cryptographic processes. A random process provides passwords, and it is not easy to demonstrate the effectiveness of the software’s process. Gradually there would be several ways to generate random passwords using quantum mechanics like radioactive decay and tunnelling.
Key Distribution
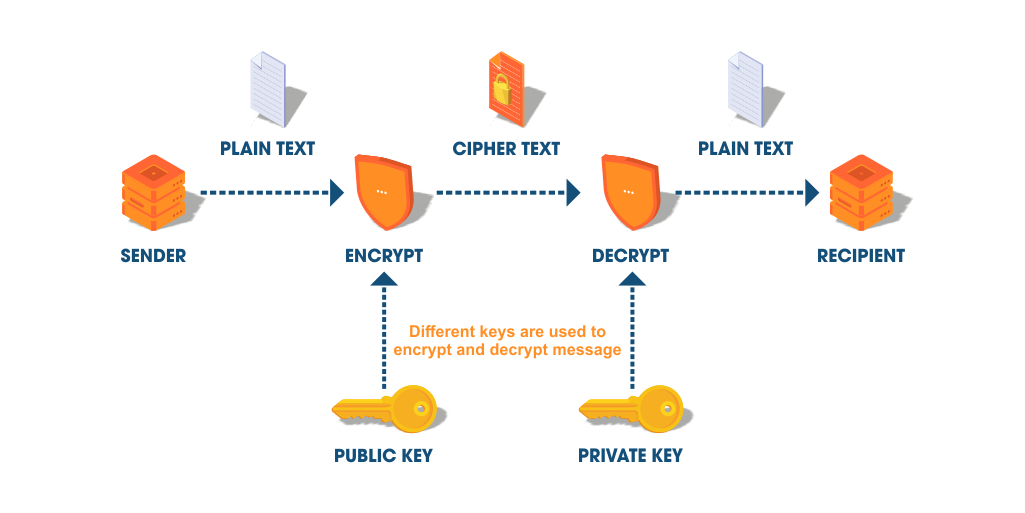
One of the secure ways of communication is to generate a pair of public and private keys. The sender and the recipient can register the pair of keys and register the public key with the Certification Authority. The Certification Authority creates the certificate for the public key and distributes it with the recipient. Then they need to match the private key with the public key of the other end and protect their communication.
Public key cryptography is a useful way to protect the password, and it would not be feasible for a cybercriminal to obtain the private key using the available public key. Researchers are nevertheless looking out for better alternatives.
What is Quantum Cryptography?
Let us first understand what cryptography is. It is the set of processes undertaken to convert plain text into an encrypted text that only authorized personnel with a key will be able to unlock and decipher. Quantum cryptography follows a set of procedures related to quantum mechanics so that none other than the expected recipient of the information can understand. The phenomenon works such that it cannot be interrupted unknowingly. It is due to the multiple states of the quantum theory. You will need a heavy-duty computer to help in the encryption and decryption of the data.
The use of quantum computers is not without risk as it can decrypt the asymmetric and symmetric keys. The initial target of quantum computers was the asymmetric encryption. There were two keys whereby the recipient would decrypt the information using the matching key. The symmetric encryption mechanism used only one key that made its use for communication unsafe. It was, on the contrary, more difficult to break.
However, using symmetric keys would require doubling the required activity for every additional bit. As a result, you may need to have larger keys. However, quantum computers can still cut the length of the string. While longer keys are suitable for a primary defence mechanism, symmetric encryption was another option. The longer keys made encryption expensive, and the encryption itself became slower, in the quantum computational model, the basic unit of information is the qubit.
Quantum cryptography is also based on the Heisenberg Uncertainty Principle. The principle states that the measured position cannot be ascertained with precision and any particle’s momentum. Over time, the principle has been generalized to include various pairs known as conjugate variables. In layman’s terms, the more correctly you know about one variable, the more uncertain you are about the other.
What is Post Quantum Cryptography?
As technology tries to find out newer algorithms to ensure cryptography is foolproof; there is constant research to improve the current algorithms. It has been seen that quantum computing can crack the 2048-bit RSA system very quickly. It is where the post-quantum cryptography algorithms come in! They are known to be safer against quantum computers. It is expected that these algorithms use complex functions that even Shor’s algorithm cannot crack.
It must be borne in mind that the newer algorithms must be in sync with the protocols running currently, like TLS. It must also consider the signatures and size of the encryption keys. The time is taken to encrypt, and decrypt communication messages and the time needed to verify signatures etc. should be considered. The amount of traffic is also a significant factor.
Currently, researchers are developing algorithms based on advanced mathematical models to strengthen public-key infrastructure against future quantum attacks. This urgency stems from the anticipation that quantum computers will eventually break algorithms that are considered safe today. The challenge is that post-quantum cryptography often requires larger keys and produces bigger signatures, which can affect performance. At the same time, the threat of Harvest Now, Decrypt Later highlights why these efforts cannot be delayed. Attackers may already be stockpiling encrypted data to exploit once quantum decryption becomes possible.
While quantum computing could take a few years; work has started to upgrade the current algorithms. Now, as government and private businesses have systems that could run for decades, the need to improve the cryptographic algorithms are enormous. One of the organizations leading the research is the US National Institute of Standards and Technology (NIST). They are in the process of shortlisting algorithms that could help in the future. But experts feel they are years away from coming.
There are advanced functions like the lattice-based cryptography and the supersingular isogeny key exchange. The lattice-based cryptography utilizes mathematical equations like lattices and can create several cryptographic tools and schemes. The supersingular isogeny key exchange is also known as supersingular isogeny Diffie-Hellmann key exchange (SIDH). It is an algorithm that allows two parties, who have no prior knowledge of the other, to set up a secret key over an insecure channel. The SIDH utilizes 2688-bit public keys at a 128-bit quantum level. It is among the smallest ones too!
Standardizing post-quantum cryptographic algorithms
The NIST and numerous other organizations are currently devoting their work to standardizing public-key encryption and key-establishment algorithms. The NIST is working on stateless quantum-resistant signatures. Once the new algorithms get standardized, they will be tagged with the various security protocols. The NIST is currently undertaking the process of choosing a standard for the post-quantum cryptographic algorithm. In 2019, the NIST had selected 26 promising algorithms that would be evaluated and tested. They are planning to have the final one ready by 2022 and release it for public comment.
The best way to start preparing is to ensure that all current and future systems have cryptographic agility — the ability to be easily reconfigured to add quantum-resistant algorithms
—Brian LaMacchia, Head of the Security and Cryptography Group, Microsoft Research
The IETF crypto forum has standardized two hash-based algorithms, viz. XMSS and LMS. They are among the ones that could be considered for firmware updates.
Types of Post Quantum Algorithms
Lattices
They are the most studied and flexible. The lattices algorithm can support digital signatures and key exchanges and is capable of sophisticated encryption models too. The foundation is based on linear algebra, despite the need for complex mathematical processes for security proofs and optimization.
Among the different lattice-based algorithms being considered for the NIST standards are Kyber and Dilithium. The Kyber is a key-encapsulation mechanism that uses the algebraic number theory for better performance. Dilithium is a scheme based on the digital signature, and its performance has been very high.
Isogenies
Isogenies use the Diffie-Hellman type protocol as part of the elliptic-curve cryptography. An isogeny is a function that transforms one elliptic curve into another with the group structure of the first is reflected in the second. It is sort of a group homomorphism with an added structure dealing with the geometry of each curve. The secret keys are a chain of isogenies while the public keys are the curves.
Advantage of quantum key distribution
The Quantum Key Distribution (QKD) is an example of Quantum Cryptography. It transfers information by using photons instead of the usual method of using bits. Entities can take advantage of the attribute of photons that they cannot be cloned or changed in any way. Hence the information exchanged between two parties can be kept secure.
QKD uses the principles of quantum mechanics to ensure the communication is secure without any chances of allowing any unauthorized access. The QKD principle is bound to see its use in a highly sensitive exchange of information. The communicating entities must be located at a fixed place. It means that it will mainly be used in government, military, and financial services industries where there is a significant exchange of sensitive information.
QKD uses a feature through which if there is any attempt to break into the communication with authorization, the photon will change its state. The key will fail, only to alert the two entities about the incident. Thus, QKD provides a secure channel of communication. It uses a One-Time Pad (OTP) encryption that provides the keys as long as the data to be encrypted. The OTP can be used only once.
The Post Quantum Cryptography (PWC) can be used for standard commercial applications where the cost of the system and mobility ranks supreme. It can use the same hardware infrastructure use by the current networks. The risk with PQC is that there is a small possibility that any new algorithm could break into it forcibly. Still, the market for PQC is enormous. According to a report by Inside Quantum Technology, there would be a market of US$ 9.5 billion by 2029.
Conclusion
There has been a significant increase in the number of cyberattacks attempted every day. The number of successful data breaches also does not seem to go down. Studies suggest that entities need to be on their guard against as much as possible. There has been constant research on how to improve upon the prevalent cryptographic algorithms. The risk has grown manifold after Peter Shor came up with his paper that showed that quantum computers could break into the encryption algorithms currently in use. What gives us solace in the research being undertaken to improve the current algorithms.
While the search for advanced algorithms is needed; we must also identify the areas that are most vulnerable to cyberattacks and try to plug them. The cryptographic algorithm used for digital signatures and take care of the initial SSL/ TLS handshake needs to be addressed. As of now, the symmetric algorithms are resistant to attacks from quantum computers.
Related Article: