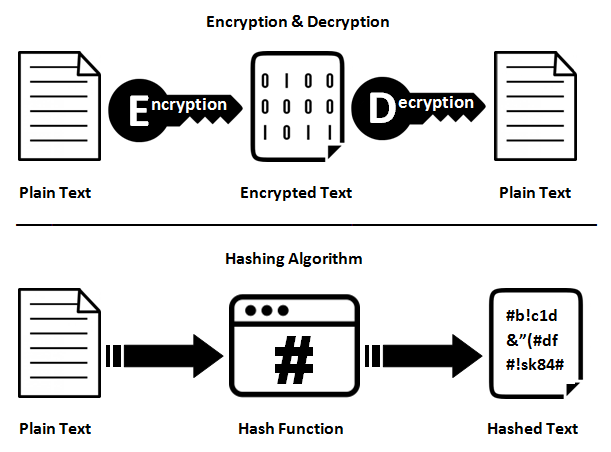
Hashing and Encryption have different functions. Encryption includes encryption and decryption process while hashing is a one-way process that changes data into the message digest which is irreversible.
Security and efficiency are two very important parameters in communication systems and you must have heard of the terms. Encryption and Hashing as far as data and computing concerned. Regardless, these two computing terms that can be confusing to many, but this article looks to dispel any confusion by giving a complete overview of the two.
Hashing algorithm
A hash can simply be defined as a number generated from a string of text. Other literature can also call it a message digest. In essence, a hash is smaller than the text that produces it. It is generated in a way that a similar hash with the same value cannot be produced by another text. From this definition, it can be seen that hashing is the process of producing hash values for the purpose of accessing data and for security reasons in communication systems. In principle, hashing will take arbitrary input and produce a string with a fixed length. As a rule of the thumb, hashing will have the following attributes:
- A given known input must always produce one known output.
- Once hashing has been done, it should be impossible to go from the output to the input.
- Different multiple inputs should give a different output.
- Modifying an input should mean a change in the hash.
A hash algorithm is a function that can be used to map out data of random size to data of fixed size. Hash values, hash codes and hash sums are returned by functions during hashing. These are different types of hashing algorithms used in computing, but some have been discarded over time. Some examples are given below:
- MD4 – It is a hash function created by Ronald Rivest in 1990. It has a length of 128 bits and has influenced many posterior designs like WMD5, WRIPEMD and WSHA family. The security of this algorithm has however been criticized even by the creator himself.
- SHA algorithm – Secure Hash Algorithm was designed by the National Security Agency to be used in their digital signature algorithm. It has a length of 160 bits. Just like the latter, security weaknesses in it means that it is no longer used SHA and SHA-1, organizations are using strong SHA-2 (256 bit) algorithm for the cryptographic purpose. (How to move from SHA1 to SHA2 algorithm?)
- RIPMEND – It is a cryptographic hash algorithm designed by Hans Dobbertin. It has a length of 160 bits. It was developed in the framework of the EU project RIPE.
- WHIRLPOOL algorithm – It is algorithm design by Vincent Rijmen and Paul Barreto. It has a length of 2256 bits and produces the 512-bit message digest.
- TIGER algorithm – It is a new and fast algorithm. It used by modern computers. It hashes more than 132M bits per second. It has thus far proved to be more efficient than all the hashing algorithms discussed. It has no restrictions on its usage that means it has no patents.
Purpose of hashing
- Hashing can be used to compare a large amount of data. Hash values can be created for different data, meaning that it is easier comparing hashes than the data itself.
- It is easy to find a record when the data is hashed.
- Hashing algorithms are used in cryptographic applications like a digital signature.
- Hashing is used to generate random strings to avoid duplication of data stored in databases.
- Geometric hashing – widely used in computer graphics to find closet pairs and proximity problems in planes. It is also called grid method and it has also been adopted in telecommunications.
These characteristics mean that hash can be used to store passwords. This way, it becomes difficult for someone who has the raw data to reverse them.
Encryption
Encryption is the process of encoding simple text and other information that can be accessed by the sole authorized entity if it has a decryption key. It will protect your sensitive data from being accessed by cybercriminals. It is the most effective way of achieving data security in modern communication systems. In order for the receiver to read an encrypted message, he/she should have a password or a security key that is used in decryption. Data that has not been encrypted is known as plain text while encrypting data is known as a cipher text. There are a number of encryption systems, where an asymmetric encryption is also known as public-key encryption, symmetric encryption and hybrid encryption are the most common.
- Symmetric encryption – Uses the same secret key to encrypt and decrypt the message. The secret key can be a word, a number or a string of random letters. Both the sender and the receiver should have the key. It is the oldest technique of encryption.
- Asymmetric encryption – It deploys two keys, a public key known by everyone and a private key known only by the receiver. The public key is used to encrypt the message and a private key is used to decrypt it. Asymmetric encryption is little slower than symmetric encryption and consumes more processing power when encrypting data.
- Hybrid encryption – It is a process of encryption that blends both symmetric and asymmetric encryption. It takes advantage of the strengths of the two encryptions and minimizes their weakness.
Purpose of encryption
The main idea of encryption is to protect data from an unauthorized person who wants to read or get information from a message that was not intended for them. Encryption enhances security when sending messages through the Internet or through any given network. The following are key elements of security that encryption helps to enhance.
- Confidentiality – Encrypted message cannot be read or changed by another person.
- Encrypt – It transforms data in such a way that only specific individuals can transform the message.
- Granular access control – Users are limited to what they can see and do.
- It makes auditing for accountability easy. In the case of message leaked, it is easy to trace who did that and when thus security breaches can be sorted out efficiently.
- Authentication – the origin of the message received can be traced thus facilitating authentication.
Some of the most popular encryption algorithms are AES and PGP. AES is a symmetric encryption algorithm while PGP is an example of an asymmetric encryption algorithm used today.
The difference between hashing and encryption
Hashing is used to validate the integrity of the content by detecting all modifications and thereafter changes to a hash output. Encryption encodes data for the primary purpose of maintaining data confidentiality and security. It requires a private key to reversible function encrypted text to plain text.
In short, encryption is a two-way function that includes encryption and decryption whilst hashing is a one-way function that changes a plain text to a unique digest that is irreversible.
Hashing and encryption are different but also have some similarities. They are both ideal in handling data, messages, and information in computing systems. They both transform or change data into a different format. While encryption is reversible, hashing is not. Future improvements are very crucial given that attackers keep changing tactics. This implies that an up-to-date way of hashing and encrypting is more palatable in modern computing systems.
Do you want your website to be encrypted?
To encrypt transmitted information over the website, you need to obtain an SSL certificate as per your needs. Once you installed the certificate on your desired server, all communication between the web browser and the web server will be encrypted.